While industrial control systems (ICS) are the most talked-about when it comes to cyberattacks against energy and utilities firms, most attacks actually take aim at the enterprise IT networks used by these organizations, rather than critical infrastructure itself.
The Vectra 2018 Spotlight Report on Energy and Utilities shows that cyberattackers mainly look to spy and steal information from the energy and utility sectors, to be used in carefully orchestrated attack campaigns that tend to unfold over many months.
“There is a difference between attacks that probe IT networks for information and access about critical infrastructure versus attacks against the ICS on which the critical infrastructure operates,” according to the report. “The two are interconnected, but the targeted assets are different. These slow, quiet reconnaissance missions involve observing operator behaviors and building a unique plan of attack. The attack that shut down the Ukraine power grid in 2015 was reportedly planned many months in advance by highly skilled and sophisticated cybercriminals.”
Remote attackers typically gain a foothold in energy and utilities networks by staging malware and spear-phishing to steal administrative credentials. Once inside, they use administrative connections and protocols to perform reconnaissance and spread laterally in search of confidential data about ICS.
Administrative protocols are a favorite tool of attackers because they allow cybercriminals to move laterally inside networks where they have already established a durable foothold.
“Because administrative connections are typically used in conjunction with administrative credentials, attackers often have unconstrained access to systems and data that are critical to energy and utilities organizations,” Vectra explained in its report. “Unexpected and unexplained administrative connections represent a huge potential risk in the lifecycle of a major breach.”
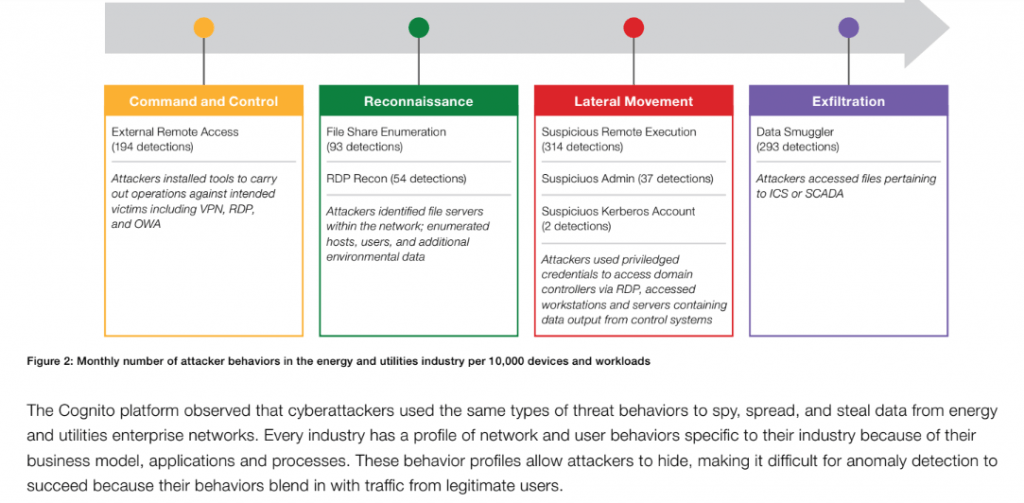
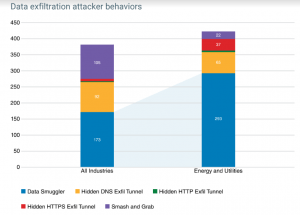
The report is based on telemetry collected between January and June 2018 from over 250 enterprise organizations in energy and utilities. In terms of attack frequency, the data showed that, per each 10,000 host devices and workloads, 194 malicious external remote access behaviors were detected during the command-and-control phase of attack. About 314 lateral movement attack behaviors were also detected; and, in the exfiltration phase of the cyberattack lifecycle, 293 data-smuggling behaviors were detected per 10,000 host devices and workloads.
With external remote access, attackers directly control host devices rather than using an automated form of command-and-control, according to the report.
“Energy and utilities organizations use forms of remote access technology to improve productivity and it can be a legitimate command-and-control behavior,” it noted. “However, the presence of remote network access traffic introduces a risk because it enables attackers to blend in while performing the same types of external remote access for nefarious deeds. This is especially true when attackers leverage commonly-used remote access tools like [VPNs].”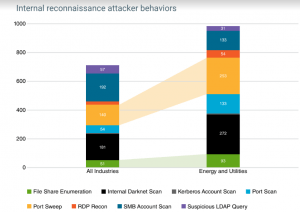
On the reconnaissance front, the Vectra platform detected 93 file-share enumeration attempts in energy and utilities per 10,000 host devices and workloads. File-share enumeration behaviors occur when a host device accesses inordinately more file-shares than normal.
“Enumeration might indicate a host device is accessing many file-shares as a user attempts to find a file or directory. However, enumerating file-shares on a network is also an effective way for attackers to find data to exfiltrate or data that helps further the attack,” the report said.
Meanwhile, the most common lateral movement behaviors inside energy and utilities companies were suspicious remote execution.
“The server message block (SMB) channel allows the copying of executables and executing them via remote procedure call (RPC),” according to the report. “Systems that are authorized to perform remote execution should be monitored because they enable attackers to hide in plain sight.”