Use these settings in Microsoft Azure Active Directory to take control of user-requested OAuth access permissions.

Recently Malwarebytes reported that the SolarWinds hackers accessed its internal emails using the same intrusion vector they used in other attacks. The vector appears to abuse applications with privileged access to Microsoft Office 365 and Azure environments. The representative stated that “the investigation indicated the attackers leveraged a dormant email protection product within our Office 365 tenant that allowed access to a limited subset of internal company emails.” The attack sequence suggests that the attacker tricked an end user into authorizing a third-party site to share authentication via OAuth.
OAuth 2.0 is an open standard for token-based authentication and authorization that allows the application to obtain authorization without exposing users’ passwords directly. Making this linked connection can inadvertently authorize a third-party product to have more rights than you intend. It’s one reason why I recommend to always set your OAuth settings so that you, the administrator, must approve access or at a minimum monitor these approvals.
How attackers exploit OAuth
The attack sequence starts with a phishing email that lures the user to click on a link or approve an action. This simple action enables the attacker to read the user’s emails and contact information at a minimum. In reported attacks the OAuth access token is typically made to mimic the branding of the target company so that users are less suspicious. The user is then prompted with screen that grants limited access to the resources.
Attackers build phishing lures that use a cloud service that will launch a specific OAuth authorization request link. By getting the user to click to approve the rights, the attacker can act as that user throughout the entire ecosystem where OAuth is used. Adding multi-factor authentication will not prevent these attacks. You need to add policies for reviewing for certain activities and anomaly actions.
Preventing OAuth-based attacks
First, determine how your organization uses third-party OAuth 2.0 applications. Is it limited in scope or by need to where you can easily add the mandate of administrator approval of adding user approval? If your application process is limited, I strongly recommend using the most restrictive setting that all OAuth use must be approved by an administrator before a user can add access to an application.
The MITRE attack techniques used in these observed attacks include using a trusted relationship with Office 365 as well as using the steal access token technique. You can monitor and set alerts for these issues in several ways.
First, set up administrator consent to applications. Microsoft has added a middle ground for consent. Instead of the two extremes of “Do not allow user consent”, which blocks everything, and “Allow user consent for apps”, which allows everything, Microsoft added a third option: “Allow user consent for apps from verified publishers, from selected permissions”. This selection allows users to use Azure Active Directory credentials to sign into third-party applications, but it still requires admin consent for applications that attempt to read data from your cloud assets. You can even create a custom application consent policy.
To set this up, sign into the Azure Portal as a global administrator. Select in order:
- “Azure Active Directory”
- “Enterprise applications”
- “Consent and permissions”
- “User consent settings”
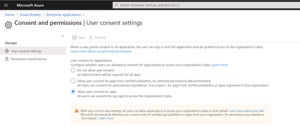
Under “User consent for applications”, select the consent settings you’d like for all users.
 Susan Bradley
Susan BradleySelect user consent settings
The default setting for Microsoft 365 is to allow user consent for apps. As even Microsoft points out on its settings page, all users can allow applications to access your organization’s data on their behalf. Microsoft recommends using the middle setting, allowing user consent for apps from verified publishers.
 Susan Bradley
Susan BradleyChoose verified publishers
Here’s how to set up an admin consent workflow:
- Sign into the Azure Portal as a global administrator.
- Click on “All services” at the top navigation menu on the left to open the Azure Active Directory Extension.
- In the filter search box, type “Azure Active Directory”.
- Select the Azure Active Directory item from your search process.
- From the navigation menu, select “Enterprise applications”.
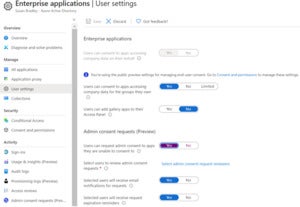
- Under “Manage”, select “User settings”.
- Under “Admin consent requests (preview)”, set “Users can request admin consent to apps they are unable to consent to” to “Yes”.
 Susan Bradley
Susan BradleySet up admin consents
Now configure the following settings:
- Select who will review admin consent requests. These users should be global administrators and have cloud application administrator and application administrator roles. Enable or disable email notifications to the selected reviewers when a request is made by choosing the selected users.
- Enable reminder email notifications to the reviewers when a request is about to expire.
- Set the time limit for how long a consent request can stay valid.
Your users will ask for permission and press a button to request approval. The approval request will be sent to the designated reviewers for approval. The reviewer will have the choice to approve the request, deny the request or block the request as needed.
If you have Microsoft Defender for Office, you should receive an alert that a suspicious OAuth app permission was granted. Follow up and review any such alerts. If your tenant has not already done so, disable automatic forwarding in Office 365. This is a recent new default in Microsoft 365 settings. Microsoft has realized attackers often use automatic forwarding, so 365 now blocks it by default.
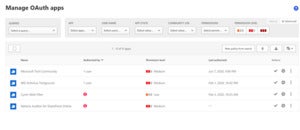
If you have a license for Cloud App Security you can go even farther and investigate risky cloud applications. In the portal, go to “Investigate” and then “OAuth apps”. Review what applications have connected to your domain and what permissions they have in your environment.
 Susan Bradley
Susan BradleyInvestigate OAuth connections
Attackers often know how to attack your systems better than you know how to protect them. Take the time to investigate the common attack techniques that are being used in targeted cloud attacks. Ensure that you set up your cloud applications to be protected from the start. Setting the proper alerts and permissions for OAuth applications is a key way to keep your network safe and secure.










