Contents:
The FritzFrog botnet, which has been operative for more than two years, has reemerged with a concerning infection rate, having grodawn tenfold in just a month after compromising medical, education, and government systems via a vulnerable SSH server.
The malware was noticed in August 2020 and is written in the Golang programming language.
As explained by BleepingComputer, the FritzFrog botnet is regarded as an advanced cyber threat that relies on custom code, runs in memory, and is decentralized – peer-to-peer (P2P), so it does not necessitate a central management server.
According to cybersecurity experts at Akamai Threat Labs, the botnet has resurfaced with a rapid growth surge since December, despite having disappeared quietly following its previous attack wave.
They said the new FritzFrog malware variant includes some intriguing new features, such as the ability to use the Tor proxy chain, and also indicates that its developers are planning to add capabilities to attack WordPress servers.
The actors have implemented a filtering list to skip low-powered devices such as Raspberry Pi boards, while the malware now contains code that lays the groundwork for targeting WordPress sites.
Given the botnet’s reputation for cryptocurrency mining, this feature is an odd addition. However, Akamai believes the hackers have found other ways to make money, such as ransomware or data leaks. This capability is currently inactive while it is being developed.
FritzFrog Botnet – a Rising “Star”
The researchers refer to FritzFrog as a “next-generation” botnet since it integrates characteristics that set it apart from other threats in the same category.
FritzFrog updates the list of targets and compromised devices on a regular basis, and its node distribution system ensures that each node has an equal number of targets to keep the botnet balanced.
New Attacks
Even though Akamai’s global network of sensors detected 24,000 attacks, the botnet has only claimed 1,500 victims so far. The majority of the infected hosts are located in China, but compromised systems can also be found in a European TV network, a Russian healthcare organization, and several East Asian universities.
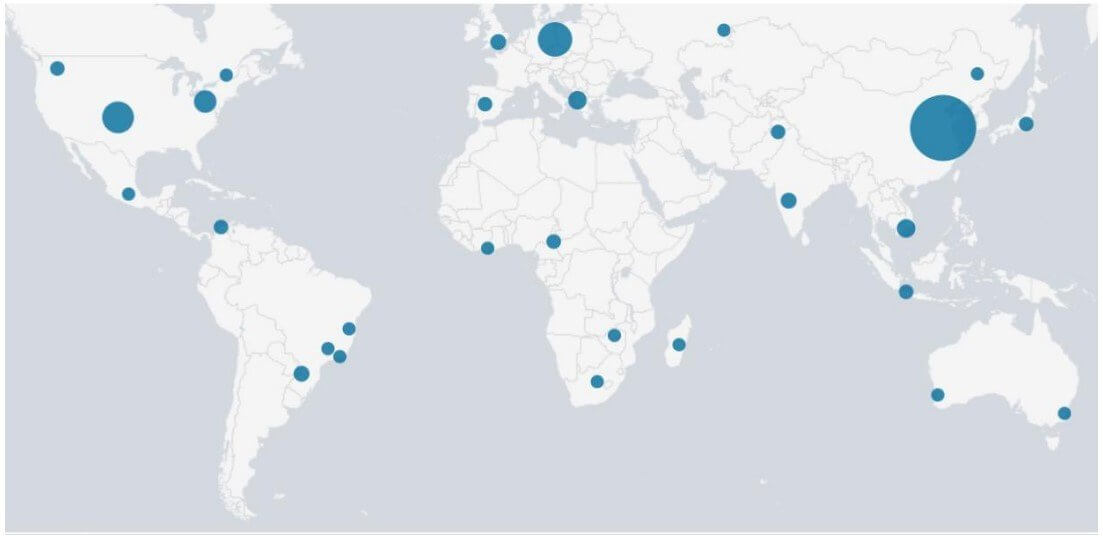
The researchers point out that FritzFrog is constantly in development, with new vulnerabilities being fixed daily, multiple times a day.
Another new feature in the most recent FritzFrog version is the proxying of outgoing SSH connections through Tor, which hides the network structure and limits visibility to the botnet network from infected nodes. Despite the fact that this feature appears to be fully functional, the creators have yet to activate it.
Also, the copying system (which is used to infect new systems) is now based on SCP (security copy protocol), which replaces the cat command from the previous variant.
Who’s Behind the Backdoor?
Although Akamai researchers do not have a precise attribution for FritzFrog’s operation, the indications point to China.
Because the malware contains distinct code components, some of it can be traced back to unique GitHub repositories set up by Shanghai-based users. Furthermore, the wallet addresses associated with the second campaign’s mining activities were also used in the Mozi botnet, which was later confirmed to be Chinese.
Finally, approximately 37% of FritzFrog’s active nodes are in China, suggesting that the actor is based there.
Recommendations from the Researchers
FritzFrog is after any device that exposes an SSH server, so data center, cloud instance, and router administrators should be on the lookout. Here are Akamai’s recommendations:
- Enable system login auditing with alerting
- Monitor the authorized_hosts file on Linux
- Configure explicit allow list of SSH login
- Disable root SSH access
- Enable cloud-based DNS protection with threats and unrelated business applications such as coin mining set to block
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










