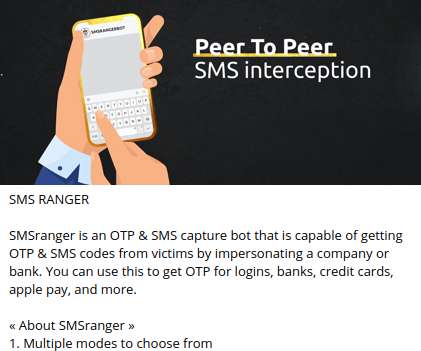
The Rise of One-Time Password Interception Bots
Krebs on Security
SEPTEMBER 29, 2021
In February, KrebsOnSecurity wrote about a novel cybercrime service that helped attackers intercept the one-time passwords (OTPs) that many websites require as a second authentication factor in addition to passwords. That service quickly went offline, but new research reveals a number of competitors have since launched bot-based services that make it relatively easy for crooks to phish OTPs from targets.








































Let's personalize your content