Operational Resilience Regulations for Financial Services – The Role of CRQ
The Australian Prudential Regulatory Authority (APRA) is the latest financial regulator to release proposed regulations regarding operation resilience[i], prompting me to collect my thoughts on how a Balbix-style cyber risk quantification (CRQ) solution could help meet these regulatory obligations.
A brief history
For those of you not familiar with financial services regulation, or the operational resilience requirements that have been emerging over recent years, here’s a brief history.
As ever, regulation tends to follow lived experience; where harm to customers or to the financial system has occurred and regulatory bodies find themselves needing to introduce requirements to protect consumers and the financial system. This was the case in 2017 where, on the back of a number of high-profile incidents – including Wannacry, and the Equifax leak – G20 finance ministers and central bank governors determined that cyber risk had the potential to disrupt the financial system on a supranational scale.
Furthermore, in the UK, it was determined that a number of major disruptions to customers were caused by poorly managed IT upgrade programmes at a number of high-street banks. This led to the publication of a discussion paper on Building Operational Resilience by the Bank of England[ii] and the establishment of a working group by the Basel committee on Banking supervision.[iii] Eventually, the Bank of England[iv] and the Basel Committee[v] issued their Operational Resilience Policy in March 2021. Since then, a number of financial regulators around the globe have either released similar policies, or are in the process of doing so.
What is operational resilience?
So what is operational resilience and what are the requirements being placed on financial services firms? The Basel Committee defines operational resilience as the “ability of a bank to deliver critical operations through disruptions.”[vi] The Bank of England takes this a step further and explains that operational resilience refers to the, “ability of firms, financial market infrastructures (FMIs), and the sector as a whole to prevent, respond to, recover and learn from operational disruptions.”[vii]
Similarly, the discussion paper recently released by the Australian Prudential Regulation Authority (APRA) places operational resilience at the heart of good operational risk management. In doing so, operational resilience is seen as minimizing the potential impact of events and ensuring that “entities can continue to operate through disruption and provide key services to customers.”[viii]
Operational resilience regulation in practice
All good stuff, but what do these regulations mean in practice for regulated firms? In the UK, the policy released in 2021 requires firms to:
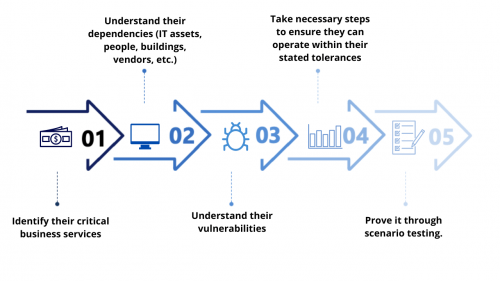
- Identify and map important business services
- Identify any vulnerabilities in their operational resilience
- Set impact tolerances for each important business service
- Undertake scenario testing to validate impact tolerances
- Demonstrate through testing their ability to remain within impact tolerances
Firms were given until 2025 to demonstrate full compliance, but initial identification, mapping and tolerance setting had to be completed by March 2022.
In Europe, the EU’s Digital Operational Resilience Act will similarly require firms to identify their “critical or important functions” and map their assets and dependencies. It too requires firms to set risk tolerances for information and communications technology (ICT) disruptions which are to be supported by key performance indicators and risk metrics. It will also require firms “on a continuous basis, identify all sources of ICT risk…..and assess cyber threats and ICT Vulnerabilities.”[ix]
I could go on, but in short, most operational resilience regulations around the globe are requiring firms to identify their critical business services; understand their dependencies (IT assets, people, buildings, vendors, etc); understand their vulnerabilities; takes necessary steps to ensure they can operate within their stated tolerances; and prove it through scenario testing.
How does cyber risk quantification help?
Okay, I hear you say, so where could cyber risk quantification (CRQ) help?
In almost all cases, cyber threats have been at the forefront of regulators’ thinking. They are not the only potential driver of ICT disruption, but experience shows the impact of cyber threats can be quite widespread and have significant consequences for consumers and for the wider financial system. Therefore, regulated companies will have to get a firm understanding of the susceptibility of their critical business services to cyber threats, as well as be able to demonstrate that they are on top of managing their vulnerabilities to keep risk at an acceptable level. They will also have to demonstrate that they are doing this on an ongoing basis. This is where dynamic CRQ comes in.
For me, the potential uses of a CRQ tool such as Balbix to assist with meeting operational resilience requirements fall into three key areas: visibility, vulnerability management, and risk assessment. There are undoubtedly others, but I believe these are the three main ones.
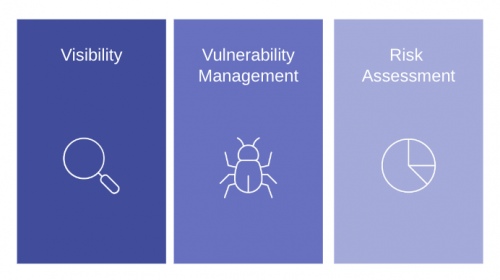
Visibility
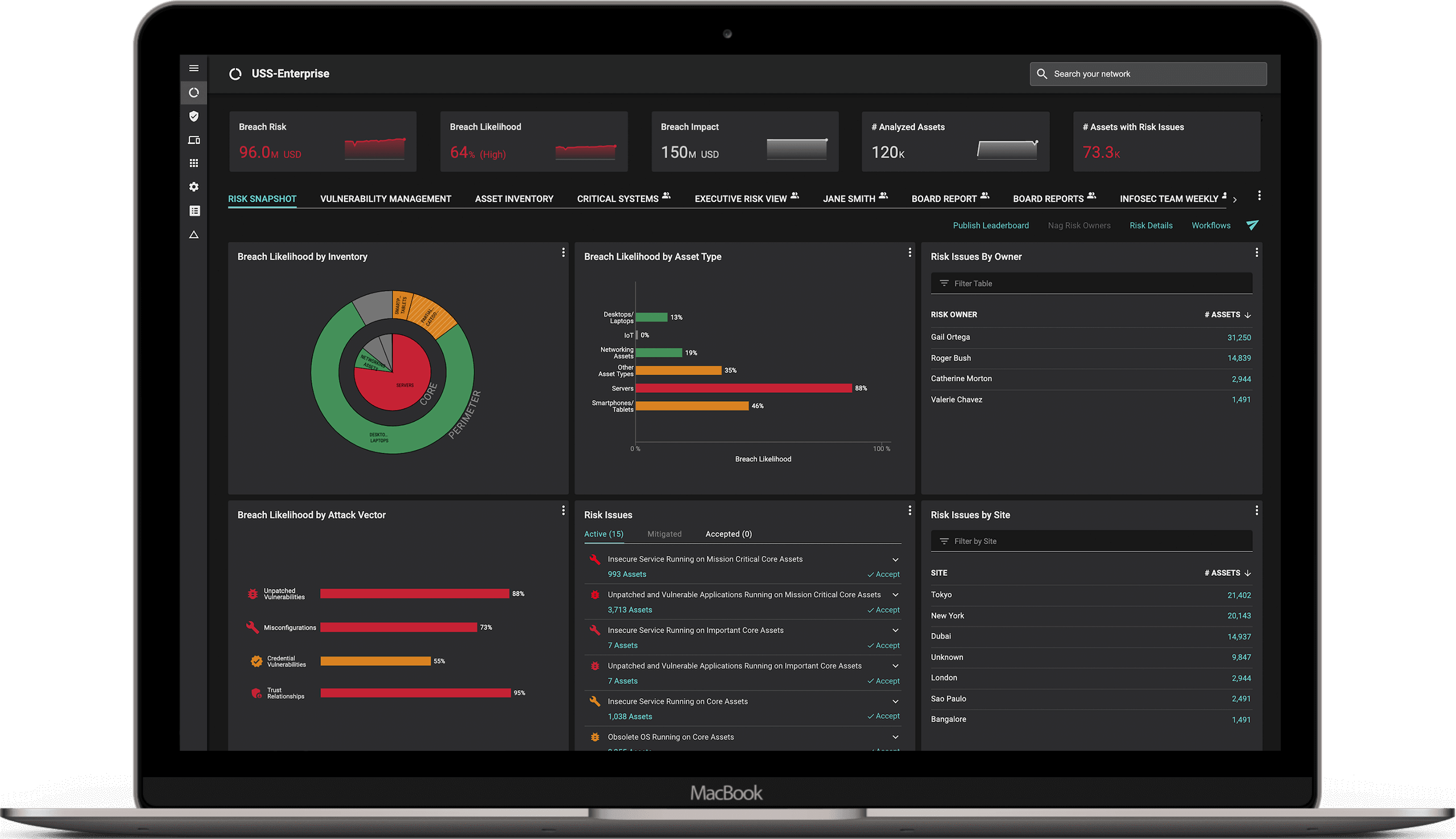
By enumerating the entire IT estate of a firm, CRQ tools like Balbix enable visibility of the complete software and hardware inventory. The inventory is dynamic and continuously updated. When important business services (IBS) information is overlaid on the technical inventory data, then firms are able to demonstrate to regulators that they have full understanding of the IT elements supporting each IBS. This then enables both vulnerability and risk assessments to be completed and reported, not only across the firm, but by each IBS. As solutions like Balbix use continuously observed data, it is always up-to-date.
Vulnerability management
Having established a complete inventory and mapped this to IBS, the vulnerabilities identified within the estate can easily be reported against each service. CRQ solutions are also key to enabling the prioritization of vulnerability remediation, as well as demonstrating that a firm is effective at managing its vulnerabilities to keep its services within stated tolerances.
Risk assessment
CRQ tools such as Balbix, which continuously calculate risk exposure based on observed data in the firm’s ICT environment, are able to track the reduction in risk exposure as vulnerability remediation is completed. This enables the production of a key metric to determine the health of a firm’s ability to manage its vulnerabilities. This metric is what I would describe as mean-time-to-mitigate. It would measure the period of time between the identification of a threat or vulnerability that took the calculated risk exposure above acceptable levels to the reduction of exposure to an acceptable level through closing vulnerabilities. It could become a key benchmarking metric across the organization, or indeed more widely.
A final note
An accurate risk assessment is also key to understanding the susceptibility of a firm’s infrastructure and business services to cyber threats for the CISO, CFO, and the rest of the leadership team. In addition to providing operational and risk likelihood metrics, CRQ solutions like Balbix can also quantify the cost of a breach in dollars (or in other currencies) by calculating the attendant financial impact that could incur. By reporting risk in terms of potential financial exposure, the CISO, CFO, and the rest of the leadership team can discuss cybersecurity risk in the C-suite and with the Board using a common language – hard cash!
[i] APRA consults on new prudential standard to strengthen operational resilience | APRA [ii] dp118.pdf (bankofengland.co.uk) [iii] https://www.bis.org/bcbs/events/icbs20/ws6.pdf [iv] Bank of England – Statement of Policy ‘Operational Resilience – March 2021’ [v] Press release: Basel Committee issues principles for operational resilience and risk (bis.org) [vi] Principles for operational resilience (bis.org) [vii] dp118.pdf (bankofengland.co.uk) [viii] Discussion paper – Strengthening operational risk management | APRA [ix] AG (europa.eu)
*** This is a Security Bloggers Network syndicated blog from Blog – Balbix authored by Paul Kelly. Read the original post at: https://www.balbix.com/blog/operational-resilience-regulations-for-financial-services-the-role-of-crq/





