2020 Oscar Nominees Used to Spread Malware
Adam Levin
FEBRUARY 7, 2020
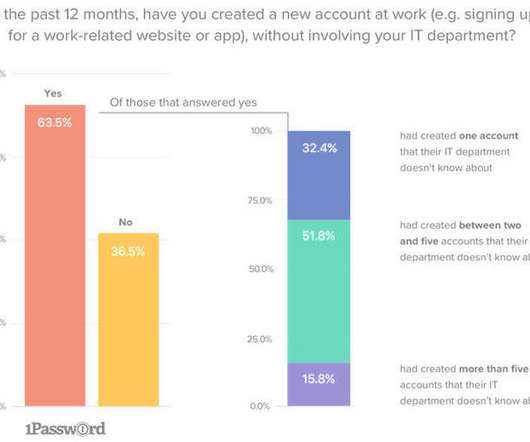
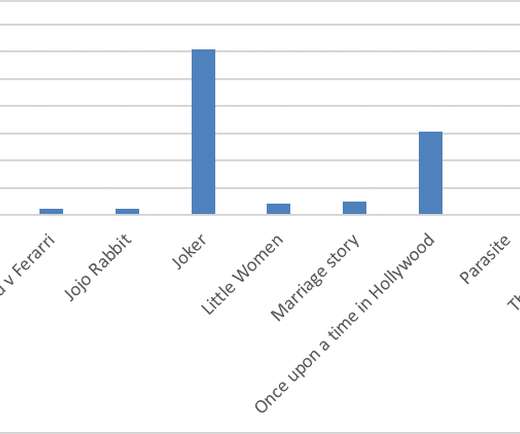
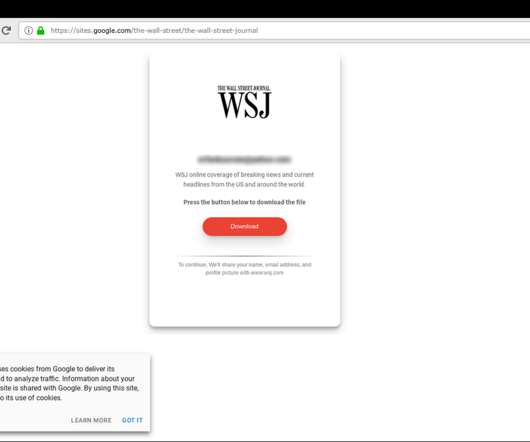
Online scammers are using the 2020 Oscars to spread malware. A recent study released by Kaspersky Labs uncovered several hacking and phishing campaigns promising their targets free and early access to Best Picture nominees for this year’s Academy Awards. The study found over twenty phishing websites hosting at least 925 malicious files using the movies as bait, requiring would-be victims to either provide personal information (including credit card numbers), or to install adware applications to



































Let's personalize your content