Ransomware Profitability
Schneier on Security
FEBRUARY 10, 2021
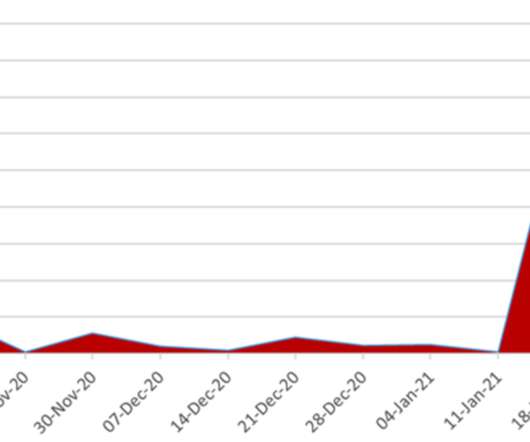
Analyzing cryptocurrency data, a research group has estimated a lower-bound on 2020 ransomware revenue: $350 million, four times more than in 2019. Based on the company’s data, among last year’s top earners, there were groups like Ryuk, Maze (now-defunct), Doppelpaymer, Netwalker ( disrupted by authorities ), Conti, and REvil (aka Sodinokibi).





































Let's personalize your content