Thinking of a Cybersecurity Career? Read This
Krebs on Security
JULY 24, 2020
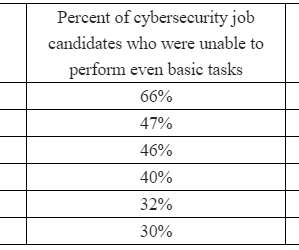
Thousands of people graduate from colleges and universities each year with cybersecurity or computer science degrees only to find employers are less than thrilled about their hands-on, foundational skills. Here’s a look at a recent survey that identified some of the bigger skills gaps, and some thoughts about how those seeking a career in these fields can better stand out from the crowd.


































Let's personalize your content