Psychological Manipulation in Social Engineering: Unveiling the Tactics
Have you ever found yourself in a situation where you felt like someone was trying to manipulate you into doing something you didn’t want to do? Perhaps it was a friend, family member, or even a stranger. The truth is, we all encounter people who try to influence our behavior or decisions from time to time. But what happens when these tactics cross the line into psychological manipulation? Social engineers use a variety of tactics to manipulate individuals and organizations for their own gain, and the results can be devastating. From phishing scams to social media manipulation, it is crucial that we understand these tactics and learn how to protect ourselves from them. In this article, we will explore the world of social engineering, and provide you with practical tips on how to spot and avoid psychological manipulation. So, buckle up and get ready to learn how to protect yourself from these dangerous tactics.
Types of Social Engineering Tactics
Social engineering attacks can take many forms, and attackers use a wide range of tactics to achieve their goals. Here are some of the most common tactics used by social engineers:
- Phishing Scams: They are the most common type of social engineering attack. Attackers use email, text messages, or phone calls to trick individuals into revealing sensitive information or clicking on a link that will download malware onto their computer. Phishing scams can be highly effective because they often appear to come from a trusted source, such as a bank or an online retailer.
- Baiting: It is a social engineering tactic that involves offering something of value, such as a free gift card or a USB drive, in exchange for sensitive information. The attacker may leave the USB drive in a public place, such as a coffee shop, in the hopes that someone will pick it up and plug it into their computer.
- Pretexting: It is a tactic used by social engineers to create a false sense of trust with their target. The attacker will create a scenario that requires the target to reveal sensitive information, such as a password or a social security number. For example, the attacker may pose as an IT support technician and ask the target to provide their login credentials.

Common Psychological Manipulation Techniques
Social engineers use a variety of psychological manipulation techniques to influence their targets. These techniques are designed to exploit our natural human tendencies and emotions, such as fear, greed, and trust. Here are some of the most common psychological manipulation techniques used by social engineers:
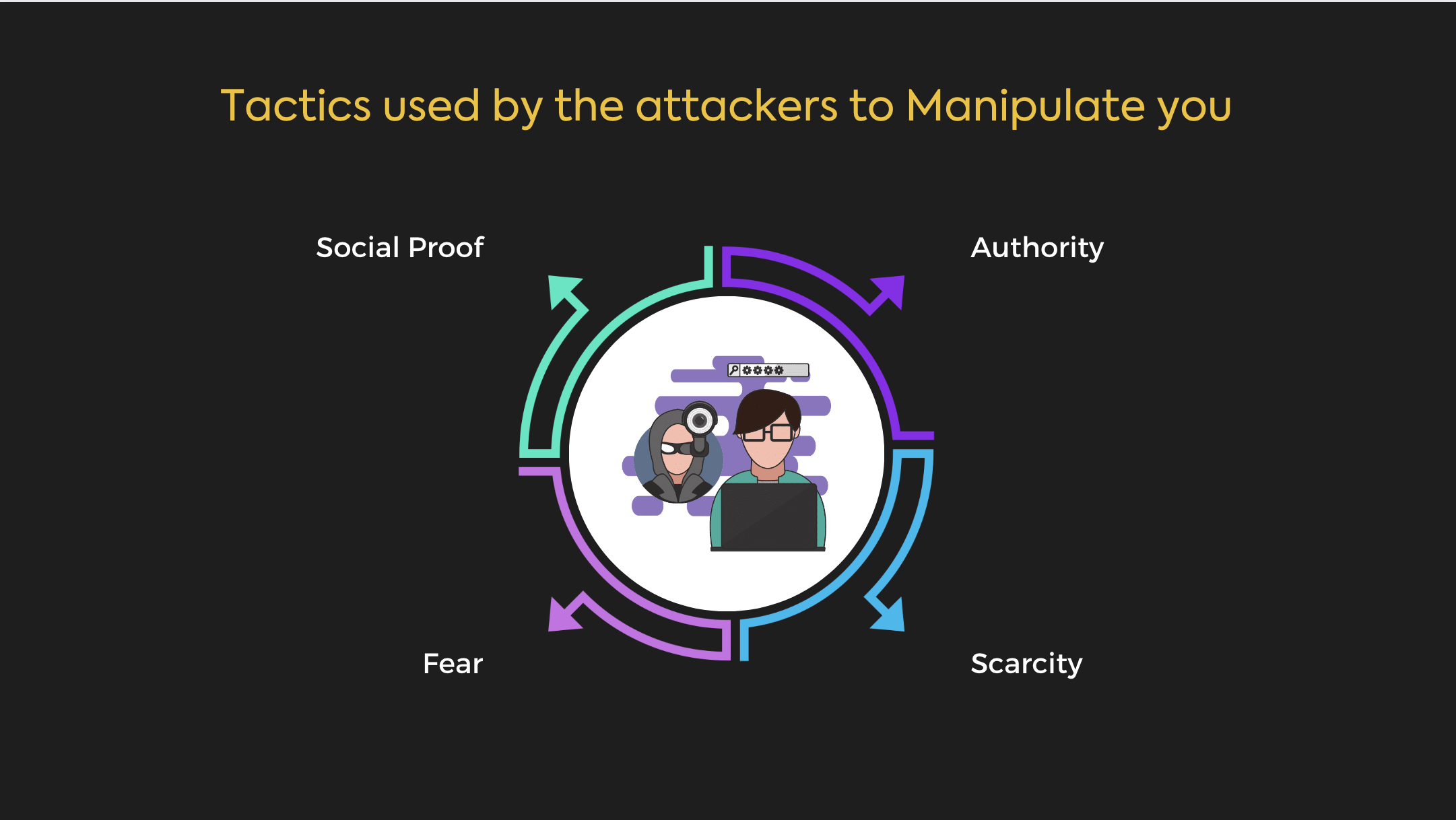
- Authority
Social engineers may use their perceived authority to manipulate their targets. For example, an attacker may pose as a police officer or a government official to gain the trust of their target. - Scarcity
Scarcity is a tactic that involves creating a sense of urgency or scarcity to encourage the target to take action. For example, an attacker may claim that there are only a few spots left in a limited-time offer to encourage the target to act quickly. - Social Proof
Social proof is a tactic that involves using the opinions or actions of others to influence the target. For example, an attacker may claim that many other people have already taken advantage of a particular offer to encourage the target to do the same. - Fear
Fear is a tactic in which threat actors create a sense of fear to make the victim act impulsively. They claim that the victim’s computer has been infected with a virus or that their personal information has been compromised.
Red Flags to Look Out For
While social engineering attacks can be highly effective, there are often red flags that can help you identify them. Here are some red flags to look out for:
- Urgency
Social engineering attacks often involve a sense of urgency or scarcity. If you feel like you are being pressured to act quickly, it may be a sign of a social engineering attack. - Suspicious Links or Attachments
Phishing scams often involve links or attachments that are designed to download malware onto your computer. If you receive an email or message with a suspicious link or attachment, be cautious. - Requests for Sensitive Information
Social engineers may request sensitive information, such as a password or a social security number. Be cautious when providing sensitive information, and always verify the identity of the person or organization requesting it.
Real-Life Examples of Social Engineering Attacks
There are many real-life examples of social engineering attacks that have had devastating consequences. Here are a few examples:
2022 Attack on Uber
A threat actor used Uber’s Internal Slack Platform to impersonate an employee and gain internal network access. They posted an explicit image and it’s believed that they escalated privileges and viewed sensitive information. This threat actor admitted their conquest and said they used social engineering to easily penetrate Uber’s security protocols.
2022 Attack on Twilio
The threat actor gained access to private customer and employee account information by stealing an employee password. This was done through a broad-based social engineering attack that involved sending fake IT text messages to Twilio employees.
2022 Attack on Rockstar Games
The social engineering attack on Rockstar Games was similar to what happened to Uber, and it happened just a few days after Uber’s fiasco by the same threat actor. Once inside the internal Slack channel of Rockstar Games, TeaPot claimed he was able to access code for the then unannounced sequel to the game, Grand Theft Auto.
How to Protect Yourself from Social Engineering Attacks
Protecting yourself from social engineering attacks requires a multi-pronged approach. Here are some steps you can take to protect yourself:
- Be Cautious Online
Be cautious when clicking on links or downloading attachments, particularly if they are from an unknown source. Use strong, unique passwords for each of your online accounts, and enable two-factor authentication whenever possible. - Verify Requests for Sensitive Information
Before providing sensitive information, always verify the identity of the person or organization requesting it. If you receive a call or email requesting sensitive information, hang up or delete the email and contact the organization directly to verify the request. - Stay Up-to-Date on Security Best Practices
Stay up-to-date on the latest security best practices, such as enabling automatic updates for your software and using anti-virus software to protect your computer from malware. - Creating a Security Plan for Personal and Professional Use
Creating a security plan for personal and professional use is an important step in protecting yourself from social engineering attacks. Here are some steps you can take to create a security plan: - Conduct a Risk Assessment
Conduct a risk assessment to identify potential vulnerabilities and threats to your personal or professional security. This will help you to prioritize your security measures and allocate resources accordingly. - Establish Security Policies and Procedures
Establish security policies and procedures to govern your personal or professional security. This should include guidelines for password management, access control, and incident response. - Train Employees
If you are creating a security plan for your workplace or family, it is important to train employees or family members on security best practices. This will help to ensure that everyone is on the same page when it comes to security. - Importance of Education and Awareness
Education and awareness are key to protecting yourself from social engineering attacks. By educating yourself and your employees or family members on the tactics used by social engineers, you can help to prevent these attacks from being successful. It is important to stay up-to-date on the latest security best practices and to be vigilant when it comes to suspicious activity.
Conclusion
Social engineering attacks are a serious threat to both individuals and organizations. By understanding the tactics used by social engineers and taking steps to protect yourself, you can reduce your risk of falling victim to these attacks. Remember to be cautious online, verify requests for sensitive information, and stay up-to-date on the latest security best practices. With these tips in mind, you can protect yourself and your organization from the potentially devastating consequences of social engineering attacks.
The post Psychological Manipulation in Social Engineering: Unveiling the Tactics appeared first on WeSecureApp :: Simplifying Enterprise Security.
*** This is a Security Bloggers Network syndicated blog from WeSecureApp :: Simplifying Enterprise Security authored by Khushboo Chahal. Read the original post at: https://wesecureapp.com/blog/psychological-manipulation-in-social-engineering-unveiling-the-tactics/




