Bizarro Banking Trojan
Schneier on Security
MAY 20, 2021
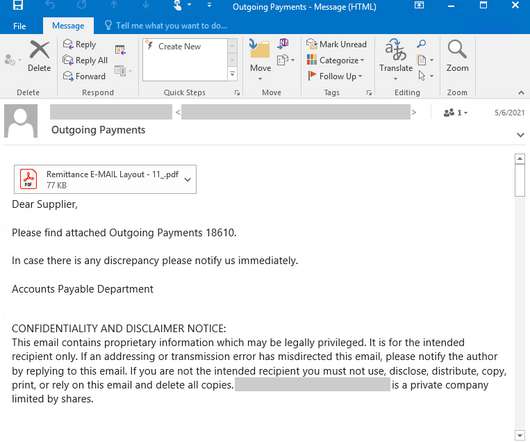
Bizarro is a new banking trojan that is stealing financial information and crypto wallets. …the program can be delivered in a couple of ways — either via malicious links contained within spam emails, or through a trojanized app. Using these sneaky methods, trojan operators will implant the malware onto a target device, where it will install a sophisticated backdoor that “contains more than 100 commands and allows the attackers to steal online banking account credentials,”





































Let's personalize your content