How to Tell a Job Offer from an ID Theft Trap
Krebs on Security
MAY 21, 2021
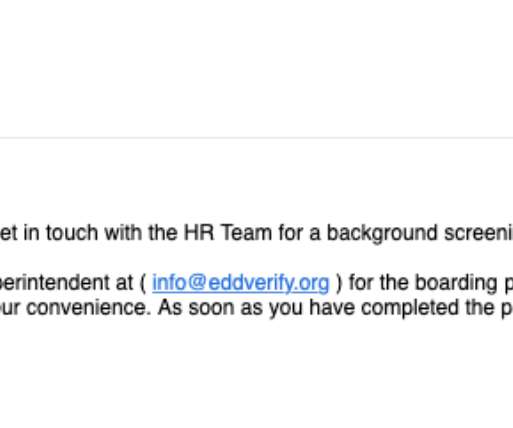
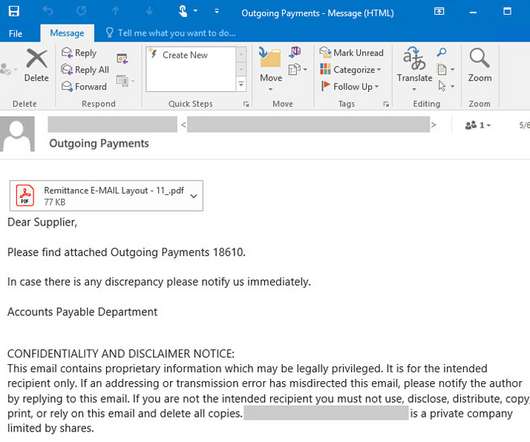
One of the oldest scams around — the fake job interview that seeks only to harvest your personal and financial data — is on the rise, the FBI warns. Here’s the story of a recent LinkedIn impersonation scam that led to more than 100 people getting duped, and one almost-victim who decided the job offer was too-good-to-be-true. Last week, someone began began posting classified notices on LinkedIn for different design consulting jobs at Geosyntec Consultants , an environmental engi









































Let's personalize your content