Customised Ubiquiti Clients and Randomised MAC Addresses on Apple Devices
Troy Hunt
OCTOBER 15, 2020
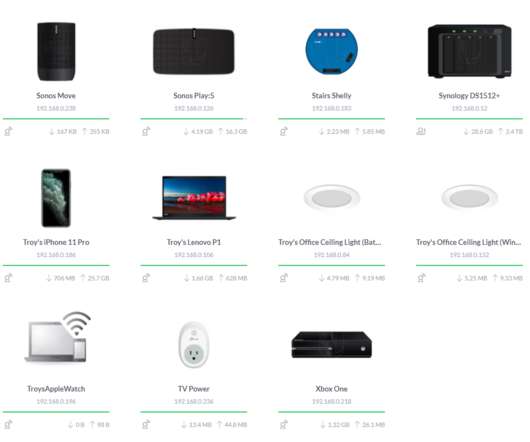
You know how some people are what you'd call "house proud" in that they like everything very neat and organised? You walk in there and everything is in its place, nice and clean without clutter. I'm what you'd call "network proud" and the same principle applies to how I manage my IP things: That's just a slice of my Ubiquiti network map which presently has 91 IP addresses on it between clients and network devices.


































Let's personalize your content