How the SolarWinds Hackers Bypassed Duo’s Multi-Factor Authentication
Schneier on Security
DECEMBER 15, 2020
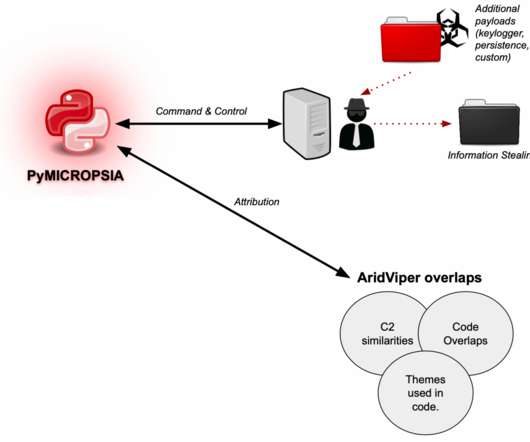
This is interesting : Toward the end of the second incident that Volexity worked involving Dark Halo, the actor was observed accessing the e-mail account of a user via OWA. This was unexpected for a few reasons, not least of which was the targeted mailbox was protected by MFA. Logs from the Exchange server showed that the attacker provided username and password authentication like normal but were not challenged for a second factor through Duo.









































Let's personalize your content