Live Coronavirus Map Used to Spread Malware
Krebs on Security
MARCH 12, 2020
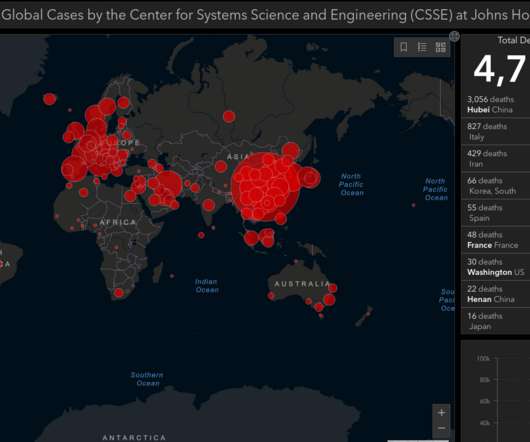
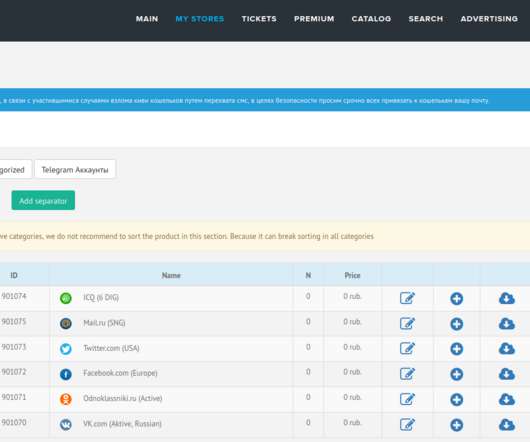
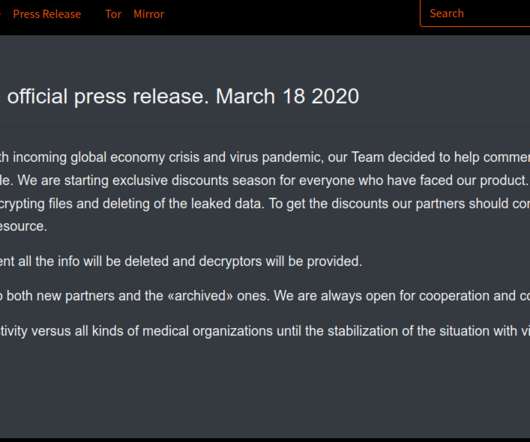
Cybercriminals constantly latch on to news items that captivate the public’s attention, but usually they do so by sensationalizing the topic or spreading misinformation about it. Recently, however, cybercrooks have started disseminating real-time, accurate information about global infection rates tied to the Coronavirus/COVID-19 pandemic in a bid to infect computers with malicious software.




































Let's personalize your content