Weekly Update 223
Troy Hunt
DECEMBER 26, 2020
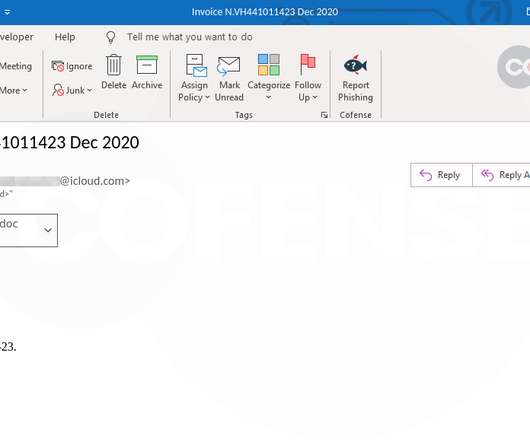
Well that's Christmas down for another year, and a rather different one it was for so many of us around the world. I'm pumping this post out very quickly (a couple of days after recording) whilst midway along a very long drive. I'll share more about that on my New Year's Day broadcast so for now, here's the Christmas Day weekly update: References Ledger customers are receiving some super nasty protection emails (makes me think of the mob charging business to make sure "nothing happens to them.










Let's personalize your content