5 IT security strategies that you should think about as employees return to the office
CyberSecurity Insiders
MAY 5, 2021
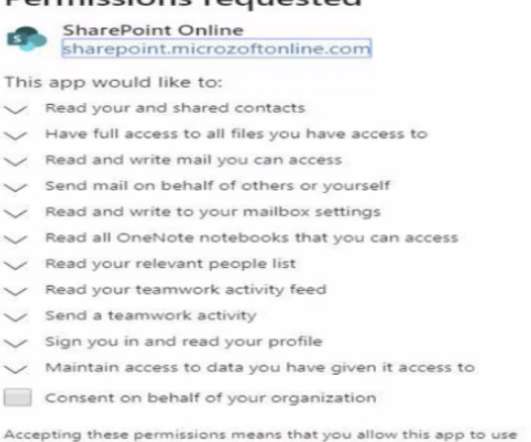
This blog was written by an independent guest blogger. Without a doubt, digital transformation accelerated amid the pandemic and made it possible for employees to work remotely. However, it also intensified the threat landscape created by malicious attackers who jumped on the first opportunity to attack the more vulnerable home networks. As remote working becomes the new norm, it is paramount to have an agile infrastructure and team for security.








































Let's personalize your content