Innovation, Agility and Securing the Mobile World in 2021
Lohrman on Security
FEBRUARY 21, 2021

Tech Republic Security
FEBRUARY 22, 2021
A study on CIO and CISO prioritization showed these two areas are most important this year. Cloud security is another area high on their lists.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.
The Hacker News
FEBRUARY 22, 2021
An ever-evolving and rampant form of cybercrime that targets emails as the potential medium to conduct fraud is known as Business Email Compromise. Targeting commercial, government as well as non-profit organizations, BEC can lead to huge amounts of data loss, security breach, and compromised financial assets.

CSO Magazine
FEBRUARY 23, 2021
Cybersecurity audit fatigue has become a very real issue for organizations that are required to comply with multiple government, industry, and internal requirements.

Advertisement
How many people would you trust with your house keys? Chances are, you have a handful of trusted friends and family members who have an emergency copy, but you definitely wouldn’t hand those out too freely. You have stuff that’s worth protecting—and the more people that have access to your belongings, the higher the odds that something will go missing.

Schneier on Security
FEBRUARY 25, 2021
I am a co-author on a report published by the Hoover Institution: “ Chinese Technology Platforms Operating in the United States.” From a blog post : The report suggests a comprehensive framework for understanding and assessing the risks posed by Chinese technology platforms in the United States and developing tailored responses. It starts from the common view of the signatories — one reflected in numerous publicly available threat assessments — that China’s power is

Tech Republic Security
FEBRUARY 24, 2021
BlackBerry researchers see more double-extortion ransomware attacks, attackers demanding ransom from healthcare patients, and rising bitcoin prices driving the growth of ransomware.
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.

Bleeping Computer
FEBRUARY 26, 2021
A new Ryuk ransomware variant with worm-like capabilities that allow it to spread to other devices on victims' local networks has been discovered by the French national cyber-security agency while investigating an attack in early 2021. [.].

Schneier on Security
FEBRUARY 23, 2021
Alex Birsan writes about being able to install malware into proprietary corporate software by naming the code files to be identical to internal corporate code files. From a ZDNet article : Today, developers at small or large companies use package managers to download and import libraries that are then assembled together using build tools to create a final app.
Tech Republic Security
FEBRUARY 22, 2021
Most organizations don't give the same thought and attention to their non-human workers, such as bots, RPAs and service accounts, as they do human workers and identity lifecycles.
The Hacker News
FEBRUARY 24, 2021
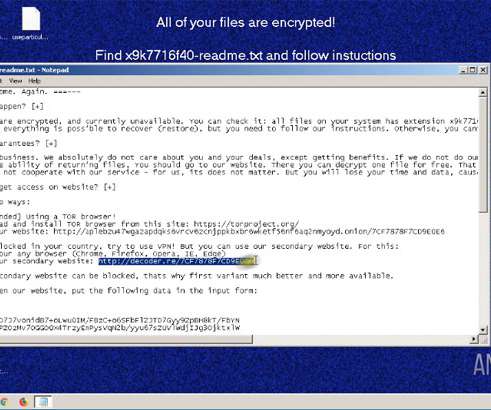
The cybersecurity world is constantly evolving to new forms of threats and vulnerabilities. But ransomware proves to be a different animal—most destructive, persistent, notoriously challenging to prevent, and is showing no signs of slowing down.

Advertiser: Revenera
In a recent study, IDC found that 64% of organizations said they were already using open source in software development with a further 25% planning to in the next year. Most organizations are unaware of just how much open-source code is used and underestimate their dependency on it. As enterprises grow the use of open-source software, they face a new challenge: understanding the scope of open-source software that's being used throughout the organization and the corresponding exposure.

Security Boulevard
FEBRUARY 26, 2021
Almost a year ago, the world turned upside down and seemingly everything changed due to the COVID-19 pandemic. In that time, entire workforces went – and stayed – home, cloud adoption skyrocketed and digital transformation. The post Pandemic Cyber Crime, By the Numbers appeared first on Security Boulevard.

Schneier on Security
FEBRUARY 24, 2021
Researchers found, and Microsoft has patched, a vulnerability in Windows Defender that has been around for twelve years. There is no evidence that anyone has used the vulnerability during that time. The flaw, discovered by researchers at the security firm SentinelOne, showed up in a driver that Windows Defender — renamed Microsoft Defender last year — uses to delete the invasive files and infrastructure that malware can create.

Tech Republic Security
FEBRUARY 23, 2021
DDoS, SQL injection and man-in-the-middle are just a few of the attacks that can compromise your network. Tom Merritt lists five things to know about network attacks.

PCI perspectives
FEBRUARY 26, 2021
Industry feedback is fundamental to the evolution of the PCI Data Security Standard (PCI DSS). Because of the broad impact PCI DSS has on the payment community, the Council is seeking additional feedback into the PCI DSS v4.0 validation documents. As a result of expanding stakeholder feedback opportunities to include these supporting documents, the Council is now targeting a Q4 2021 completion date for PCI DSS v4.0.

Advertisement
The healthcare industry has massively adopted web tracking tools, including pixels and trackers. Tracking tools on user-authenticated and unauthenticated web pages can access personal health information (PHI) such as IP addresses, medical record numbers, home and email addresses, appointment dates, or other info provided by users on pages and thus can violate HIPAA Rules that govern the Use of Online Tracking Technologies by HIPAA Covered Entities and Business Associates.

Security Boulevard
FEBRUARY 23, 2021
The General Data Protection Regulation (GDPR) came into effect on 25th May 2018. Although pertinent to the Personally Identifiable Information (PII) of citizens within the European Economic Area, its effect has reached around the world. As many organisations grappled with updating their data security practices in line with tighter legislation, several questions remained unanswered.

Schneier on Security
FEBRUARY 26, 2021
Excellent Brookings paper: “ Why data ownership is the wrong approach to protecting privacy.” From the introduction: Treating data like it is property fails to recognize either the value that varieties of personal information serve or the abiding interest that individuals have in their personal information even if they choose to “sell” it.

Tech Republic Security
FEBRUARY 25, 2021
The Stanford Internet Observatory alleged that the Chinese government may have had access to audio data from Clubhouse. Here's what users should know.

Bleeping Computer
FEBRUARY 20, 2021
Earlier this week, Microsoft officially announced the Windows 10 version 21H1 update and it'll begin rolling out to consumers in the first half of this year. Like the October 2020 Update (20H2), this new update also comes with a minimal set of features, general improvements, and bug fixes. [.].

Speaker: Blackberry, OSS Consultants, & Revenera
Software is complex, which makes threats to the software supply chain more real every day. 64% of organizations have been impacted by a software supply chain attack and 60% of data breaches are due to unpatched software vulnerabilities. In the U.S. alone, cyber losses totaled $10.3 billion in 2022. All of these stats beg the question, “Do you know what’s in your software?

Digital Shadows
FEBRUARY 22, 2021
Over the course of 2020, Digital Shadows detected over 500 cybercriminals’ listings advertising network access across a multitude of industry. The post The Rise of Initial Access Brokers first appeared on Digital Shadows.

Schneier on Security
FEBRUARY 22, 2021
Really good op-ed in the New York Times about how vulnerable the GPS system is to interference, spoofing, and jamming — and potential alternatives. The 2018 National Defense Authorization Act included funding for the Departments of Defense, Homeland Security and Transportation to jointly conduct demonstrations of various alternatives to GPS, which were concluded last March.

Tech Republic Security
FEBRUARY 22, 2021
Known as Silver Sparrow, the malware's intent is still unknown as it has yet to deliver an actual payload, says security firm Red Canary.

Security Boulevard
FEBRUARY 24, 2021
Sysdig announced today it has donated a sysdig kernel module, along with libraries for the Falco security platform for Kubernetes, to the Cloud Native Computing Foundation (CNCF) as part of an effort to advance Linux security. The sysdig kernel module runs in the extended Berkeley Packet Filter (eBPF) microkernel created by the Linux community to. The post Sysdig Donates eBPF to CNCF to Improve Linux Security appeared first on Security Boulevard.

Advertisement
Within the past few years, ransomware attacks have turned to critical infrastructure, healthcare, and government entities. Attackers have taken advantage of the rapid shift to remote work and new technologies. Add to that hacktivism due to global conflicts and U.S. elections, and an increased focus on AI, and you have the perfect recipe for a knotty and turbulent 2024.

Bleeping Computer
FEBRUARY 26, 2021
American telecommunications provider T-Mobile has disclosed a data breach after an unknown number of customers were apparently affected by SIM swap attacks. [.].

SC Magazine
FEBRUARY 22, 2021
Craig Froelich, chief information security officer of Bank of America Merrill Lynch, described how cybersecurity is not just a technology risk during a 2017 annual meeting of the Securities Industry and Financial Markets Association. (SIFMA). Diversity and inclusion programs gained a great deal of traction in the last few years as a means of hiring minorities, women and other underrepresented members of the modern security workforce.

Tech Republic Security
FEBRUARY 23, 2021
These eight online courses teach the fundamentals you need to pass various IT and cybersecurity certification exams from Cisco and CompTIA.

Security Affairs
FEBRUARY 20, 2021
Sequoia Capital, one of the most prominent venture capital firms, told its investors that an unauthorized third party had access to their information. Sequoia Capital, one of the most prominent venture capital firms that focus on the technology industry, discloses a data breach. The company informed its investors that an unauthorized third party had access to their personal and financial information.

Speaker: Erika R. Bales, Esq.
When we talk about “compliance and security," most companies want to ensure that steps are being taken to protect what they value most – people, data, real or personal property, intellectual property, digital assets, or any other number of other things - and it’s more important than ever that safeguards are in place. Let’s step back and focus on the idea that no matter how complicated the compliance and security regime, it should be able to be distilled down to a checklist.

Bleeping Computer
FEBRUARY 23, 2021
Mozilla Firefox 86 was released today with Total Cookie Protection, a new privacy feature that prevents web trackers from keeping tabs on your activity while browsing the web. [.].

Security Boulevard
FEBRUARY 24, 2021
In mid-February 2021, the Department of Justice shared the content of what had been a sealed indictment charging three North Korean (DPRK) hacking “operatives” with a plethora of cybercrimes, including “cyber heists and extortion schemes, targeting both traditional and cryptocurrencies.” Assistant Attorney General John C. Demers remarked, “The indictment refines the attribution of this crime.

Tech Republic Security
FEBRUARY 24, 2021
A new FlexJobs survey reveals 14 of the most common--and successful--job-search scams. Here's how to identify them and not become a victim.

SecureList
FEBRUARY 25, 2021
Lazarus targets defense industry with ThreatNeedle (PDF). We named Lazarus the most active group of 2020. We’ve observed numerous activities by this notorious APT group targeting various industries. The group has changed target depending on the primary objective. Google TAG has recently published a post about a campaign by Lazarus targeting security researchers.

Speaker: William Hord, Vice President of ERM Services
A well-defined change management process is critical to minimizing the impact that change has on your organization. Leveraging the data that your ERM program already contains is an effective way to help create and manage the overall change management process within your organization. Your ERM program generally assesses and maintains detailed information related to strategy, operations, and the remediation plans needed to mitigate the impact on the organization.
Let's personalize your content