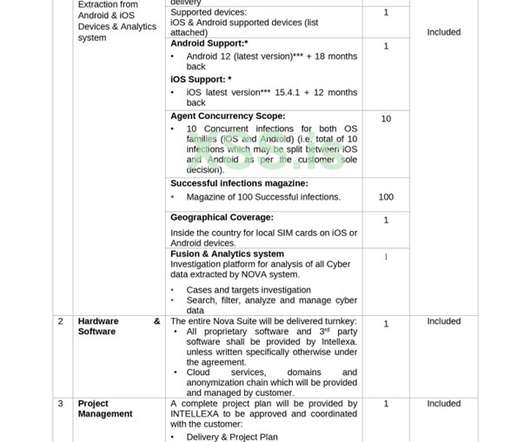
Will Voluntary CISA Cyber Goals Be Enough to Protect Critical Infrastructure?
Lohrman on Security
AUGUST 28, 2022
The Cybersecurity and Infrastructure Security Agency is getting pushback from critical infrastructure owners and operators on cyber goals and objectives. So what happens next?

























Let's personalize your content