5 Ways to Fight School Ransomware Attacks
Dark Reading
MARCH 16, 2023
The challenges are steep, but school districts can fight back with planning.

Dark Reading
MARCH 16, 2023
The challenges are steep, but school districts can fight back with planning.
Krebs on Security
MARCH 17, 2023
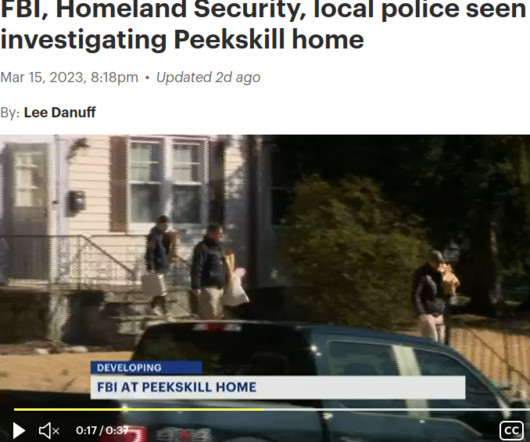
The U.S. Federal Bureau of Investigation (FBI) this week arrested a New York man on suspicion of running BreachForums , a popular English-language cybercrime forum where some of the world biggest hacked databases routinely show up for sale. The forum’s administrator “ Pompompurin ” has been a thorn in the side of the FBI for years, and BreachForums is widely considered a reincarnation of RaidForums , a remarkably similar crime forum that the FBI infiltrated and dismantled in 20
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Joseph Steinberg
MARCH 13, 2023
As pretty much every professional knows, the cyber-threat landscape is constantly and rapidly evolving as hackers discover new techniques to breach organizations. While the introduction of artificial intelligence (AI) is certainly delivering many benefits to mankind, including in the realm of cybersecurity, it has also created all sorts of new risks as evildoers seek to harness AI for their illicit and harmful purposes.

Schneier on Security
MARCH 14, 2023
From Brian Krebs : A Croatian national has been arrested for allegedly operating NetWire, a Remote Access Trojan (RAT) marketed on cybercrime forums since 2012 as a stealthy way to spy on infected systems and siphon passwords. The arrest coincided with a seizure of the NetWire sales website by the U.S. Federal Bureau of Investigation (FBI). While the defendant in this case hasn’t yet been named publicly, the NetWire website has been leaking information about the likely true identity and lo

Advertisement
How many people would you trust with your house keys? Chances are, you have a handful of trusted friends and family members who have an emergency copy, but you definitely wouldn’t hand those out too freely. You have stuff that’s worth protecting—and the more people that have access to your belongings, the higher the odds that something will go missing.

Tech Republic Security
MARCH 15, 2023
AI-generated phishing emails, including ones created by ChatGPT, present a potential new threat for security professionals, says Hoxhunt. The post Humans are still better at creating phishing emails than AI — for now appeared first on TechRepublic.
Krebs on Security
MARCH 14, 2023
Two U.S. men have been charged with hacking into a U.S. Drug Enforcement Agency (DEA) online portal that taps into 16 different federal law enforcement databases. Both are alleged to be part of a larger criminal organization that specializes in using fake emergency data requests from compromised police and government email accounts to publicly threaten and extort their victims.
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.

We Live Security
MARCH 14, 2023
ESET Research uncovered a campaign by APT group Tick against a data-loss prevention company in East Asia and found a previously unreported tool used by the group The post The slow Tick‑ing time bomb: Tick APT group compromise of a DLP software developer in East Asia appeared first on WeLiveSecurity

Tech Republic Security
MARCH 17, 2023
Some 12% of employees take customer details, health records, sales contracts and other confidential data when leaving a company, according to DTEX. The post How to prevent data theft by existing and departing employees appeared first on TechRepublic.
Krebs on Security
MARCH 15, 2023
Microsoft on Tuesday released updates to quash at least 74 security bugs in its Windows operating systems and software. Two of those flaws are already being actively attacked, including an especially severe weakness in Microsoft Outlook that can be exploited without any user interaction. The Outlook vulnerability ( CVE-2023-23397 ) affects all versions of Microsoft Outlook from 2013 to the newest.

Security Boulevard
MARCH 16, 2023
Ben is disappointed: FBI reports huge rise in cryptocurrency investment scams. Why am I not surprised? The post Scams Lost US $10 BILLION in 2022 — Crypto Fraud Grows Fast appeared first on Security Boulevard.

Advertiser: Revenera
In a recent study, IDC found that 64% of organizations said they were already using open source in software development with a further 25% planning to in the next year. Most organizations are unaware of just how much open-source code is used and underestimate their dependency on it. As enterprises grow the use of open-source software, they face a new challenge: understanding the scope of open-source software that's being used throughout the organization and the corresponding exposure.

CyberSecurity Insiders
MARCH 17, 2023
After Rubrik, Hitachi Energy issued a public statement that some of its customer accounts might have been compromised, after a ransomware attack took place on a third-party software called Fortra GoAnywhere MFT. Clop ransomware gang is the company that managed to infiltrate the servers and siphon data and a portion of employee data might have been compromised.

Tech Republic Security
MARCH 13, 2023
A new malware dubbed HiatusRAT infects routers to spy on its targets, mostly in Europe and in the U.S. Learn which router models are primarily targeted and how to protect from this security threat. The post New Hiatus malware campaign targets routers appeared first on TechRepublic.

Graham Cluley
MARCH 17, 2023
Well, this isn’t good. Google has issued a warning that some Android phones can be hacked remotely, without the intended victim having to click on anything.

Bleeping Computer
MARCH 17, 2023
Microsoft is working on a non-custodial built-in Ethereum crypto wallet for Microsoft Edge to allow users to send and receive cryptocurrency and NFTs. [.

Advertisement
The healthcare industry has massively adopted web tracking tools, including pixels and trackers. Tracking tools on user-authenticated and unauthenticated web pages can access personal health information (PHI) such as IP addresses, medical record numbers, home and email addresses, appointment dates, or other info provided by users on pages and thus can violate HIPAA Rules that govern the Use of Online Tracking Technologies by HIPAA Covered Entities and Business Associates.

Security Boulevard
MARCH 14, 2023
Growing interconnectedness makes it harder to detect ransomware before it causes harm. Whether data is processed locally or in the cloud, the risk of a breach is the same. But edge computing also makes it easier for hackers to break in because sensitive data is stored and processed on a wider range of systems. As. The post Using AI Cybersecurity Solutions to Stop Ransomware appeared first on Security Boulevard.

Tech Republic Security
MARCH 13, 2023
By exploiting webcams and other IoT devices, hackers can spy on private and professional conversations, potentially giving them access to sensitive information, says BitSight. The post How internet-facing webcams could put your organization at risk appeared first on TechRepublic.

CSO Magazine
MARCH 13, 2023
Phishing attempts are typically like fishing in a barrel — given enough time, a bad actor is 100% likely to reel in a victim. Once they recognize organizations as habitually vulnerable, they will continue to target them and the barrel-fishing cycle goes on and on. “Bad actors are highly motivated and funded with the sole attempt to be successful at attracting only one victim,” says Johanna Baum, CEO and founder of Strategic Security Solutions Consulting.

Bleeping Computer
MARCH 17, 2023
Hitachi Energy confirmed it suffered a data breach after the Clop ransomware gang stole data using a zero-day GoAnyway zero-day vulnerability. [.

Speaker: Blackberry, OSS Consultants, & Revenera
Software is complex, which makes threats to the software supply chain more real every day. 64% of organizations have been impacted by a software supply chain attack and 60% of data breaches are due to unpatched software vulnerabilities. In the U.S. alone, cyber losses totaled $10.3 billion in 2022. All of these stats beg the question, “Do you know what’s in your software?
Security Boulevard
MARCH 17, 2023
Federal Communications Commission rules to block illegal text messages. What took you so long? The post FINALLY! FCC Acts on SMS Scam-Spam — But Will It Work? appeared first on Security Boulevard.

Tech Republic Security
MARCH 14, 2023
The Premium Ethical Hacking Certification Bundle features eight courses that introduce students to the fundamentals and prepare them to earn important credentials from CompTIA. The post Learn the basics of cybersecurity with this $60 web-based training package appeared first on TechRepublic.
CSO Magazine
MARCH 14, 2023
During every quarter last year, between 10% and 16% of organizations had DNS traffic originating on their networks towards command-and-control (C2) servers associated with known botnets and various other malware threats, according to a report from cloud and content delivery network provider Akamai. More than a quarter of that traffic went to servers belonging to initial access brokers, attackers who sell access into corporate networks to other cybercriminals, the report stated.

Bleeping Computer
MARCH 17, 2023
Ukraine's cyberpolice has arrested the developer of a remote access trojan (RAT) malware that infected over 10,000 computers while posing as game applications. [.

Advertisement
Within the past few years, ransomware attacks have turned to critical infrastructure, healthcare, and government entities. Attackers have taken advantage of the rapid shift to remote work and new technologies. Add to that hacktivism due to global conflicts and U.S. elections, and an increased focus on AI, and you have the perfect recipe for a knotty and turbulent 2024.

SecureWorld News
MARCH 15, 2023
Alright, how many of you saw a cryptocurrency ad on TV in 2022? Oh, yeah, everyone did. How many of you acted on those ads and actually purchased crypto? Probably some of you. Now the important question: how many of you got scammed in some sort of way by cryptocurrency or another type of investment? According to the U.S. Federal Bureau of Investigations (FBI), the answer is a lot of people did.

Tech Republic Security
MARCH 14, 2023
A possible Chinese attack campaign on compromised unpatched SonicWall SMA edge devices stayed undetected since 2021 and could persist even through firmware updates. The post Attack campaign on edge appliance: undetected since 2021 and resists firmware update appeared first on TechRepublic.

Security Boulevard
MARCH 17, 2023
A common misconception of small business owners is that they can fly under the radar when it comes to ransomware, social engineering, and other cyberattacks. But it turns out that the opposite is true. The post The Small Business Fallacy – Why You Need Cybersecurity and Insurance More Than Ever appeared first on Security Boulevard.

Bleeping Computer
MARCH 16, 2023
Microsoft has released a script to make it easier to patch a BitLocker bypass security vulnerability in the Windows Recovery Environment (WinRE). [.

Speaker: Erika R. Bales, Esq.
When we talk about “compliance and security," most companies want to ensure that steps are being taken to protect what they value most – people, data, real or personal property, intellectual property, digital assets, or any other number of other things - and it’s more important than ever that safeguards are in place. Let’s step back and focus on the idea that no matter how complicated the compliance and security regime, it should be able to be distilled down to a checklist.

Dark Reading
MARCH 14, 2023
One researcher thinks trust is broken in AD. Microsoft disagrees that there's a security vulnerability. But enterprise IT environments should be aware of an authentication gap either way.

Tech Republic Security
MARCH 15, 2023
With backing from major firms, credential security company Beyond Identity has launched the Zero Trust Authentication initiative for organizations to hack-proof user credentials. The post For credentials, these are the new Seven Commandments for zero trust appeared first on TechRepublic.

Security Boulevard
MARCH 14, 2023
A new report from the Bipartisan Policy Center ( BPC ) lays out — in stark terms – the prominent cybersecurity risks of the moment. Related: Pres. Biden’s impact on cybersecurity. The BPC’s Top Risks in Cybersecurity 2023 analysis … (more…) The post SHARED INTEL Q&A: Bi-partisan report calls a for a self-sacrificing approach to cybersecurity appeared first on Security Boulevard.

Bleeping Computer
MARCH 17, 2023
U.S. law enforcement arrested on Wednesday a New York man believed to be Pompompurin, the owner of the BreachForums hacking forum. [.

Speaker: William Hord, Vice President of ERM Services
A well-defined change management process is critical to minimizing the impact that change has on your organization. Leveraging the data that your ERM program already contains is an effective way to help create and manage the overall change management process within your organization. Your ERM program generally assesses and maintains detailed information related to strategy, operations, and the remediation plans needed to mitigate the impact on the organization.
Let's personalize your content