
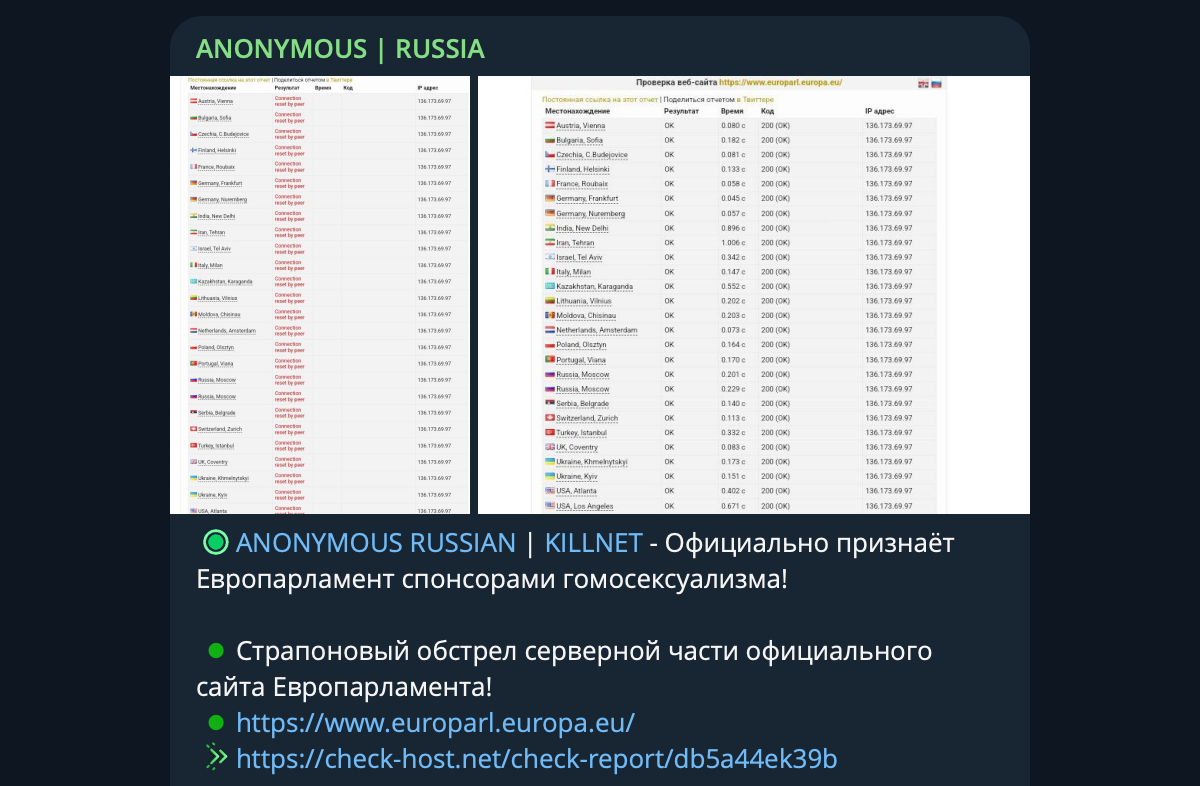
The website of the European Parliament has been taken down following a DDoS (Distributed Denial of Service) attack claimed by Anonymous Russia, part of the pro-Russian hacktivist group Killnet.
European Parliament President confirmed the incident saying that the Parliament's "IT experts are pushing back against it & protecting our systems."
The Director General for Communication and Spokesperson of the European Parliament, Jaume Dauch, also stated after the website went down that the outage was caused by an ongoing DDoS attack.
"The availability of Europarl_EN website is currently impacted from outside due to high levels of external network traffic," Dauche said.
"This traffic is related to a DDOS attack (Distributed Denial of Service) event. EP teams are working to resolve this issue as quickly as possible."
The attack came after the European Parliament recognized Russia as a state sponsor of terrorism and MEPs called for further international isolation of Russia.
The resolution was adopted on Wednesday following recent developments in Russia's war of aggression against Ukraine.
"Parliament calls on the European Union to further isolate Russia internationally, including when it comes to Russia's membership of international organisations and bodies such as the United Nations Security Council," a press release published today reads.
"MEPs also want diplomatic ties with Russia to be reduced, EU contacts with official Russian representatives to be kept to the absolute minimum and Russian state-affiliated institutions in the EU spreading propaganda around the world to be closed and banned."
Pro-Kremlin hacktivist groups have targeted European and U.S. websites since Russia invaded Ukraine. For instance, Killnet recently claimed large-scale distributed denial-of-service (DDoS) attacks targeting the websites of several major U.S. airports last month.
Notable examples of airport websites taken down following their attack include the Los Angeles International Airport (LAX), which was intermittently offline, and the Hartsfield-Jackson Atlanta International Airport (ATL), a large U.S. air traffic hub.
One week before, they attacked multiple U.S. government websites in Colorado, Kentucky, and Mississippi, with moderate success, managing to knock some of them offline for a short time.
Killnet also claimed to have taken down CISA's Protected Critical Infrastructure Information Management System website after its attacks on the U.S. Treasury in early October were thwarted before having a real effect on the agency's infrastructure.
They also previously targeted countries that sided with Ukraine, including Romania and Italy, while the Legion "sub-group" attacked key Norwegian and Lithuanian entities for similar reasons.
Earlier this month, the FBI said that DDoS attacks coordinated by pro-Russian hacktivists have a minor impact on their targets because they're attacking public-facing infrastructure like websites instead of the actual services, leading to limited disruption.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now