Microsoft Uses Trademark Law to Disrupt Trickbot Botnet
Krebs on Security
OCTOBER 12, 2020
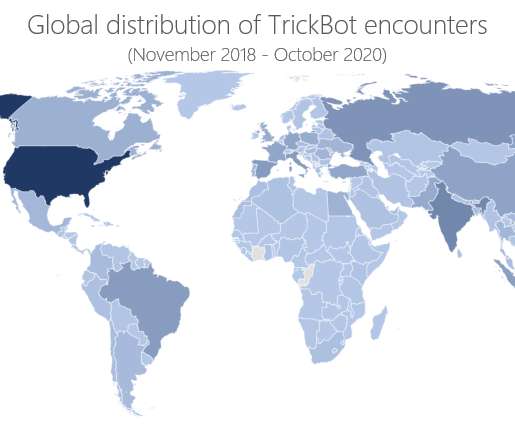
Microsoft Corp. has executed a coordinated legal sneak attack in a bid to disrupt the malware-as-a-service botnet Trickbot , a global menace that has infected millions of computers and is used to spread ransomware. A court in Virginia granted Microsoft control over many Internet servers Trickbot uses to plunder infected systems, based on novel claims that the crime machine abused the software giant’s trademarks.






















Let's personalize your content