Do you work in the financial sector? Time to step up your cybersecurity habits
Tech Republic Security
APRIL 28, 2017
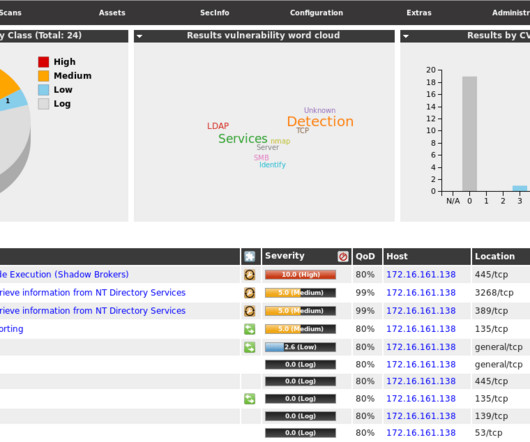
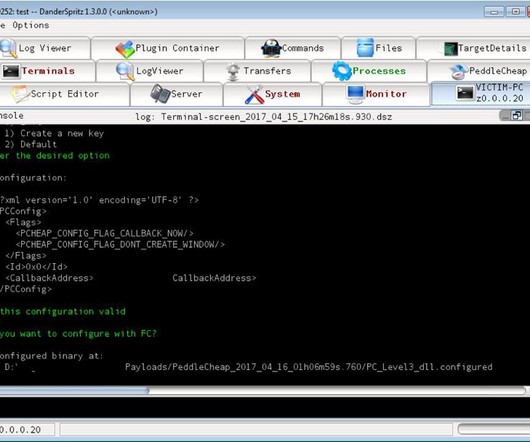
A report from IBM Security revealed a 937% increase in records stolen from the financial sector in 2016. Here's what you need to know and do to protect your sensitive data.





























Let's personalize your content