Why Windows 11's security is such a big deal
Tech Republic Security
OCTOBER 5, 2021
Enterprises are worried about exactly the issues that Windows 11 helps with, and the hardware specs mean future security improvements like more app containers.

Tech Republic Security
OCTOBER 5, 2021
Enterprises are worried about exactly the issues that Windows 11 helps with, and the hardware specs mean future security improvements like more app containers.

Security Boulevard
OCTOBER 5, 2021
Hackers broke into the massive telephony interconnection service run by Syniverse—a huge, yet invisible, chunk of infrastructure. The post Syniverse Hack: Billions of Users’ Data Leaks Over Five Years appeared first on Security Boulevard.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Tech Republic Security
OCTOBER 5, 2021
Throughout the summer of 2021, the number of phishing URLs designed to impersonate Chase jumped by 300%, says security firm Cyren.

We Live Security
OCTOBER 5, 2021
ESET research discovers a previously undocumented UEFI bootkit with roots going back all the way to at least 2012. The post UEFI threats moving to the ESP: Introducing ESPecter bootkit appeared first on WeLiveSecurity.

Advertisement
How many people would you trust with your house keys? Chances are, you have a handful of trusted friends and family members who have an emergency copy, but you definitely wouldn’t hand those out too freely. You have stuff that’s worth protecting—and the more people that have access to your belongings, the higher the odds that something will go missing.

Tech Republic Security
OCTOBER 5, 2021
Free for the first 60 days, the new service is designed to help you better understand your organization's exposure to ransomware and automate the steps needed to reduce your risk.

Bleeping Computer
OCTOBER 5, 2021
A newly discovered and previously undocumented UEFI (Unified Extensible Firmware Interface) bootkit has been used by attackers to backdoor Windows systems by hijacking the Windows Boot Manager since at least 2012. [.].
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.

Bleeping Computer
OCTOBER 5, 2021
The Apache Software Foundation has released version 2.4.50 of the HTTP Web Server to address two vulnerabilities, one of which is an actively exploited path traversal and file disclosure flaw. [.].

CSO Magazine
OCTOBER 5, 2021
One boring day during the pandemic, security researcher Craig Hays decided to do an experiment. He wanted to leak an SSH username and password into a GitHub repository and see if any attacker might find it. Hays thought he'd have to wait a few days, maybe a week, before anyone noticed it. Reality proved more brutal. The first unauthorized login happened within 34 minutes.
Bleeping Computer
OCTOBER 5, 2021
'The Telegraph', one of UK's largest newspapers and online media outlets, has leaked 10 TB of data after failing to properly secure one of its databases. [.].

CyberSecurity Insiders
OCTOBER 5, 2021
Interpol, the internationally recognized crime prevention agency, has announced an online campaign that will help individuals and companies protect their networks from state funded cyber attack campaigns. Cybersecurity Awareness Program by Interpol will start on October 4th, 2021 and will end on October 22nd, 2021, and will only be driven through social media.

Advertiser: Revenera
In a recent study, IDC found that 64% of organizations said they were already using open source in software development with a further 25% planning to in the next year. Most organizations are unaware of just how much open-source code is used and underestimate their dependency on it. As enterprises grow the use of open-source software, they face a new challenge: understanding the scope of open-source software that's being used throughout the organization and the corresponding exposure.

Security Boulevard
OCTOBER 5, 2021
Security professionals work hard to plan secure IT environments for organizations, but the developers who are tasked with implementing and carrying these plans and procedures are often left out of security planning processes, creating a fractured relationship between development and security. This was the conclusion from a VMware and Forrester study of 1,475 IT and.
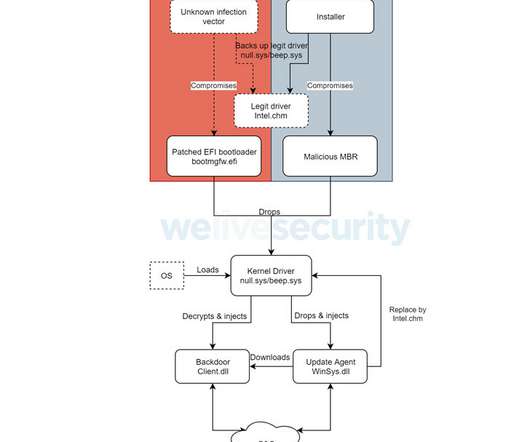
The Hacker News
OCTOBER 5, 2021
Cybersecurity researchers on Tuesday revealed details of a previously undocumented UEFI (Unified Extensible Firmware Interface) bootkit that has been put to use by threat actors to backdoor Windows systems as early as 2012 by modifying a legitimate Windows Boot Manager binary to achieve persistence, once again demonstrating how technology meant to secure the environment prior to loading the

CyberSecurity Insiders
OCTOBER 5, 2021
On September 11th, 2001 Taliban linked terrorist group launched a flight attack on the twin towers of United States that from then-on put a major dent in the US governance on an international note. In retaliation, in December 2001, UK and US launched a major military attack on Taliban nationals and took control of the entire Afghan nation for almost 20 years.

Malwarebytes
OCTOBER 5, 2021
Windows 11, the latest operating system (OS) from Microsoft, launches today, and organizations have begun asking themselves when and if they should upgrade from Windows 10 or older versions. The requirements and considerations of each organization will be different, and many things will inform the decisions they make about whether to stick or twist.

Advertisement
Within the past few years, ransomware attacks have turned to critical infrastructure, healthcare, and government entities. Attackers have taken advantage of the rapid shift to remote work and new technologies. Add to that hacktivism due to global conflicts and U.S. elections, and an increased focus on AI, and you have the perfect recipe for a knotty and turbulent 2024.

CSO Magazine
OCTOBER 5, 2021
Throughout National Insider Threat Awareness Month there has been no shortage of thoughts and ideas proffered on how to manage and mitigate insider risk that comes with having humans as part of the ecosystem. It’s true, the human is both the strength and the weakness. They are called upon to mitigate the risk and ameliorate the actions of the malevolent or careless employee.

eSecurity Planet
OCTOBER 5, 2021
Spending money you hadn’t budgeted to hire experts to clean up an unexpected mess is at the bottom of every manager’s wish list, but in the case of a cyber attack as damaging as ransomware , turning incident response over to a pro may be the best thing you can do. Let’s examine five key reasons to pay an expert to help recover from ransomware: Contractual obligations.

The Hacker News
OCTOBER 5, 2021
Apache has issued patches to address two security vulnerabilities, including a path traversal and file disclosure flaw in its HTTP server that it said is being actively exploited in the wild. "A flaw was found in a change made to path normalization in Apache HTTP Server 2.4.49.

CSO Magazine
OCTOBER 5, 2021
One Identity has acquired OneLogin, an IAM (identity and access management) provider, in a bid to offer its customers an end-to-end suite of security applications that offer identity correlation, secured access to critical assets, and real-time visibility into suspicious login activity. One Identity, which is owned by Quest Software, has up to now provided PAM (privileged access management), IGA (identity governance and administration), and ADMS (active directory management and security) applica

Advertisement
The healthcare industry has massively adopted web tracking tools, including pixels and trackers. Tracking tools on user-authenticated and unauthenticated web pages can access personal health information (PHI) such as IP addresses, medical record numbers, home and email addresses, appointment dates, or other info provided by users on pages and thus can violate HIPAA Rules that govern the Use of Online Tracking Technologies by HIPAA Covered Entities and Business Associates.

Bleeping Computer
OCTOBER 5, 2021
Operators of an unknown ransomware gang are using a Python script to encrypt virtual machines hosted on VMware ESXi servers. [.].

Quick Heal Antivirus
OCTOBER 5, 2021
Microsoft has released an all-new Windows 11 Operating System (OS). This article highlights the new features in Windows. The post Update – All Quick Heal products are compatible with Windows 11 appeared first on Quick Heal Blog | Latest computer security news, tips, and advice.

Bleeping Computer
OCTOBER 5, 2021
Google announced today that they plan on auto-enrolling 150 million accounts into two-factor authentication by the end of 2021. [.].

TrustArc
OCTOBER 5, 2021
The ICO’s Data Sharing Code of Practice comes into force on 5 October 2021. It was laid before Parliament on 18 May 2021 and issued on 14 September 2021 under the DPA (Data Protection Act) 2018. Its goal is to enable responsible data sharing by setting up best practices. How to achieve responsible data sharing? […].

Advertisement
The losses companies suffered in 2023 ransomware attacks increased by 74% compared to those of the previous year, according to new data from the Federal Bureau of Investigation (FBI). The true figure is likely to be even higher, though, as many identity theft and phishing attacks go unreported. Ransomware attackers can potentially paralyze not just private sector organizations but also healthcare facilities, schools, and entire police departments.

Security Boulevard
OCTOBER 5, 2021
Qualys today launched a Ransomware Risk Assessment Service through which organizations can proactively identify, prioritize, track and ultimately remediate assets that are vulnerable to ransomware attacks. Sumedh Thakar, Qualys CEO, said the service leverages the vulnerability discovery capabilities at the core of the Qualys vulnerability management, detection and response (VMDR) platform to specifically pinpoint vulnerabilities.

Tech Republic Security
OCTOBER 5, 2021
Jack Wallen dispenses his bi-annual advice to Android users on how to avoid falling prey to malicious apps and bad actors.

Heimadal Security
OCTOBER 5, 2021
Atlassian Confluence is a highly popular web-based team workspace meant to help employees collaborate. Back in August, Atlassian issued security updates meant to patch a Confluence remote code execution (RCE) vulnerability tracked as CVE-2021-26084 that was being exploited in the wild. If this vulnerability is successfully exploited, any unauthenticated attacker can remotely execute instructions on unpatched systems. […].

Bleeping Computer
OCTOBER 5, 2021
Facebook says that yesterday's worldwide outage was caused by faulty configuration changes made to its backbone routers that brought all its services to a halt. [.].

Speaker: Blackberry, OSS Consultants, & Revenera
Software is complex, which makes threats to the software supply chain more real every day. 64% of organizations have been impacted by a software supply chain attack and 60% of data breaches are due to unpatched software vulnerabilities. In the U.S. alone, cyber losses totaled $10.3 billion in 2022. All of these stats beg the question, “Do you know what’s in your software?

Security Boulevard
OCTOBER 5, 2021
As 2021 progressed through the second quarter and into the third, cybercriminals introduced new—and updated—threats and tactics in campaigns targeting prominent sectors, McAfee’s October 2021 Advanced Threat Research Report found. The report called the second quarter of 2021 a “vibrant quarter” for ransomware, earning its place as a high-profile cybersecurity agenda item for the U.S.

Dark Reading
OCTOBER 5, 2021
Common vulnerabilities and exposures (CVEs) contain actionable details that can help address your security concerns. Here's how to get more from CVE data.

Security Boulevard
OCTOBER 5, 2021
In my previous post, I discussed some of the reasons why organizations decide to partner with managed service providers (MSPs). Organizations need to be careful when deciding to work with a specific provider, however, as not all MSPs are the created the same. Part of the reason why is because MSPs come in four varieties. […]… Read More. The post 4 Types of MSPs that Can Help You Meet Your Cybersecurity Needs appeared first on The State of Security.

The Hacker News
OCTOBER 5, 2021
Law enforcement agencies have announced the arrest of two "prolific ransomware operators" in Ukraine who allegedly conducted a string of targeted attacks against large industrial entities in Europe and North America since at least April 2020, marking the latest step in combating ransomware incidents.

Speaker: Erika R. Bales, Esq.
When we talk about “compliance and security," most companies want to ensure that steps are being taken to protect what they value most – people, data, real or personal property, intellectual property, digital assets, or any other number of other things - and it’s more important than ever that safeguards are in place. Let’s step back and focus on the idea that no matter how complicated the compliance and security regime, it should be able to be distilled down to a checklist.
Let's personalize your content