The ALPHV ransomware group (aka BlackCat) was observed employing signed malicious Windows kernel drivers to evade detection by security software during attacks.
The driver seen by Trend Micro is an improved version of the malware known as 'POORTRY' that Microsoft, Mandiant, Sophos, and SentinelOne spotted in ransomware attacks late last year.
The POORTRY malware is a Windows kernel driver signed using stolen keys belonging to legitimate accounts in Microsoft's Windows Hardware Developer Program.
This malicious driver was used by the UNC3944 hacking group, also known as 0ktapus and Scattered Spider, to terminate security software running on a Windows device to evade detection.
While security software is usually protected from being terminated or tampered with, as Windows kernel drivers run with the highest privileges in the operating system, they can be used to terminate almost any process.
Trend Micro says the ransomware actors attempted to use the Microsoft-signed POORTRY driver, but its detection rates were high following the publicity it got and after the code-signing keys were revoked.
Hence, the hackers deployed an updated version of the POORTRY kernel driver signed using a stolen or leaked cross-signing certificate.
The new driver used by the BlackCat ransomware operation helps them elevate their privileges on compromised machines and then stop processes relating to security agents.
Furthermore, it may provide a loose link between the ransomware gang and the UNC3944/Scattered Spider hacking groups.
The Malicious Windows kernel driver
The signed driver seen by Trend Micro in February 2023 BlackCat attacks is 'ktgn.sys,' dropped onto the victim's filesystem in the %Temp% folder and then loaded by a user mode program named 'tjr.exe.'
The analysts say the digital signature of ktgn.sys has been revoked; however, the driver will still load without a problem on 64-bit Windows systems with enforced signing policies.
The malicious kernel driver exposes an IOCTL interface that allows the user mode client, tjr.exe, to issue commands that the driver will execute with Windows kernel privileges.
"From our analysis of what occurs when a user interfaces with this driver, we observed that it only uses one of the exposed Device Input and Output Control (IOCTL) code — Kill Process, which is used to kill security agent processes installed on the system," explains the Trend Micro report.
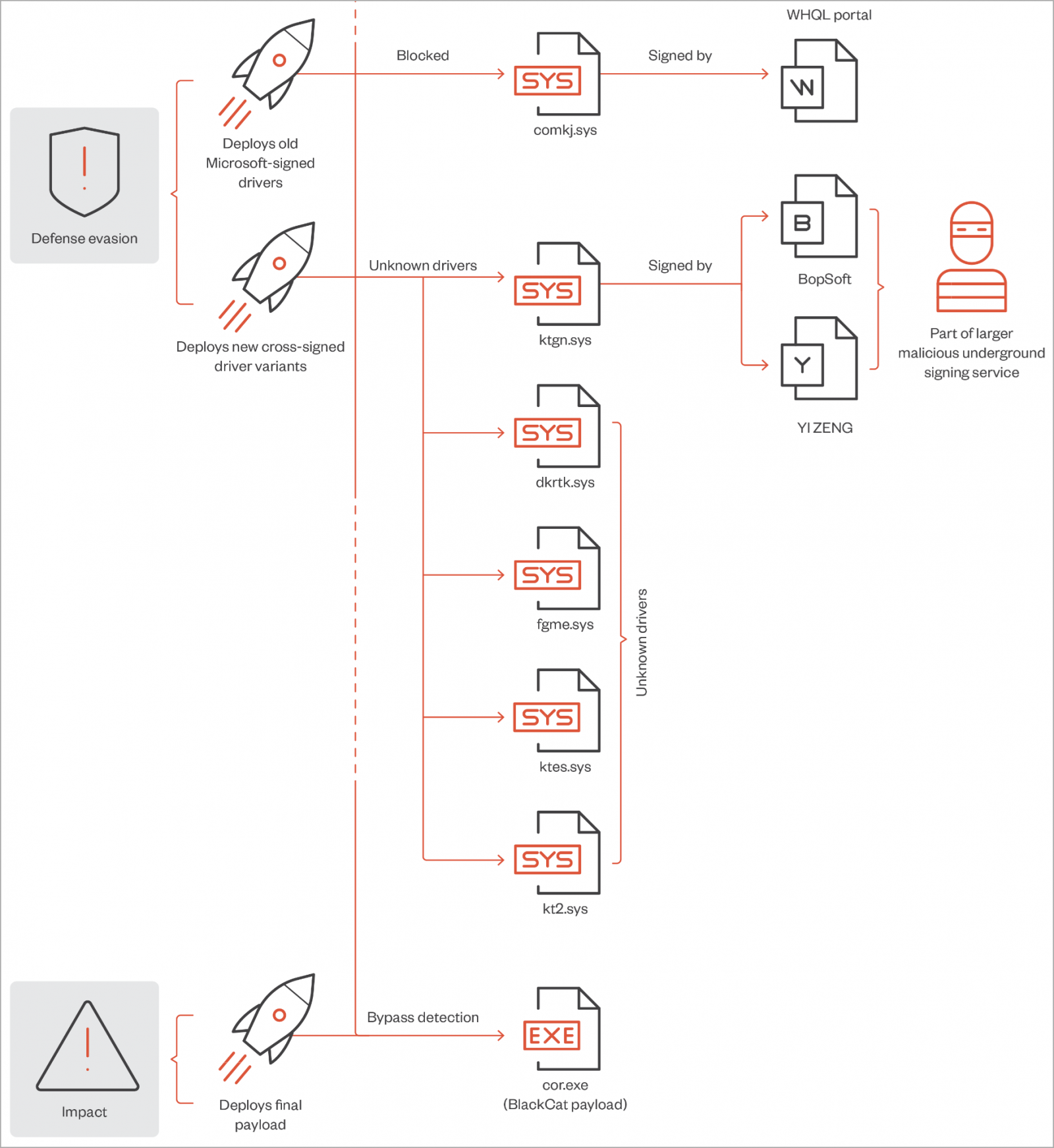
Trend Micro's analysts observed the exposed following commands that can be issued to the driver:
- Activate driver
- Deactivate the driver after the user mode client finishes its operation
- Kill any user-mode process
- Delete specific file paths
- Force-delete a file by freeing its handles and terminating running processes using it
- Copy files
- Force-copy files using a similar mechanism to force-delete
- Register Process/Thread Notification callbacks
- Unregister Process/Thread Notification callbacks
- Reboot the system by calling the 'HalReturnToFirmware' API
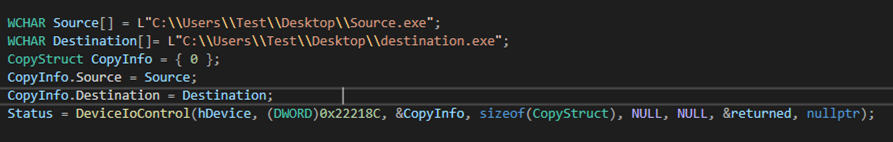
Trend Micro comments that the two commands used for Process/Thread Notification callbacks are not working, indicating that the driver is currently under development or still in a testing phase.
System administrators are recommended to use the indicators of compromise shared by Trend Micro and add the malicious drivers used by the ransomware actors to the Windows driver blocklist.
Windows admins should also ensure that 'Driver Signature Enforcement' is enabled, which blocks the installation of any drivers that do not have a valid digital signature.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now