Why & Where You Should You Plant Your Flag
Krebs on Security
AUGUST 12, 2020
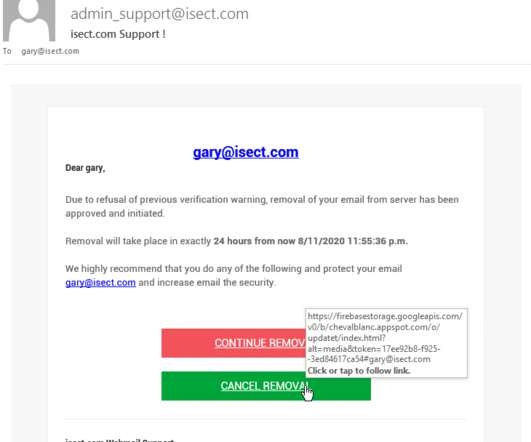
Several stories here have highlighted the importance of creating accounts online tied to your various identity, financial and communications services before identity thieves do it for you. This post examines some of the key places where everyone should plant their virtual flags. As KrebsOnSecurity observed back in 2018 , many people — particularly older folks — proudly declare they avoid using the Web to manage various accounts tied to their personal and financial data — including ev







































Let's personalize your content