New GwisinLocker ransomware encrypts Windows and Linux ESXi servers
Bleeping Computer
AUGUST 6, 2022
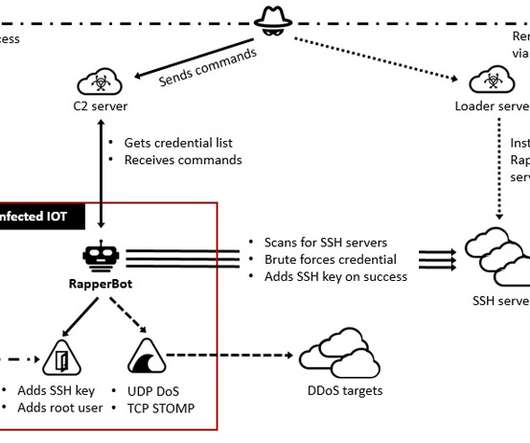
A new ransomware family called 'GwisinLocker' targets South Korean healthcare, industrial, and pharmaceutical companies with Windows and Linux encryptors, including support for encrypting VMware ESXi servers and virtual machines. [.].




















Let's personalize your content