To Ease the Cybersecurity Worker Shortage, Broaden the Candidate Pipeline
Dark Reading
SEPTEMBER 14, 2022
With enough passion, intelligence, and effort, anyone can be a successful cybersecurity professional, regardless of education or background.

Dark Reading
SEPTEMBER 14, 2022
With enough passion, intelligence, and effort, anyone can be a successful cybersecurity professional, regardless of education or background.

Krebs on Security
SEPTEMBER 15, 2022
A number of financial institutions in and around New York City are dealing with a rash of super-thin “deep insert” skimming devices designed to fit inside the mouth of an ATM’s card acceptance slot. The card skimmers are paired with tiny pinhole cameras that are cleverly disguised as part of the cash machine. Here’s a look at some of the more sophisticated deep insert skimmer technology that fraud investigators have recently found in the wild.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Schneier on Security
SEPTEMBER 12, 2022
It’s pretty nasty : The malware was dubbed “ Shikitega ” for its extensive use of the popular Shikata Ga Nai polymorphic encoder, which allows the malware to “mutate” its code to avoid detection. Shikitega alters its code each time it runs through one of several decoding loops that AT&T said each deliver multiple attacks, beginning with an ELF file that’s just 370 bytes.

Anton on Security
SEPTEMBER 14, 2022
This blog / mini-paper is written jointly with Oliver Rochford. When we detect threats we expect to know what we are detecting. Sounds painfully obvious, right? But it is very clear to us that throughout the entire history of the security industry this has not always been the case. Some of us remember the early days of the network IDS intrusion detections systems were delivered without customers being able to see how the detections worked .

Advertisement
How many people would you trust with your house keys? Chances are, you have a handful of trusted friends and family members who have an emergency copy, but you definitely wouldn’t hand those out too freely. You have stuff that’s worth protecting—and the more people that have access to your belongings, the higher the odds that something will go missing.

Troy Hunt
SEPTEMBER 15, 2022
I came so close to skipping this week's video. I'm surrounded by family, friends and my amazing wife to be in only a couple of days. But. this video has been my constant companion through very difficult times, and I'm happy to still being doing it at the best of times 😊 So, with that, I'm signing out and heading off to do something much more important.

Lohrman on Security
SEPTEMBER 11, 2022
As we emerge from the most life-changing pandemic in a century, discouraging workplace trends, like "quiet quitting," are commonplace. So what works to improve morale and productivity?
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.

Tech Republic Security
SEPTEMBER 16, 2022
While it's important to implement processes and procedures that safeguard data security and privacy, you can also focus on more strategic data governance goals. The post How does data governance affect data security and privacy? appeared first on TechRepublic.

Troy Hunt
SEPTEMBER 11, 2022
I'm so excited to see the book finally out and awesome feedback coming in, but I'm disappointed with this week's video. I frankly wasn't in the right frame of mind to do it justice (it's been a very hard road up until this point, for various reasons), then my connection dropped out halfway through and I had to roll to 5G, and now I'm hearing (both from other people and with my own ears), a constant background noise being picked up by the mic.

Graham Cluley
SEPTEMBER 16, 2022
Uber has suffered a security breach which allowed a hacker to break into its network, and access the company's internal documents and systems. How did they do it? By bombarding an employee with a spate of multi-factor authentication (MFA) push notifications.

Schneier on Security
SEPTEMBER 16, 2022
It’s big : The breach appeared to have compromised many of Uber’s internal systems, and a person claiming responsibility for the hack sent images of email, cloud storage and code repositories to cybersecurity researchers and The New York Times. “They pretty much have full access to Uber,” said Sam Curry, a security engineer at Yuga Labs who corresponded with the person who claimed to be responsible for the breach. “This is a total compromise, from what it looks like

Advertiser: Revenera
In a recent study, IDC found that 64% of organizations said they were already using open source in software development with a further 25% planning to in the next year. Most organizations are unaware of just how much open-source code is used and underestimate their dependency on it. As enterprises grow the use of open-source software, they face a new challenge: understanding the scope of open-source software that's being used throughout the organization and the corresponding exposure.

Tech Republic Security
SEPTEMBER 16, 2022
One breach of digital trust can cause devastating reputational, regulatory and financial repercussions, according to ISACA’s State of Digital Trust 2022 survey findings. The post Report: Digital trust is critical, but many enterprises are not prioritizing it appeared first on TechRepublic.

Bleeping Computer
SEPTEMBER 10, 2022
Winamp 5.9 Final has been released after four years of development and includes numerous improvements, including Windows 11 support, playback of HTTPS:// streams, and various bug fixes. [.].

Digital Shadows
SEPTEMBER 14, 2022
Although in decline, carding has traditionally been an easy entry point into the world of cybercrime, owing to the low. The post There’s No Honor Among Thieves: Carding Forum Staff Defraud Users in an ESCROW Scam first appeared on Digital Shadows.

CyberSecurity Insiders
SEPTEMBER 16, 2022
According to State of Cloud Security Report compiled by Snyk, over 80% of organizations have suffered cloud security in the past one year and an equal proportion of them have suffered a data breach, but aren’t aware of it due to lack of coordination between teams & policy frameworks, enforcement challenges and budget allotment on time. The report that was compiled after taking the response of over 400 cloud engineers and security analysts concluded that their cloud platforms suffered a varie

Advertisement
The healthcare industry has massively adopted web tracking tools, including pixels and trackers. Tracking tools on user-authenticated and unauthenticated web pages can access personal health information (PHI) such as IP addresses, medical record numbers, home and email addresses, appointment dates, or other info provided by users on pages and thus can violate HIPAA Rules that govern the Use of Online Tracking Technologies by HIPAA Covered Entities and Business Associates.

Tech Republic Security
SEPTEMBER 12, 2022
Some ransomware groups are now using a new method to try to bypass those detections. The post Ransomware makes use of intermittent encryption to bypass detection algorithms appeared first on TechRepublic.

Bleeping Computer
SEPTEMBER 10, 2022
A growing number of ransomware groups are adopting a new tactic that helps them encrypt their victims' systems faster while reducing the chances of being detected and stopped. [.].

Security Affairs
SEPTEMBER 16, 2022
Uber on Thursday disclosed a security breach, threat actors gained access to its network, and stole internal documents. Uber on Thursday suffered a cyberattack, the attackers were able to penetrate its internal network and access internal documents, including vulnerability reports. We are currently responding to a cybersecurity incident. We are in touch with law enforcement and will post additional updates here as they become available. — Uber Comms (@Uber_Comms) September 16, 2022.

CyberSecurity Insiders
SEPTEMBER 13, 2022
Chief Financial Officers aka CFOs are ignoring billions of dollars loss incurred through cyber risks and threats, says a survey. Interestingly, over 87% of survey respondents are over-confident that their companies can overcome any level of threats, although their current Cybersecurity posture was never tested to the core. The survey conducted financial risks evaluator Kroll states that in the past few months, beginning this year of 2022, over 71% of organizations suffered over 5 million financi

Speaker: Blackberry, OSS Consultants, & Revenera
Software is complex, which makes threats to the software supply chain more real every day. 64% of organizations have been impacted by a software supply chain attack and 60% of data breaches are due to unpatched software vulnerabilities. In the U.S. alone, cyber losses totaled $10.3 billion in 2022. All of these stats beg the question, “Do you know what’s in your software?

Tech Republic Security
SEPTEMBER 12, 2022
A new report finds that ransomware attacks are delaying procedures and tests, resulting in poor patient outcomes and increased complications from medical procedures. The post ‘Cyber insecurity’ in healthcare is leading to increased patient mortality rates appeared first on TechRepublic.

Bleeping Computer
SEPTEMBER 14, 2022
Security analysts have found a severe security vulnerability in the desktop app for Microsoft Teams that gives threat actors access to authentication tokens and accounts with multi-factor authentication (MFA) turned on. [.].

Security Affairs
SEPTEMBER 12, 2022
Google completed the acquisition of the threat intelligence firm Mandiant, the IT giant will pay $5.4 billion. Google announced the completion of the $5.4 billion acquisition of threat intelligence firm Mandiant. The acquisition was announced in March 2022 by both companies: “ RESTON, Va., March 8, 2022 – Mandiant, Inc. (NASDAQ: MNDT) today announced that it has entered into a definitive agreement to be acquired by Google LLC for $23.00 per share in an all-cash transaction valued at appro

Digital Shadows
SEPTEMBER 16, 2022
Getting started in any business is a tricky affair. While estimations may vary, it’s widely believed that around 9 in. The post Ransomware franchising: How do groups get started? first appeared on Digital Shadows.

Advertisement
Within the past few years, ransomware attacks have turned to critical infrastructure, healthcare, and government entities. Attackers have taken advantage of the rapid shift to remote work and new technologies. Add to that hacktivism due to global conflicts and U.S. elections, and an increased focus on AI, and you have the perfect recipe for a knotty and turbulent 2024.

Tech Republic Security
SEPTEMBER 13, 2022
These five SASE companies are the leaders in their field. The post Secure Access Service Edge: Trends and SASE companies to watch appeared first on TechRepublic.

Identity IQ
SEPTEMBER 14, 2022
Surya Pochareddy Named Head of M&A and Strategy at IDIQ. IdentityIQ. New role further develops company’s strategic growth across identity and credit solutions. Temecula, California, Sept. 14, 2022 – IDIQ , an industry leader in identity theft protection and credit monitoring, has named Surya Pochareddy to the role of executive vice president, head of M&A and strategy.

The State of Security
SEPTEMBER 16, 2022
Millions of dollars have been stolen from healthcare companies after fraudsters gained access to customer accounts and redirected payments. In a newly-published advisory directed at the healthcare payment industry, the FBI warns that cybercriminals are using a cocktail of publicly-available Personally Identifiable Information (PII) and social engineering techniques to impersonate victims and obtain access to […]… Read More.

Security Affairs
SEPTEMBER 10, 2022
The U.S. Treasury Department sanctioned Iran ‘s Ministry of Intelligence and Security (MOIS) and its Minister of Intelligence over the Albania cyberattack. The U.S. Treasury Department announced sanctions against Iran ‘s Ministry of Intelligence and Security (MOIS) and its Minister of Intelligence over the cyber attack that hit Albania in July.

Speaker: Erika R. Bales, Esq.
When we talk about “compliance and security," most companies want to ensure that steps are being taken to protect what they value most – people, data, real or personal property, intellectual property, digital assets, or any other number of other things - and it’s more important than ever that safeguards are in place. Let’s step back and focus on the idea that no matter how complicated the compliance and security regime, it should be able to be distilled down to a checklist.
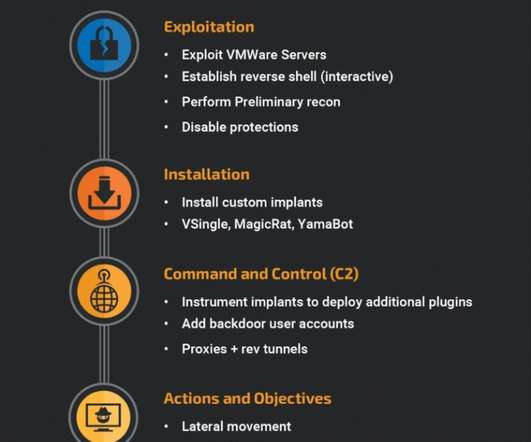
Tech Republic Security
SEPTEMBER 14, 2022
Lazarus, a North Korean cyberespionage group, keeps hitting energy providers in the U.S., Canada and Japan with a new malware arsenal. The post North Korean cyberespionage actor Lazarus targets energy providers with new malware appeared first on TechRepublic.

PCI perspectives
SEPTEMBER 10, 2022
PCI Security Standards Council has published a new Information Supplement: Guidance for Containers and Container Orchestration Tools. This document was produced by the 2021 Special Interest Group (SIG), the members of which provided their expertise and shared experience for applying best practices to containers and container orchestration tools for payment systems.?.
Heimadal Security
SEPTEMBER 16, 2022
The term managed detection and response (MDR) refers to a cybersecurity service that employs advanced technologies and human expertise to carry out threat hunting, monitoring, and response, assisting in diagnosing and minimizing the severity of threats without the necessity of additional employees. A cutting-edge 24/7 security control that frequently consists of a variety of core […].

CSO Magazine
SEPTEMBER 14, 2022
A total 75% of organizations across North America, Asia Pacific and EMEA plan to consolidate the number of security vendors they use, a Gartner survey of 418 respondents found. That percentage has increased significantly, as only 29% were looking to consolidate vendors in 2020. The main reasons are an increase in dissatisfaction with operational inefficiencies and lack of integration of a heterogenous security stack, the survey found.

Speaker: William Hord, Vice President of ERM Services
A well-defined change management process is critical to minimizing the impact that change has on your organization. Leveraging the data that your ERM program already contains is an effective way to help create and manage the overall change management process within your organization. Your ERM program generally assesses and maintains detailed information related to strategy, operations, and the remediation plans needed to mitigate the impact on the organization.
Let's personalize your content