Backing up data is more important as people work from home during COVID-19
Tech Republic Security
SEPTEMBER 9, 2020
TechRepublic writer Erik Eckel gives tips on how to make sure your data is safe if you're working from home.

Tech Republic Security
SEPTEMBER 9, 2020
TechRepublic writer Erik Eckel gives tips on how to make sure your data is safe if you're working from home.
Security Affairs
SEPTEMBER 9, 2020
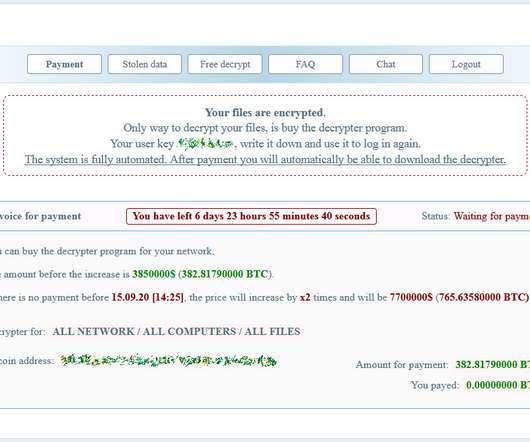
K-Electric, the electricity provider for the city of Karachi, Pakistan, was hit by a Netwalker ransomware attack that blocked billing and online services. K-Electric, the electricity provider for Karachi (Pakistan) is another victim of the Netwalker ransomware gang, the infection disrupted billing and online services. K-Electric (KE) (formerly known as Karachi Electric Supply Company / Karachi Electric Supply Corporation Limited) is a Pakistani investor-owned utility managing all three key stage
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Tech Republic Security
SEPTEMBER 9, 2020
Hartford Mayor Luke Bronin said the attackers did not make a specific ransom demand after shutting down systems for 40 schools.

Trend Micro
SEPTEMBER 9, 2020
This blog will discuss the ruthless battle for computing power among the different cryptocurrency-mining malware that target Linux systems. We also discuss the shifts in entry points that cover Docker environments and applications with open APIs.

Advertisement
How many people would you trust with your house keys? Chances are, you have a handful of trusted friends and family members who have an emergency copy, but you definitely wouldn’t hand those out too freely. You have stuff that’s worth protecting—and the more people that have access to your belongings, the higher the odds that something will go missing.

Tech Republic Security
SEPTEMBER 9, 2020
This month's patch Tuesday includes patches for 15 Microsoft products, including 23 critical CVEs.

Dark Reading
SEPTEMBER 9, 2020
Are attacks on IoT physical security devices real or just theoretical? Why professionals need to be aware of the real-life examples in an effort to guard against future attacks on their own businesses.
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.

Dark Reading
SEPTEMBER 9, 2020
A flurry of recent attacks is complicating attempts to deliver classes online at some schools in different parts of the country.

Threatpost
SEPTEMBER 9, 2020
Malware can take over common device functions as well as creates a phishing page to steal Facebook credentials.

Dark Reading
SEPTEMBER 9, 2020
A ruling that a police officer's personal use of a law enforcement database is "hacking" has security researchers worried for the future.

Threatpost
SEPTEMBER 9, 2020
Researchers warn of critical vulnerabilities in a third-party industrial component used by top ICS vendors like Rockwell Automation and Siemens.

Advertiser: Revenera
In a recent study, IDC found that 64% of organizations said they were already using open source in software development with a further 25% planning to in the next year. Most organizations are unaware of just how much open-source code is used and underestimate their dependency on it. As enterprises grow the use of open-source software, they face a new challenge: understanding the scope of open-source software that's being used throughout the organization and the corresponding exposure.

Tech Republic Security
SEPTEMBER 9, 2020
TechRepublic writer Erik Eckel gives tips on how to make sure your data is safe if you're working from home.

InfoWorld on Security
SEPTEMBER 9, 2020
As more and more organizations move containerized applications into production, Kubernetes has become the de facto approach for managing those applications in private, public and hybrid cloud settings. In fact, at least 84% of organizations already use containers in production, and 78% leverage Kubernetes to deploy them, according to the Cloud Native Computing Foundation.

Dark Reading
SEPTEMBER 9, 2020
An interdisciplinary research team constructs a way for companies to share breach data without revealing specific details that could exposes businesses to legal risk.

Threatpost
SEPTEMBER 9, 2020
The September Android security bulletin addressed critical- and high-severity flaws tied to 53 CVEs overall.

Advertisement
Within the past few years, ransomware attacks have turned to critical infrastructure, healthcare, and government entities. Attackers have taken advantage of the rapid shift to remote work and new technologies. Add to that hacktivism due to global conflicts and U.S. elections, and an increased focus on AI, and you have the perfect recipe for a knotty and turbulent 2024.

Dark Reading
SEPTEMBER 9, 2020
In the wake of COVID-19, today's remote workforce is here to stay, at least for the foreseeable future. And with it, an increase in identity-related security incidents.

Threatpost
SEPTEMBER 9, 2020
The malware has popped up in a targeted campaign and a new infection routine.

Dark Reading
SEPTEMBER 9, 2020
Yes, according to 21% of security pros who participated in the 2020 Black Hat Attendee Survey.

NopSec
SEPTEMBER 9, 2020
NopSec’s Vulnerability Risk Management Platform Enables Organizations to Better Manage Business Risk. New York, NY – NopSec,Inc. , a leader in vulnerability and cyber threat management, today announced that the Program Intelligence Module will extend the power of the Unified VRM , addressing additional use cases to strengthen the security posture of customers.

Advertisement
The healthcare industry has massively adopted web tracking tools, including pixels and trackers. Tracking tools on user-authenticated and unauthenticated web pages can access personal health information (PHI) such as IP addresses, medical record numbers, home and email addresses, appointment dates, or other info provided by users on pages and thus can violate HIPAA Rules that govern the Use of Online Tracking Technologies by HIPAA Covered Entities and Business Associates.

Dark Reading
SEPTEMBER 9, 2020
As election season ramps up, organizations engaged in the process must strengthen security to prevent chaos and disorder from carrying the day. Here's how.

ForAllSecure
SEPTEMBER 9, 2020
At ForAllSecure, we’ve observed an increasing uptick in organizations looking for alternatives to mainstream application security tools. Why? Organizations are finding that today’s AST tools aren’t servicing their objectives to develop software faster and deploy frequently. In this blog series, we’ll chronicle the top challenges of incorporating application security testing in DevOps workflows.

Dark Reading
SEPTEMBER 9, 2020
An analysis of initial access brokers explains how they break into vulnerable organizations and sell their access for up to $10,000.
Schneier on Security
SEPTEMBER 9, 2020
The Trump Administration just published “ Space Policy Directive – 5 “: “Cybersecurity Principles for Space Systems.” It’s pretty general: Principles. (a) Space systems and their supporting infrastructure, including software, should be developed and operated using risk-based, cybersecurity-informed engineering. Space systems should be developed to continuously monitor, anticipate,and adapt to mitigate evolving malicious cyber activities that could manipulate,

Advertisement
The losses companies suffered in 2023 ransomware attacks increased by 74% compared to those of the previous year, according to new data from the Federal Bureau of Investigation (FBI). The true figure is likely to be even higher, though, as many identity theft and phishing attacks go unreported. Ransomware attackers can potentially paralyze not just private sector organizations but also healthcare facilities, schools, and entire police departments.

Dark Reading
SEPTEMBER 9, 2020
The breach occurred as part of a ransomware attack against service provider Blackbaud.

WIRED Threat Level
SEPTEMBER 9, 2020
Brian Murphy says he was pressured to alter reports on Russia and white supremacy—and that he was fired for refusing to budge.

SecureWorld News
SEPTEMBER 9, 2020
President Trump recently signed a Space Policy Directive (SPD) to protect American space systems from cyber threats. At first glance, you might read cyber threats in space and think, "What, space cyber threats? Are we talking aliens?" No, the answer is not aliens. These threats are coming from our home planet, and they are indeed very real. Why does cybersecurity in space matter?

Speaker: Blackberry, OSS Consultants, & Revenera
Software is complex, which makes threats to the software supply chain more real every day. 64% of organizations have been impacted by a software supply chain attack and 60% of data breaches are due to unpatched software vulnerabilities. In the U.S. alone, cyber losses totaled $10.3 billion in 2022. All of these stats beg the question, “Do you know what’s in your software?

Dark Reading
SEPTEMBER 9, 2020
Delve's automated vulnerability platform provides insight on high-risk vulnerabilities across an organization's network, endpoints, and cloud.

Dark Reading
SEPTEMBER 9, 2020
Assuming that you're truly stuck, here are some things to consider.
Let's personalize your content