Vagrant Boxes: Private Vagrant Box Hosting With Easy Versioning
NopSec
MARCH 27, 2015
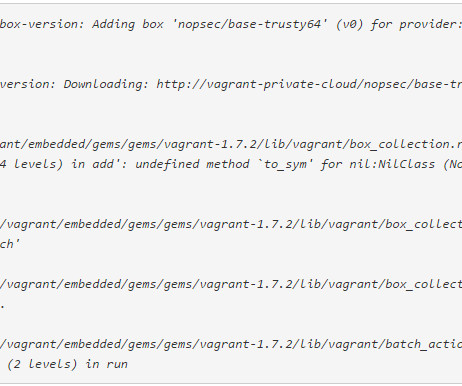
At NopSec, we are using vagrant and packer to spin up local dev environments and build our instances across the various hypervisor and cloud providers we use. We have packer scripts that build our VirtualBox and VMware images used in local development and our various instances used in our cloud providers. An issue I had to solve recently was how best to share development vagrant boxes within our team.










Let's personalize your content