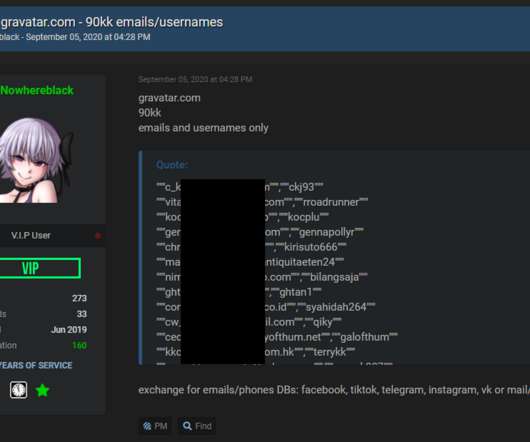
When is a Scrape a Breach?
Troy Hunt
DECEMBER 15, 2021
A decade and a bit ago during my tenure at Pfizer, a colleague's laptop containing information about customers, healthcare providers and other vendors was stolen from their car. The machine had full disk encryption and it's not known whether the thief was ever actually able to access the data. It's not clear if the car was locked or not.





































Let's personalize your content