Stealing More SRE Ideas for Your SOC
Anton on Security
DECEMBER 21, 2021
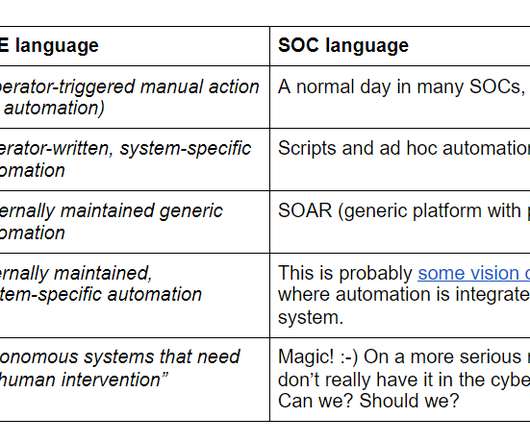
As we discussed in “Achieving Autonomic Security Operations: Reducing toil” (or it’s early version “Kill SOC Toil, Do SOC Eng” ), your Security Operations Center (SOC) can learn a lot from what IT operations learned during the SRE revolution. In this post of the series, we plan to extract the lessons for your SOC centered on another SRE principle?—?

































Let's personalize your content