UPDATE
A researcher is warning that a WhatsApp feature called “Click to Chat” puts users’ mobile phone numbers at risk — by allowing Google Search to index them for anyone to find. But WhatsApp owner Facebook says it is no big deal and that the search results only reveal what the users have chosen to make public anyway.
Bug-bounty hunter Athul Jayaram, who discovered the issue, calls the phone numbers “leaked” and characterizes the situation as a security bug that puts WhatsApp users’ privacy at risk.
Click to Chat offers websites an easy way to initiate a WhatsApp chat session with website visitors. It works by associating a Quick Response (QR) code image (created via third-party services) to a site owner’s WhatsApp mobile phone number. That allows a visitor to scan the site’s QR code or click on a URL to initiate a WhatsApp chat session – without the visitor having to dial the number itself. That visitor however still gains access to the phone number once the call is initiated.
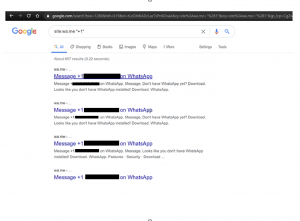
The problem, Jayaram said, is that those mobile numbers can also turn up in Google Search results, because search engines index Click to Chat metadata. The phone numbers are revealed as part of a URL string (https://wa.me/<phone_number>) and so, this in effect “leaks” the mobile phone numbers of WhatsApp users in plaintext, according to the researcher’s view.
The “wa.me” domain is owned and maintained by WhatsApp, according to WHOIS records.
“Your mobile number is visible in plain text in this URL, and anyone who gets hold of the URL can know your mobile number. You cannot revoke it,” said Jayaram, in research shared exclusively with Threatpost, Friday.
He argues that it makes it easier for spammers to compile legitimate phone numbers to mount campaigns. Using a specially crafted search string of the domain https://wa.me/, the researcher said he found that Google indexed 300,000 WhatsApp phone numbers.
Jayaram argues that because of this, Click to Chat presents an important security issue that could lead to abuse and fraud.
“As individual phone numbers are leaked, an attacker can message them, call them, sell their phone numbers to marketers, spammers, scammers,” he said.
Because WhatsApp identifies users by phone numbers (as opposed to usernames or email IDs), Google Search only revealed the phone numbers and not the identities of users that they were connected to, Jayaram explained. However, the researcher said he was also able to see users’ profile pictures on WhatsApp along with their phone numbers, merely by clicking on the Google Search phone number URLs, which brought him to their WhatsApp profiles. Next, a determined hacker could reverse-image search the user’s profile picture in hopes of collecting enough clues to establish the user’s identity.
“Through the WhatsApp profile, they can see the profile photo of the user, and a do reverse-image search to find their other social-media accounts and discover a lot more about about [a targeted individual],” he told Threatpost.
Pairing a phone number with a name and address could be a powerful starting point for an identity thief, according to Jayaram. “Most users do use the same profile picture on other social media accounts, the user profiles can be also easily find out,” he said.
For its part, WhatsApp describes Click to Chat as a convenience perk, allowing users to begin a chat with someone without having their phone number saved in their phone’s address book.
 “Our Click to Chat feature, which lets users create a URL with their phone number so that anyone can easily message them, is used widely by small and microbusinesses around the world to connect with their customers,” a WhatsApp spokesperson told Threatpost.
“Our Click to Chat feature, which lets users create a URL with their phone number so that anyone can easily message them, is used widely by small and microbusinesses around the world to connect with their customers,” a WhatsApp spokesperson told Threatpost.
In a Tuesday Tweet, Jayaram said a “fix” for the http://wa.me domain has been issued and phone numbers are not searchable anymore.
Feature or Bug?
The researcher maintains that many Click to Chat users are unaware that their phone numbers are being stored in plaintext, indexed by Google Search and discoverable via a relatively simple search query.
He told Threatpost that users he reached out to had expressed concern their phone numbers were available online and indexed by Google Search.
Threatpost also reached out to several WhatsApp users whose numbers were indexed by Google Search — some were aware that their number was public — and had made it that way to promote their business or personal contact online.
“My phone number is public on the web. No need to implicate WhatsApp,” one user told Threatpost, explaining that Click to Chat was convenient and made it easy for his site visitors. “I did it to make it easy for people to contact me. Surprisingly, I get very few spam calls,” he said.
However, others were unaware their numbers were public.
“No I didn’t mean to make my number public at all,” one user told Threatpost. “I set up WhatsApp for my business so people should text directly without getting my number.”
Rejected for Bug Bounty
After discovering the issue on May 23, Jayaram said he contacted WhatsApp owner Facebook regarding the issue via its bug-bounty program. However, Facebook responded to him saying that data abuse is only covered for Facebook platforms, and not for WhatsApp. A WhatsApp spokesperson on the other hand told Threatpost that WhatsApp is a part of the data-abuse bounty program.
“While we appreciate this researcher’s report and value the time that he took to share it with us, it did not qualify for a bounty since it merely contained a search engine index of URLs that WhatsApp users chose to make public. All WhatsApp users, including businesses, can block unwanted messages with the tap of a button,” he said.
Old Problem, New Complaints
Google search indexes were also central to a WhatsApp glitch uncovered earlier this year, after a journalist for DW News found that invite links for WhatsApp groups were being indexed by Google’s Search Engine. That meant that if links to private groups existed anywhere on the internet, anyone could potentially find them and join a WhatsApp group with a quick Google search. Hundreds of thousands of groups were potentially accessible in this way.
At the time, Danny Sullivan, public liaison for Google Search, said on Twitter that the situation is “no different than any case where a site allows URLs to be publicly listed,” but said that Google does offer tools allowing sites to block content being listed.
https://twitter.com/dannysullivan/status/1230920851849003008
A Google spokesperson told Threatpost that in regards to Google Search, what Sullivan said still holds true. According to Google, it and other search engines index pages that are available on the open web. Google cannot remove URLs from the web (only webmasters can do that), so even if something is removed from Google’s results, it can still appear in the results of other search engines.
Jayaram recommended that WhatsApp encrypt user mobile numbers, and add a robots.txt file to disallow bots from crawling their domain.
“Unfortunately they did not do that yet, and your privacy may be at stake,” he said. “Today, your mobile number is linked to your Bitcoin wallets, Adhaar, bank accounts, UPI, credit cards…[allowing] an attacker to perform SIM card swapping and cloning attacks by knowing your mobile number is another possibility.”
This article was updated on June 9 to reflect that the issue has been fixed and the phone numbers are no longer searchable.











