Cellebrite Can Break Signal
Schneier on Security
DECEMBER 21, 2020
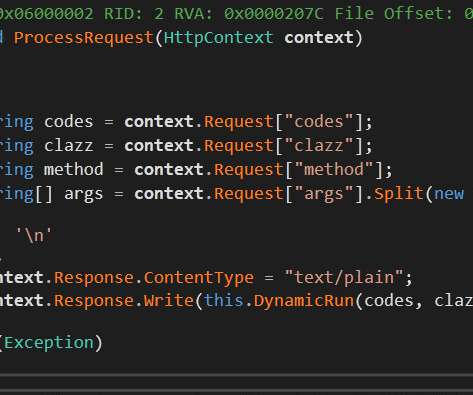
Cellebrite announced that it can break Signal. (Note that the company has heavily edited its blog post, but the original — with lots of technical details — was saved by the Wayback Machine.). News article. Slashdot post. The whole story is puzzling. Cellebrite’s details will make it easier for the Signal developers to patch the vulnerability.









































Let's personalize your content