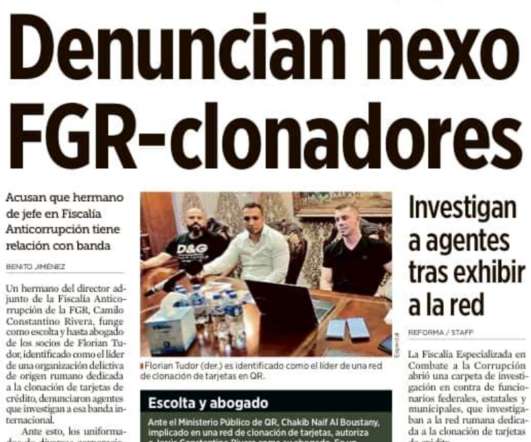
Report: ATM Skimmer Gang Had Protection from Mexican Attorney General’s Office
Krebs on Security
MAY 26, 2020
A group of Romanians operating an ATM company in Mexico and suspected of bribing technicians to install sophisticated Bluetooth-based skimmers in cash machines throughout several top Mexican tourist destinations have enjoyed legal protection from a top anti-corruption official in the Mexican attorney general’s office, according to a new complaint filed with the government’s internal affairs division.


































Let's personalize your content