Critical Vulnerability in Open SSL
Schneier on Security
OCTOBER 28, 2022
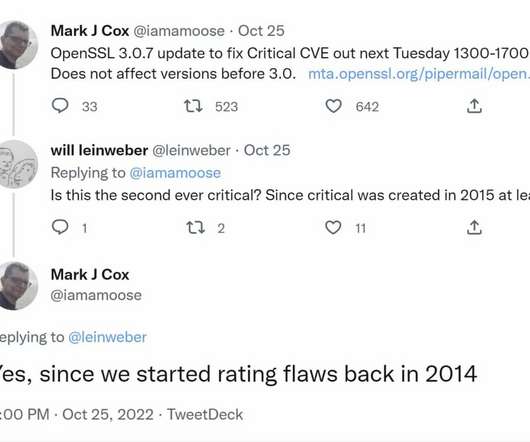
There are no details yet, but it’s really important that you patch Open SSL 3.x when the new version comes out on Tuesday. How bad is “Critical”? According to OpenSSL, an issue of critical severity affects common configurations and is also likely exploitable. It’s likely to be abused to disclose server memory contents, and potentially reveal user details, and could be easily exploited remotely to compromise server private keys or execute code execute remotely.








































Let's personalize your content