LAS VEGAS – Serious vulnerabilities have been disclosed in LeapFrog’s tablet for kids, the LeapPad Ultimate, once again throwing child data privacy into the spotlight.
The LeapPad Ultimate is a rugged tablet made by LeapFrog that targets children with an array of education, game and eBook apps. Researchers, who disclosed the flaws at Black Hat 2019 on Wednesday, said the tablet has a number of security issues opening the door to a slew of malicious activities by an adversary. Those include allowing bad actors to track the devices, send messages to children or launch man-in-the-middle attacks.
“Manufacturers need to realize that the target audience is less suspicious, more naïve, and more likely to miss even simple warning signs of attacks,” Erez Yalon, director of security research at Checkmarx, told Threatpost. “Also, the consequences of privacy breaches may be catastrophic when it comes to children. So as a general rule, manufacturers need to apply the most stringent standards.”
Several flaws circle around a specific in-house app offered by the tablet, Pet Chat, which allows children to talk to each other in a chat room using a pet avatars and some preset phrases and emoticons. Users can only communicate with one another via preset phrases.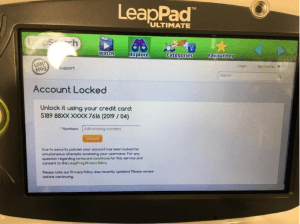
Researchers reported the flaws to LeapFrog in December 2018, and LeapFrog removed the vulnerable app, Pet Chat, from stores in June 2019.
Yalon told Threatpost that while researchers did not request a CVE for the flaw, they considered the impact of the vulnerabilities to be severe. However, there’s no evidence of the flaws being exploited in the wild, he said.
“We thank Checkmarx for bringing these security issues to our attention, as the safety of the children who use our products is a top priority,” said Mari Sunderland, VP of digital product management at LeapFrog in a statement about the flaws. “With the information they provided, we were able to take immediate actions to resolve the issues. Checkmarx has been helpful, ethical, and professional. Cooperating with them has benefited LeapFrog and our customers.”
Pet Chat Issues
Pet Chat has an array of issues that could allow allow malicious actors to either track the tablets or send a “preset” message to the tablet user.
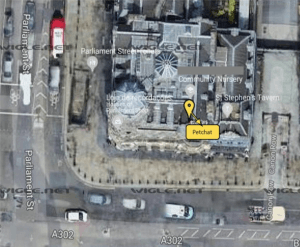 The Pet Chat app creates a Wi-Fi Ad-Hoc connection that broadcasts to other compatible devices nearby using the simple SSID: “Pet Chat.” Researchers were able to use a tool called WiGLE – a website for collecting information about the different wireless hotspots around the globe that puts location and other information in a central database – to identify the tablets.
The Pet Chat app creates a Wi-Fi Ad-Hoc connection that broadcasts to other compatible devices nearby using the simple SSID: “Pet Chat.” Researchers were able to use a tool called WiGLE – a website for collecting information about the different wireless hotspots around the globe that puts location and other information in a central database – to identify the tablets.
That means that “anyone can identify the possible location of LeapPads using Pet Chat by finding them on public Wi-Fi or tracking their device’s MAC address,” said researchers.
In addition, “we discovered that the Pet Chat protocol does not require any authentication between a parent’s device and a child’s device,” said researchers. “This means that any bystander within 100 ft. of a Leapfrog device running Pet Chat can send a message to a child’s device. It is easy to understand the potential implications of that type of activity.”
Luckily, messages are “preset” emojis or messages – however, an attacker could in theory send one of these preset messages for malicious purposes, such as using the preset phrase “Let’s go! play outside together” to persuade a child to go outside.
Researchers said that after they reported the issues to LeapFrog, the company removed the Pet Chat app from stores – however, LeapPad devices that are older than three years may still have the app installed. In that case, researchers advised parents to manually uninstall the app.
Other Flaws
Other flaws were discovered in the kid’s tablet. For instance, researchers said that outgoing traffic from LeapPad was not encrypted using HTTPS but instead the clear-text and less secure HTTP protocol. That makes the tablet vulnerable to Man-in-the-Middle attacks, which could allow a bad actor to intercept traffic and obtain sensitive data such as credit card information as well as personal details about children (name, gender and birthday).
A proof of concept video fo the MiTM attack is in the video below.
https://youtube.com/watch?v=Iygt5Mzf0Bk
Yalon told Threatpost that the resolution of these flaws was more trivial and only required mere code changes: “LeapFrog was very responsive and addressed those during the first wave of fixes,” he said.
It’s only the latest children’s toy to have issues around security and privacy: After CloudPets connected teddy bears were found to have exposed 2.2 million voice recordings between parents and their children in a significant data breach, Amazon, Target and Walmart have pulled the toys from their online markets. Genesis Toys’ My Friend Cayla doll (which was banned in Germany) and Mattel’s Hello Barbie doll have also undergone major security issues.











