Massive Brazilian Data Breach
Schneier on Security
JANUARY 26, 2021
I think this is the largest data breach of all time: 220 million people. ( Lots more stories are in Portuguese.).

Schneier on Security
JANUARY 26, 2021
I think this is the largest data breach of all time: 220 million people. ( Lots more stories are in Portuguese.).

Tech Republic Security
JANUARY 26, 2021
Google said the attackers were targeting security researchers by using fake LinkedIn and Twitter profiles and asking to collaborate.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.
Thales Cloud Protection & Licensing
JANUARY 26, 2021
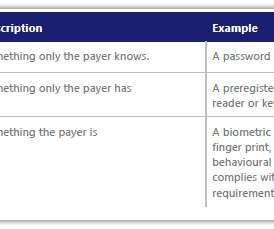
The Future of Payments Security. madhav. Tue, 01/26/2021 - 09:17. Criminals use a wide range of methods to commit fraud. The increasing trend of using mobile payments for in-store purchases (especially during the pandemic) is leading criminals to increasingly focus their efforts on defrauding people through online fraud and scams. Fraud and scams move to the web.

Tech Republic Security
JANUARY 26, 2021
A new survey from Syntax found that many decision-makers are not happy with their existing security tools.

Advertisement
How many people would you trust with your house keys? Chances are, you have a handful of trusted friends and family members who have an emergency copy, but you definitely wouldn’t hand those out too freely. You have stuff that’s worth protecting—and the more people that have access to your belongings, the higher the odds that something will go missing.

Digital Shadows
JANUARY 26, 2021
Note: This blog is a roundup of our quarterly ransomware series. You can also see our Q2 Ransomware Trends, Q3. The post Ransomware: Analyzing the data from 2020 first appeared on Digital Shadows.

Tech Republic Security
JANUARY 26, 2021
At a national summit, Louisiana Gov. John Bel Edwards said before his state could test a cyberattack plan, five schools were hit with ransomware.
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.

Tech Republic Security
JANUARY 26, 2021
Cybersecurity firm Akamai said in a report that COVID-19 and a newfound reliance on digital tools prompted a spike.

Cisco Security
JANUARY 26, 2021
What happens to privacy protections in a pandemic? When any serious threat to our safety and well-being arises, many would think privacy protections would take a back seat. After all, our personal data, including our health status, social contacts, and physical locations, have been needed to help control the spread of COVID-19. What’s more, the rapid shift to remote working has left organizations scrambling to keep their functions up and running, and privacy protections might well have been an a

Adam Shostack
JANUARY 26, 2021
I’m very excited that Gary McGraw is joining the Irius Risk Technical Advisory Board as board chair. Gary’s a pioneer in software security, and his work in machine learning was my choice to kick off blogging 2020.
Tech Republic Security
JANUARY 26, 2021
The data protection company's latest delivers new features on a simplified platform to provide customers with additional choice for deployment across edge, core, and cloud.

Advertiser: Revenera
In a recent study, IDC found that 64% of organizations said they were already using open source in software development with a further 25% planning to in the next year. Most organizations are unaware of just how much open-source code is used and underestimate their dependency on it. As enterprises grow the use of open-source software, they face a new challenge: understanding the scope of open-source software that's being used throughout the organization and the corresponding exposure.

CSO Magazine
JANUARY 26, 2021
Among the biggest cybersecurity challenges CISOs are facing is how to maintain data protection and privacy when their organizations shift workloads to the cloud. In particular, how can they manage security controls in a cloud-only environment?

SC Magazine
JANUARY 26, 2021
While no specific names were included, a new report pointed to CEOs of U.S. companies as a primary target of a new phishing scheme. Here, Amazon founder Jeff Bezos speaks about a recent development by Blue Origin, the space company he founded. (Mark Wilson/Getty Images). Cybercriminals have been using a phishing kit featuring fake Office 365 password alerts as a lure to target the credentials of chief executives, business owners and other high-level corporate leaders.
Tech Republic Security
JANUARY 26, 2021
BeyondCorp Enterprise is a scalable, agentless, end-to-end zero trust platform that lives entirely within Chrome Enterprise.
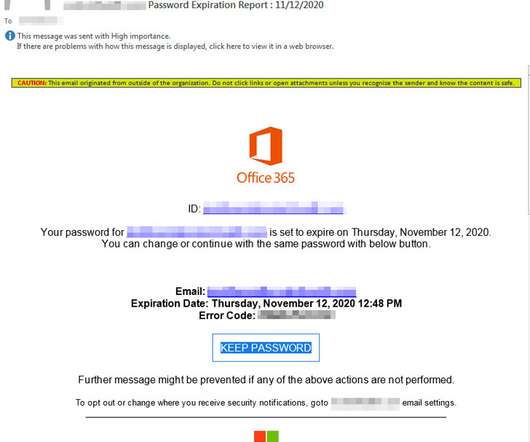
The Hacker News
JANUARY 26, 2021
An evolving phishing campaign observed at least since May 2020 has been found to target high-ranking company executives across manufacturing, real estate, finance, government, and technological sectors with the goal of obtaining sensitive information.

Advertisement
Within the past few years, ransomware attacks have turned to critical infrastructure, healthcare, and government entities. Attackers have taken advantage of the rapid shift to remote work and new technologies. Add to that hacktivism due to global conflicts and U.S. elections, and an increased focus on AI, and you have the perfect recipe for a knotty and turbulent 2024.
Tech Republic Security
JANUARY 26, 2021
Jack Wallen shows you how easy it is to block and report spam SMS messages on the Android platform.
Zero Day
JANUARY 26, 2021
For some people, it's apparently easier to manage your own browser than port some web forms from Flash to HTML.
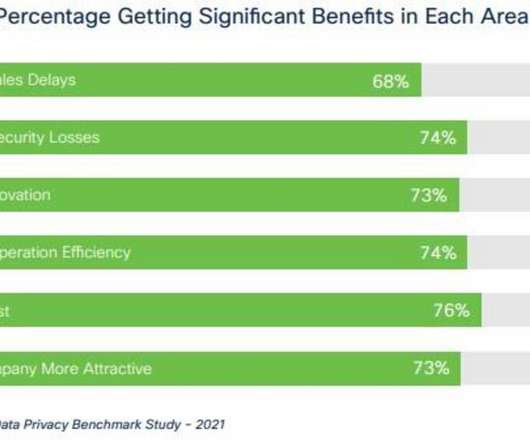
Tech Republic Security
JANUARY 26, 2021
93% of organizations turned to privacy teams to help navigate the COVID-19 pandemic, a new Cisco report finds.
Security Affairs
JANUARY 26, 2021
A vulnerability in the video-sharing social networking service TikTok could have allowed hackers to steal users’ private personal information. Developers at ByteDance, the company that owns TikTok, have fixed a security vulnerability in the popular video-sharing social networking service that could have allowed attackers to steal users’ private personal information.

Advertisement
The healthcare industry has massively adopted web tracking tools, including pixels and trackers. Tracking tools on user-authenticated and unauthenticated web pages can access personal health information (PHI) such as IP addresses, medical record numbers, home and email addresses, appointment dates, or other info provided by users on pages and thus can violate HIPAA Rules that govern the Use of Online Tracking Technologies by HIPAA Covered Entities and Business Associates.

Dark Reading
JANUARY 26, 2021
Security Assertion Markup Language, a protocol most people use daily to log into applications, makes authentication easier for both admins and users. Here's what you need to know about SAML (and what it has to do with 'GoldenSAML').

Cisco Security
JANUARY 26, 2021
Today more than ever, it is critical to protect our family and friends, both online and off. This Unhackable MFA challenge is a simple pledge that anyone can make and can have a major impact on everyone’s online safety. Therefore, we are challenging every Cisco employee, cyber fan, security and IT Pro and Unhackable podcast listener to take a small step and contact someone right now to tell them you’ll help them with MFA.

Zero Day
JANUARY 26, 2021
Mimecast, Palo Alto Networks, Qualys, and Fidelis confirmed this week they were also targeted during the SolarWinds supply chain attack.

Approachable Cyber Threats
JANUARY 26, 2021
Category Awareness Risk Level. Apple introduced its native Screen Time application in the fall of 2018 to track and report your application and screen usage. Its goal was simple: give users insight into just how much time they spend interacting with their device. The idea was to help people step away from their devices and be more present in the moment.

Advertisement
The losses companies suffered in 2023 ransomware attacks increased by 74% compared to those of the previous year, according to new data from the Federal Bureau of Investigation (FBI). The true figure is likely to be even higher, though, as many identity theft and phishing attacks go unreported. Ransomware attackers can potentially paralyze not just private sector organizations but also healthcare facilities, schools, and entire police departments.
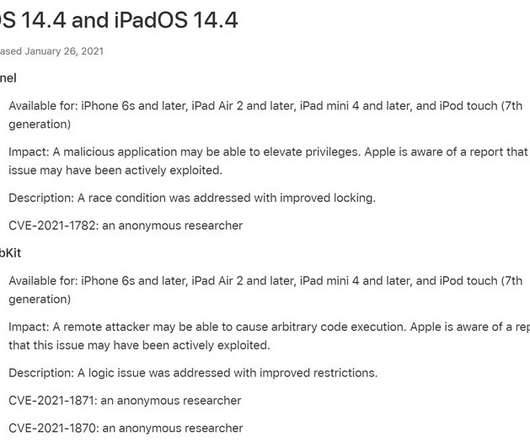
The Hacker News
JANUARY 26, 2021
Apple on Tuesday released updates for iOS, iPadOS, and tvOS with fixes for three security vulnerabilities that it says may have been actively exploited in the wild. Reported by an anonymous researcher, the three zero-day flaws — CVE-2021-1782, CVE-2021-1870, and CVE-2021-1871 — could have allowed an attacker to elevate privileges and achieve remote code execution.

Zero Day
JANUARY 26, 2021
The vulnerability, named "Baron Samedit," impacts most Linux distributions today.
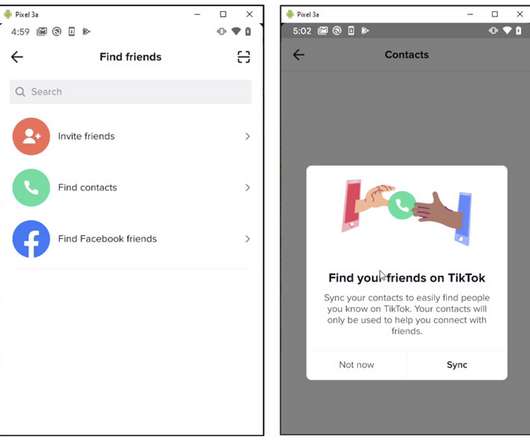
The Hacker News
JANUARY 26, 2021
Cybersecurity researchers on Tuesday disclosed a now-patched security flaw in TikTok that could have potentially enabled an attacker to build a database of the app's users and their associated phone numbers for future malicious activity.

Hot for Security
JANUARY 26, 2021
PALFINGER AG, the giant manufacturer of lifting systems, has posted a statement on its home page confirming it is currently under attack by hackers. Because of the attack, the firm’s IT infrastructure has been crippled. With 150 crane models and a market share of 35 percent, PALFINGER is the world market leader in hydraulic lifting, loading and handling systems.

Speaker: Blackberry, OSS Consultants, & Revenera
Software is complex, which makes threats to the software supply chain more real every day. 64% of organizations have been impacted by a software supply chain attack and 60% of data breaches are due to unpatched software vulnerabilities. In the U.S. alone, cyber losses totaled $10.3 billion in 2022. All of these stats beg the question, “Do you know what’s in your software?
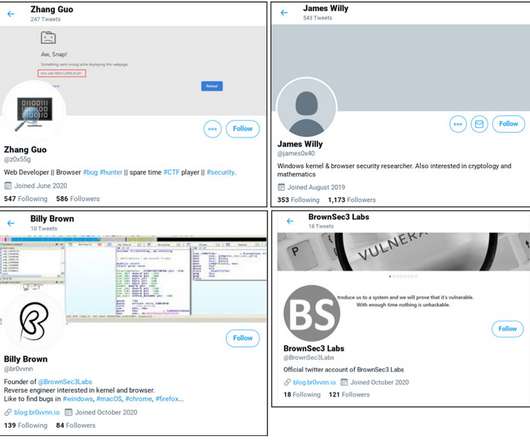
The Hacker News
JANUARY 26, 2021
Google on Monday disclosed details about an ongoing campaign carried out by a government-backed threat actor from North Korea that has targeted security researchers working on vulnerability research and development.

Hot for Security
JANUARY 26, 2021
Ransomware attacks are among the greatest security threats we face in the digital world, a trend that has continued to expand and grow in sophistication over the past years. The threat actor’s goal is simple: Find an opportunistic target and lure it into accessing, downloading or installing malicious software onto their device so it can encrypt user files and prevent them from accessing the system.

The Hacker News
JANUARY 26, 2021
Most companies with small security teams face the same issues. They have inadequate budgets, inadequate staff, and inadequate skills to face today's onslaught of sophisticated cyberthreats. Many of these companies turn to virtual CISOs (vCISOs) to provide security expertise and guidance.

Hot for Security
JANUARY 26, 2021
Fraudsters impersonating UK’s National Health Service (NHS) are actively exploiting the COVID-19 vaccination campaign to dupe citizens into providing their personal information through various phishing emails. The campaign seems to have started on January 25, as seen in the scam recipients’ multiple Twitter posts. In one version of the phishing email, users are asked to confirm or reject the coronavirus vaccination by accessing the appropriate link.

Speaker: Erika R. Bales, Esq.
When we talk about “compliance and security," most companies want to ensure that steps are being taken to protect what they value most – people, data, real or personal property, intellectual property, digital assets, or any other number of other things - and it’s more important than ever that safeguards are in place. Let’s step back and focus on the idea that no matter how complicated the compliance and security regime, it should be able to be distilled down to a checklist.
Let's personalize your content