Home » Cybersecurity » Threats & Breaches » Vulnerabilities » New Year, New CVE: a Deep Dive into the ‘node-forge’ (CVE-2022-0122)
New Year, New CVE: a Deep Dive into the ‘node-forge’ (CVE-2022-0122)
With over 16 Million weekly downloads, the important and widely-used “node-forge” component on npm implements key security functions, including Transport Layer Security protocol, cryptographic functions, and development tools for web apps in native JavaScript.
The program is in use by industry giants such as Cisco, Microsoft, and Alexa (yes, the beloved smart speaker that’s in many people’s homes), according to grep.app:
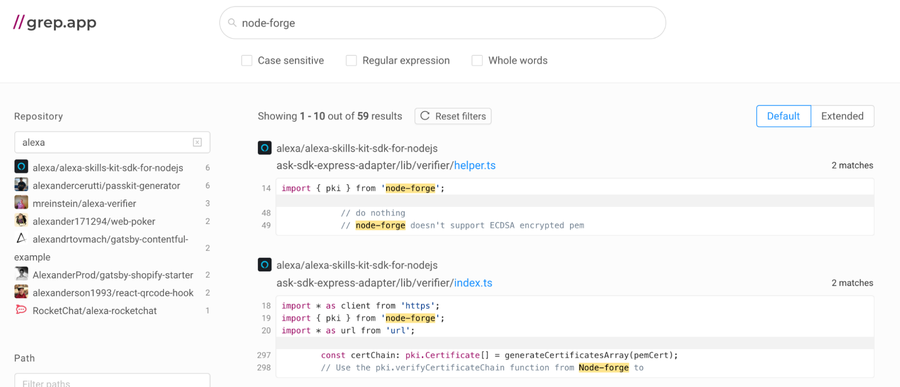
grep.app results showing the use of node-forge in Alexa projects
CVE-2022-0122 refers to an Open Redirect vulnerability in the parseUrl function from the utils.js file within the package. This function is in charge of taking a supplied string and validating its correctness to then forming and returning an object that is easier to manipulate and work with. To do this, it first uses a regular expression (regex) to analyze the string. Regex is supported by hundreds of applications for text and string management, and this regex code is the root cause of the vulnerability.
Irregular Regex
At the beginning of the function, we can even see a comment that says “FIXME: this regex looks a bit broken.” This suggests that the developers understood this was an issue but unaware of the potential for abuse.
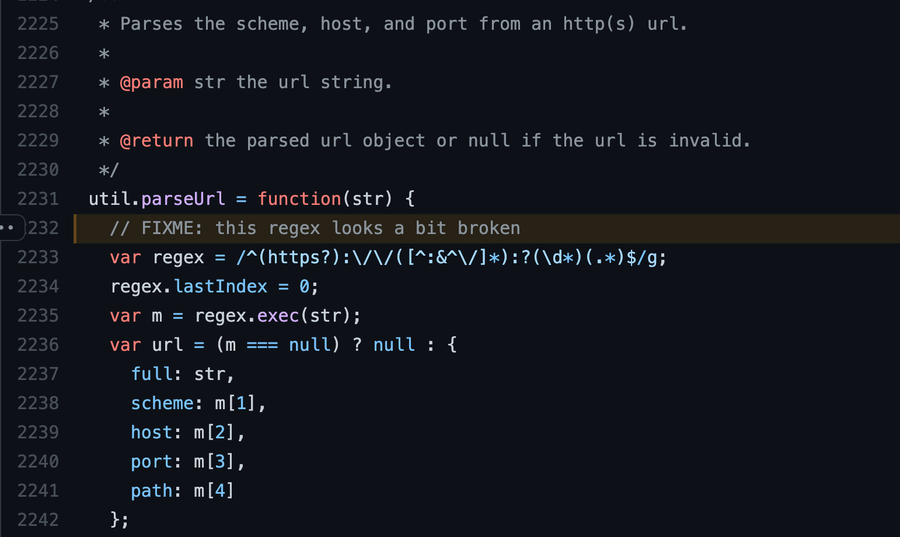
Initial portion of the vulnerable function with a “FIXME” comment.
To analyze the code, we’ll look at one of my favorite regex analysis tools: regex101. It breaks the code down with an easily explanation, as well as letting you play around with and even debug the expression to see potential matches.
The first part of this regex tells us that the string must start with either `http` or `https`. We know this because it has the ^ symbol, which asserts the start of a line, followed by a capturing group for `https?`. The question mark, ?, (Read more...)
*** This is a Security Bloggers Network syndicated blog from Sonatype Blog authored by Juan Aguirre. Read the original post at: https://blog.sonatype.com/new-year-new-cve-a-deep-dive-into-the-node-forge-cve-2022-0122





