Advice for Personal Digital Security
Schneier on Security
NOVEMBER 11, 2021
ArsTechnica’s Sean Gallagher has a two – part article on “securing your digital life.” It’s pretty good.

Schneier on Security
NOVEMBER 11, 2021
ArsTechnica’s Sean Gallagher has a two – part article on “securing your digital life.” It’s pretty good.

Tech Republic Security
NOVEMBER 11, 2021
With a bait attack, criminals try to obtain the necessary details to plan future attacks against their targets, says Barracuda.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

We Live Security
NOVEMBER 11, 2021
It’s often said that data breaches are no longer a matter of ‘if’, but ‘when’ – here’s what your organization should do, and avoid doing, in the case of a security breach. The post When the alarms go off: 10 key steps to take after a data breach appeared first on WeLiveSecurity.

Tech Republic Security
NOVEMBER 11, 2021
If you're looking for an easy command-line tool to transfer files between systems on the same LAN, Jack Wallen believes croc is the tool for the job.

Advertisement
How many people would you trust with your house keys? Chances are, you have a handful of trusted friends and family members who have an emergency copy, but you definitely wouldn’t hand those out too freely. You have stuff that’s worth protecting—and the more people that have access to your belongings, the higher the odds that something will go missing.

IT Security Guru
NOVEMBER 11, 2021
What keeps OT security specialists up at night? It’s mostly problems from the IT world, says Andy Norton, European Cyber Risk Officer at Armis. Operational technology (OT) used to be the specialist networks nobody in IT bothered with, or perhaps thought they didn’t need to. For a while, that seemed reasonable; OT networks were usually isolated from IT operations, sat behind air gaps, and ran on obscure operating systems.
Tech Republic Security
NOVEMBER 11, 2021
Receive over 100 hours of expert instruction on globally recognized cybersecurity skills that will help you become an in-demand IT professional.
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.

CSO Magazine
NOVEMBER 11, 2021
Security researchers have uncovered serious vulnerabilities in the TCP/IP stack of a real-time operating system (RTOS) called Nucleus that's used in safety-critical devices across many industry verticals. The flaws, discovered by researchers from Forescout and Medigate Labs, can lead to denial of service (DoS), information leaks and remote code execution (RCE).

Bleeping Computer
NOVEMBER 11, 2021
Hackers stayed hidden for nine months on a server holding customer information for a Queensland water supplier, illustrating the need of better cyberdefenses for critical infrastructure. [.].

CSO Magazine
NOVEMBER 11, 2021
From a cybersecurity standpoint, organizations are operating in a high-risk world. The ability to assess and manage risk has perhaps never been more important. “Having a risk management framework is essential, because risk can never be totally eliminated; it can only be effectively managed,” says Arvind Raman, CISO at telecommunications company Mitel Networks.

Tech Republic Security
NOVEMBER 11, 2021
You don't need to break the bank to get the training required for an exciting new career, especially when you've got the right coupon code.

Advertiser: Revenera
In a recent study, IDC found that 64% of organizations said they were already using open source in software development with a further 25% planning to in the next year. Most organizations are unaware of just how much open-source code is used and underestimate their dependency on it. As enterprises grow the use of open-source software, they face a new challenge: understanding the scope of open-source software that's being used throughout the organization and the corresponding exposure.

Javvad Malik
NOVEMBER 11, 2021
It’s really easy to become complacent in security when the bad guys aren’t focussing you. But when the evil eye of Cyber Sauron casts its gaze your way, you soon realise your silver bullets were only silver-plated. As lockdowns around the world ease to a degree and many organisations are welcoming staff back into the office. However, it’s not a complete return to office, and for now, it appears as if hybrid work environments are the way to go.
The Hacker News
NOVEMBER 11, 2021
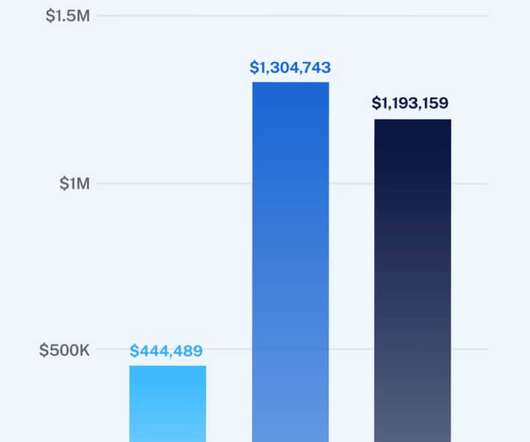
Though we are recovering from the worst pandemic, cyber threats have shown no sign of downshifting, and cybercriminals are still not short of malicious and advanced ways to achieve their goals. The Global Threat Landscape Report indicates a drastic rise in sophisticated cyberattacks targeting digital infrastructures, organizations, and individuals in 2021.
Security Affairs
NOVEMBER 11, 2021
Researchers at AT&T discovered a new BotenaGo botnet that is using thirty three exploits to target millions of routers and IoT devices. BotenaGo is a new botnet discovered by researchers at AT&T that leverages thirty three exploits to target millions of routers and IoT devices. Below is the list of exploits used by the bot: Vulnerability Affected devices CVE-2020-8515 DrayTek Vigor2960 1.3.1_Beta, Vigor3900 1.4.4_Beta, and Vigor300B 1.3.3_Beta, 1.4.2.1_Beta, and 1.4.4_Beta devices CVE-20

Graham Cluley
NOVEMBER 11, 2021
Fishing fanatics find themselves in deep water, Teslas go haywire after an update, and is there actually some good news about IoT? All this and much more is discussed in the latest edition of the award-winning "Smashing Security" podcast by computer security veterans Graham Cluley and Carole Theriault, joined this week by Ken Munro.

Advertisement
Within the past few years, ransomware attacks have turned to critical infrastructure, healthcare, and government entities. Attackers have taken advantage of the rapid shift to remote work and new technologies. Add to that hacktivism due to global conflicts and U.S. elections, and an increased focus on AI, and you have the perfect recipe for a knotty and turbulent 2024.
The Hacker News
NOVEMBER 11, 2021
Google researchers on Thursday disclosed that it found a watering hole attack in late August exploiting a now-parched zero-day in macOS operating system and targeting Hong Kong websites related to a media outlet and a prominent pro-democracy labor and political group to deliver a never-before-seen backdoor on compromised machines.

Security Boulevard
NOVEMBER 11, 2021
Each week, Sontiq uses its BreachIQ capability to identify recent notable reported data breaches. These breaches are highlighted because of the heightened identity security risks to the victims. BreachIQ uses a proprietary algorithm to analyze more than 1,300 factors of a data breach and create a risk score on a scale of 1-10. The higher. The post Sontiq BreachIQ Data Breach Report: Week of Nov. 8 appeared first on Security Boulevard.
The Hacker News
NOVEMBER 11, 2021
Researchers from Qihoo 360's Netlab security team have released details of a new evolving botnet called "Abcbot" that has been observed in the wild with worm-like propagation features to infect Linux systems and launch distributed denial-of-service (DDoS) attacks against targets.

CSO Magazine
NOVEMBER 11, 2021
Despite all the promises of secure access service edge (SASE), some challenges lie ahead for organizations looking to adopt and implement SASE technologies and practices in a hybrid cloud environment. These include driving the required organizational change to make this paradigm shift, aligning responsibilities appropriately and ensuring you choose the right vendors and products to support your desired outcomes.

Advertisement
The healthcare industry has massively adopted web tracking tools, including pixels and trackers. Tracking tools on user-authenticated and unauthenticated web pages can access personal health information (PHI) such as IP addresses, medical record numbers, home and email addresses, appointment dates, or other info provided by users on pages and thus can violate HIPAA Rules that govern the Use of Online Tracking Technologies by HIPAA Covered Entities and Business Associates.

WIRED Threat Level
NOVEMBER 11, 2021
Visitors to pro-democracy and media sites in the region were infected with malware that could download files, steal data, and more.

Bleeping Computer
NOVEMBER 11, 2021
The TrickBot gang operators are now abusing the Windows 10 App Installer to deploy their BazarLoader malware on the systems of targets who fall victim to a highly targeted spam campaign. [.].

Tech Republic Security
NOVEMBER 11, 2021
64% of survey respondents reported that their companies have concerns about security risks for supply chains.

Bleeping Computer
NOVEMBER 11, 2021
Microsoft says users might experience authentication issues on Domain Controllers (DC) running Windows Server. after installing security updates released during the November Patch Tuesday. [.].

Advertisement
The losses companies suffered in 2023 ransomware attacks increased by 74% compared to those of the previous year, according to new data from the Federal Bureau of Investigation (FBI). The true figure is likely to be even higher, though, as many identity theft and phishing attacks go unreported. Ransomware attackers can potentially paralyze not just private sector organizations but also healthcare facilities, schools, and entire police departments.

Trend Micro
NOVEMBER 11, 2021
QAKBOT operators resumed email spam operations towards the end of September after an almost three-month hiatus. QAKBOT detection has become a precursor to many critical and widespread ransomware attacks. Our report shares some insight into the new techniques and tools this threat is using.

Bleeping Computer
NOVEMBER 11, 2021
Bait attacks are on the rise, and it appears that actors who distribute this special kind of phishing emails prefer to use Gmail accounts to conduct their attacks. [.].
Google Security
NOVEMBER 11, 2021
Posted by Jonathan Metzman, Google Open Source Security Team In recent years, continuous fuzzing has become an essential part of the software development lifecycle. By feeding unexpected or random data into a program, fuzzing catches bugs that would otherwise slip through the most thorough manual checks and provides coverage that would take staggering human effort to replicate.

Threatpost
NOVEMBER 11, 2021
The One Font BEC campaign targets Microsoft 365 users and uses sophisticated obfuscation tactics to slip past security protections to harvest credentials.

Speaker: Blackberry, OSS Consultants, & Revenera
Software is complex, which makes threats to the software supply chain more real every day. 64% of organizations have been impacted by a software supply chain attack and 60% of data breaches are due to unpatched software vulnerabilities. In the U.S. alone, cyber losses totaled $10.3 billion in 2022. All of these stats beg the question, “Do you know what’s in your software?

Security Boulevard
NOVEMBER 11, 2021
Although more than half of IT decision-makers at midsize companies think cybersecurity is a moderate to high priority for their group, the majority believe the larger organization has not prioritized IT security issues. These were among the results of an UncommonX survey of 220 key IT-related professionals at midsize organizations across various industries.
Security Affairs
NOVEMBER 11, 2021
Palo Alto Networks warns of an easy exploitable Remote Code Execution vulnerability in its GlobalProtect VPN product. Palo Alto Networks disclosed a critical remote code execution vulnerability, tracked as CVE-2021-3064 , in its GlobalProtect portal and gateway interfaces. The cybersecurity vendor warns that the vulnerability is easily exploitable by an unauthenticated network-based attacker.
Security Boulevard
NOVEMBER 11, 2021
I joined Zoom in July 2020 — a time when everything about the company had fundamentally changed. The expectations for service delivery were higher than ever, growth reached an unprecedented scale and the role of security had never been more important. While I stepped in during this momentous time, I was determined to bring simplicity. The post Zoom CISO’s Lessons in Scaling With Simplicity appeared first on Security Boulevard.

Digital Shadows
NOVEMBER 11, 2021
Picture this: it’s a Monday morning, and you’ve just found out that a critical vulnerability was announced on your favorite. The post What is Vulnerability Intelligence? first appeared on Digital Shadows.

Speaker: Erika R. Bales, Esq.
When we talk about “compliance and security," most companies want to ensure that steps are being taken to protect what they value most – people, data, real or personal property, intellectual property, digital assets, or any other number of other things - and it’s more important than ever that safeguards are in place. Let’s step back and focus on the idea that no matter how complicated the compliance and security regime, it should be able to be distilled down to a checklist.
Let's personalize your content