Would You Have Fallen for This Phone Scam?
Krebs on Security
APRIL 28, 2020
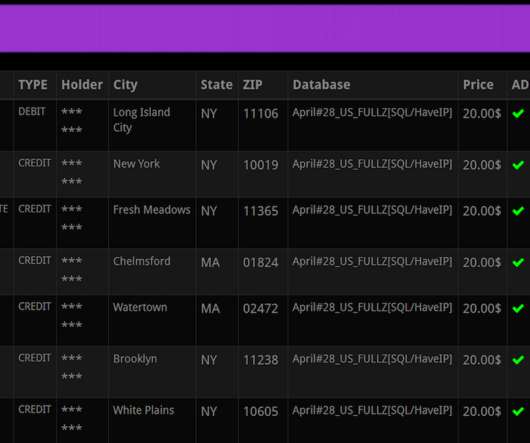
You may have heard that today’s phone fraudsters like to use use caller ID spoofing services to make their scam calls seem more believable. But you probably didn’t know that these fraudsters also can use caller ID spoofing to trick your bank into giving up information about recent transactions on your account — data that can then be abused to make their phone scams more believable and expose you to additional forms of identity theft.






































Let's personalize your content