Ransomware Gangs Now Outing Victim Businesses That Don’t Pay Up
Krebs on Security
DECEMBER 16, 2019
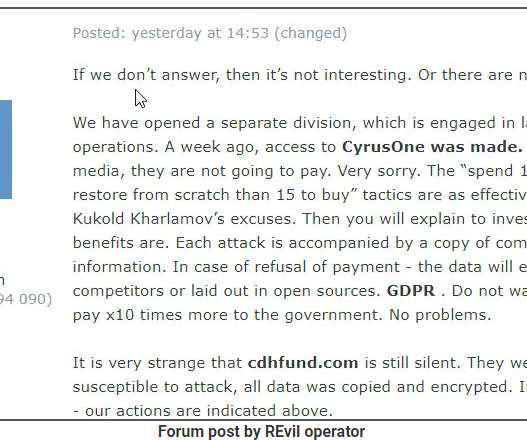
As if the scourge of ransomware wasn’t bad enough already: Several prominent purveyors of ransomware have signaled they plan to start publishing data stolen from victims who refuse to pay up. To make matters worse, one ransomware gang has now created a public Web site identifying recent victim companies that have chosen to rebuild their operations instead of quietly acquiescing to their tormentors.






































Let's personalize your content