Who’s Behind the NetWire Remote Access Trojan?
Krebs on Security
MARCH 9, 2023
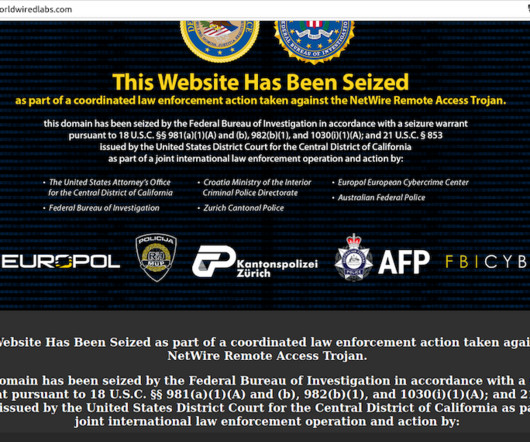
A Croatian national has been arrested for allegedly operating NetWire , a Remote Access Trojan (RAT) marketed on cybercrime forums since 2012 as a stealthy way to spy on infected systems and siphon passwords. The arrest coincided with a seizure of the NetWire sales website by the U.S. Federal Bureau of Investigation (FBI). While the defendant in this case hasn’t yet been named publicly, the NetWire website has been leaking information about the likely true identity and location of its owne







































Let's personalize your content