Contents:
Threat Actors evade security measures by creating files that are a combination of polyglot and malicious Java archive (JAR).
This way they can deploy malware without being discovered.
How Does This Work?
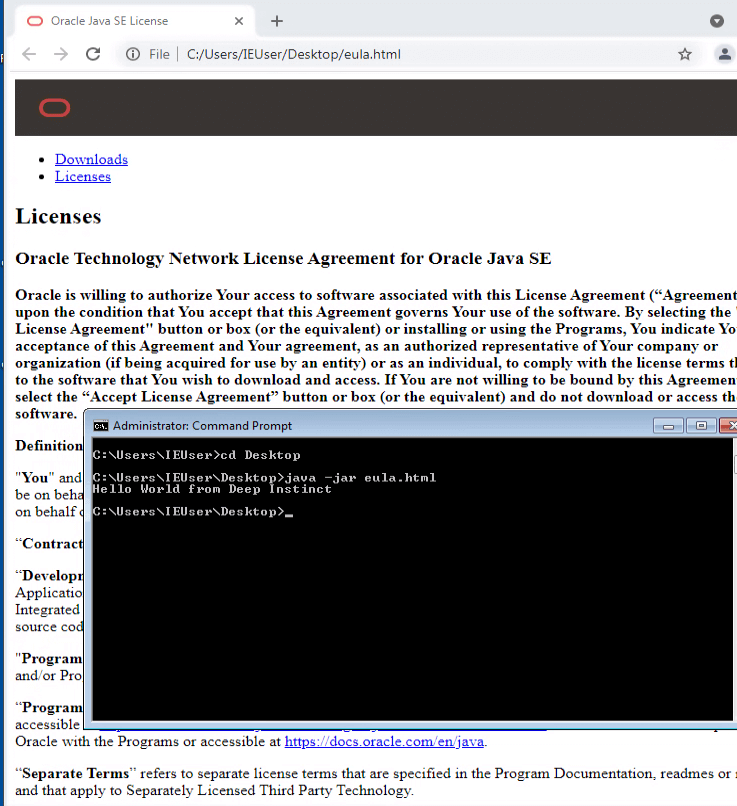
Polyglot files integrate vocabulary from two or more different formats in such a way that each format can be read without error. And a JAR file is basically a ZIP archive.
What’s special about ZIP files is that they’re identified by the presence of an end-of-central directory record which is located at the end of the archive. This means that any “junk” we append in the beginning of the file will be ignored and the archive is still valid.
This lack of validation for the JAR file enables cybercriminals to attach a malicious appended to it which will not be detected by the security software. Then the malware can be executed on the victim’s device.
2022 Campaign
Researchers at Deep Instinct discovered that remote access trojans (RATs) like StrRAT and Ratty have been deployed in a 2022 campaign using polyglot and JAR files.
One such 2022 campaign spotted by the cybersecurity firm involves the use of JAR and MSI formats – i.e., a file that’s valid both as a JAR and an MSI installer – to deploy the StrRAT payload. This also means that the file can be executed by both Windows and Java Runtime Environment (JRE) based on how it’s interpreted.
In another case were used CAB and JAR polyglots to deliver the same RATs. And the files were reproduced with the help of an URL shortening services like cutt.ly and rebrand.ly.
It is not yet clear if the samples that were analyzed are created by a single hacker or by multiple threat actors. However, the usage of the Bulgarian hosting “BelCloud LTD” has been observed in many of them, and some remote access trojans use the same command and control server.
“The proper detection for JAR files should be both static and dynamic. It’s inefficient to scan every file for the presence of an end of central directory record at the end of the file. Defenders should monitor both “java” and “javaw” processes. If such a process has “-jar” as an argument the filename passed as an argument should be treated as a JAR file regardless of the file extension or the output of the Linux “file” command”, the report concluded.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, YouTube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security









