UK Electoral Commission had an unpatched Microsoft Exchange Server vulnerability
You have have read about the hack of the Electoral Commission recently. In this piece we take a look at what happened, show they were running Microsoft Exchange Server with Outlook Web App (OWA) facing the internet, and the unpatched vulnerability that presented.
The Electoral Commission ran Microsoft Exchange Server on IP 167.98.206.41 (found by TechCrunch) — this was online until later in 2022, at which point it dropped offline. According to the Electoral Commission’s advisory, they became aware of the incident in October 2022.
Here we see, via Shodan.io, the server was still available in late September 2022 — afterwards, it stopped responding, and still isn’t online now.
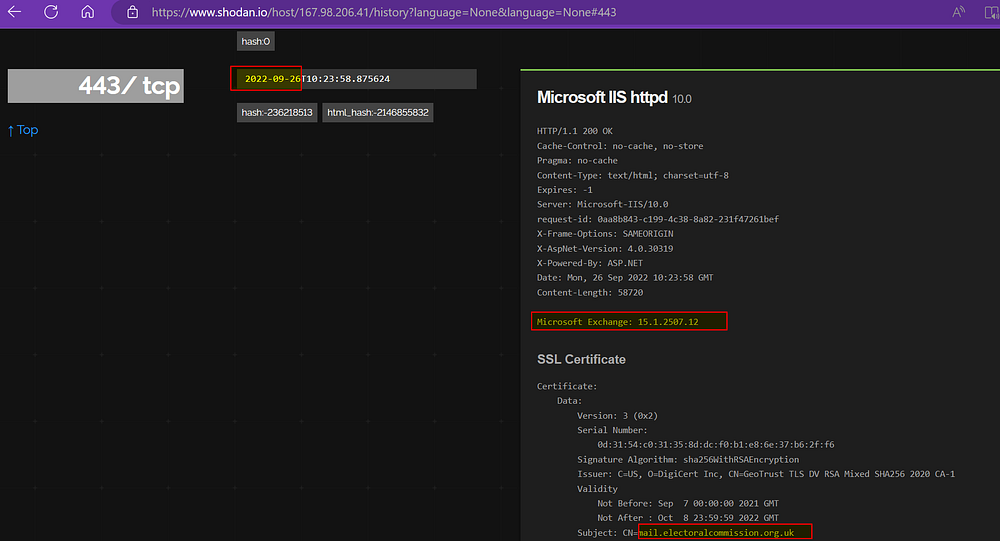
We can see the version of Microsoft Exchange Server in the data — 15.1.2507.12. This corresponds to Exchange Server 2016, last security updated in August 2022:
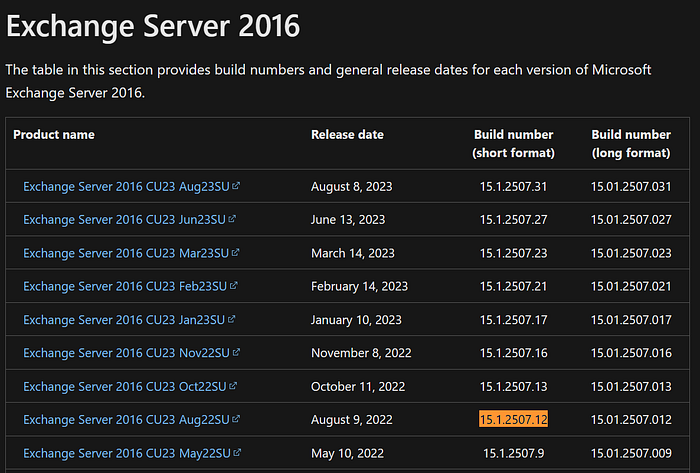
To be clear, this means the Electoral Commission (or their IT supplier) did the right thing — they were applying security patches quickly during this time in 2022. 2021 data isn’t available, so it is unknown how well they were patching prior during the ProxyShell and ProxyLogon Microsoft Exchange vulnerabilities.
However, something was wrong.
Around this time, in late September 2022, a vulnerability chain dropped as a zero day called ProxyNotShell, as I documented here:
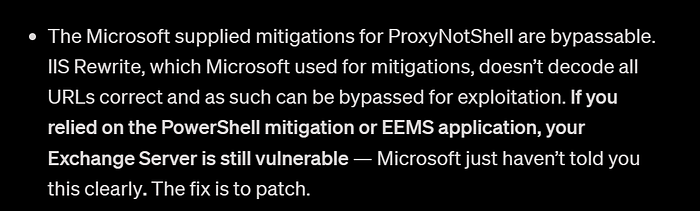
At the time Microsoft released temporary mitigations rather than a security patch — it took until November 2022 for a security update to appear to fully resolve the problem. This was a significant delay. In the meantime, the security mitigations Microsoft provided were repeatedly bypassed, as visible in my writeup linked above.
The Electoral Commission was running Exchange Server in this configuration during the main incident timeline. They were vulnerable to ProxyNotShell attacks. ProxyNotShell allows remote code execution on their Exchange email server, or in other words complete compromise of their network (Exchange Server runs with highly privileged Active Directory accounts by default).
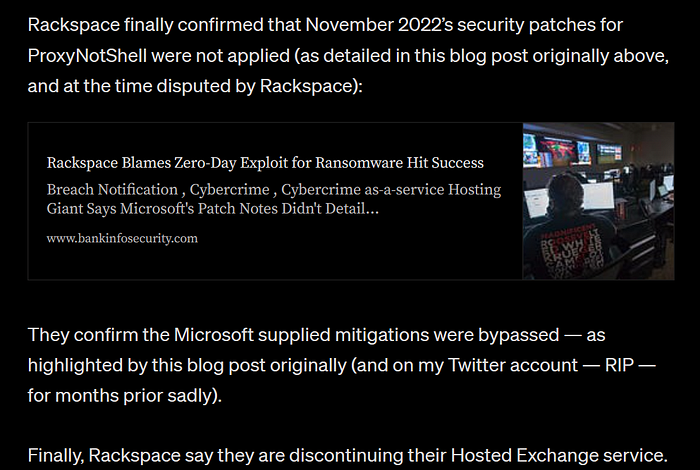
This lead to several big security breaches. For example, the Rackspace Hosted Exchange hack — which was so bad it caused Rackspace to abandon the platform and customers.
As I wrote at the time:
Rackspace directly confirmed it was ProxyNotShell months after my blog post, saying they were relying on Microsoft’s supplied mitigations.
Key learnings
- Microsoft needs to ship security patches for Microsoft Exchange Server faster. It needs some kind of emergency patch pipeline.
- Temporary mitigations are good, but should not be relied on for months for highly attacked systems used by governments etc.
- If you present Microsoft Exchange Server to the internet — particularly OWA (Outlook Web App) I would strongly suggest being very aware the system will get targeted, and implement enhanced security monitoring and containment to limit threat actor access.
- Consider migrating email hosting to something like Google Workspace if you cannot resource the above.

