Fugitive Identified on YouTube By His Distinctive Tattoos
Schneier on Security
APRIL 1, 2021
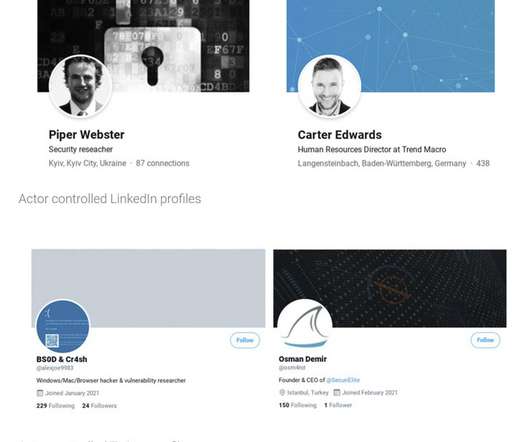
A mafia fugitive hiding out in the Dominican Republic was arrested when investigators found his YouTube cooking channel and identified him by his distinctive arm tattoos.







































Let's personalize your content