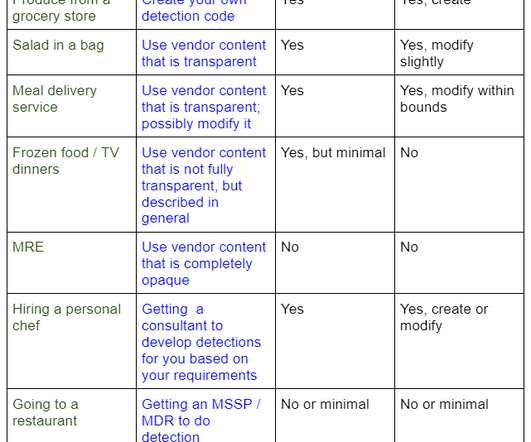
Detection as Code? No, Detection as COOKING!
Anton on Security
JUNE 3, 2022
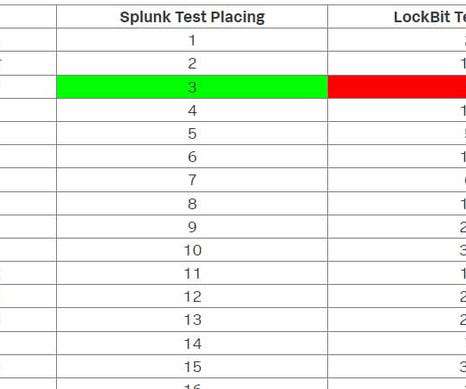
One of the well-advertised reasons for being in the office is about those “magical hallway conversations” (Google it). One happened to me a few days ago and led to a somewhat heated debate on the nature of modern threat detection. It also resulted in this half-shallow / half-profound blog that relates detection to cooking and farming! Well, the magical discussion was over lunch, so this is perhaps logical.







































Let's personalize your content