Aviatrix Distributed Cloud Firewall Streamlines App Security
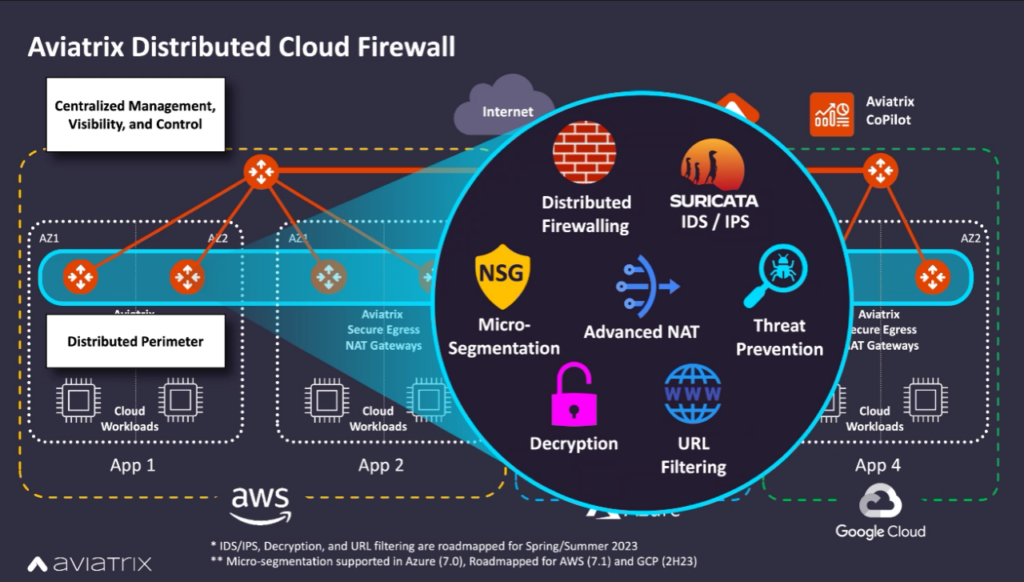
Aviatrix today made generally available a Distributed Cloud Firewall (DCF) that programmatically pushes and enforces cybersecurity policies for cloud computing environments via a central console.
Rod Stuhlmuller, vice president of solutions marketing for Aviatrix, said DCF is unique in that cybersecurity teams can now inspect traffic and enforce policies wherever application traffic naturally flows. In contrast, other centralized approaches to cybersecurity often require organizations to reroute traffic to specific firewalls to inspect it before policies are applied, he noted.
DCF also makes it possible to isolate networks, implement microsegmentation, translate network addresses and enforce role-based access controls (RBAC) in addition to automated threat detection and mitigation, anomaly detection, vulnerability scanning, workload risk scoring, Layer 7 decryption and inspection and audit reporting, said Stuhlmuller.
Aviatrix’s programmable approach also makes it simpler to create policies based on identity tags and attributes versus a static IP address, he added. That’s critical because modern microservices-based applications are continuously updated in ways that dynamically generate new IP addresses with each update, said Stuhlmuller. In comparison, legacy monolithic applications are updated less frequently, so applications’ IP addresses are generally more static.
Attempting to lift and shift firewalls—that were originally designed to be deployed on hardware or on top of a virtual machine running in an on-premises IT environment—to the cloud is fundamentally inefficient, added Stuhlmuller. DCF provides an approach that scales better and is simpler to manage while also reducing the total cost of securing a cloud computing environment. Aviatrix DCF was designed from the ground up to be natively employed in cloud computing environments rather than being bolted on, he added.
Through a central console, DCF also abstracts away the low-level tasks that would otherwise need to be performed when attempting to enforce zero-trust policies across a highly distributed computing environment made up of multiple clouds, said Stuhlmuller.
As more application workloads are deployed in the cloud, organizations of all sizes will need to evaluate their approach to securing them. Many of these organizations are under pressure to significantly reduce the total cost of cybersecurity during uncertain economic times without compromising application security, noted Stuhlmuller.
In the meantime, cybersecurity teams will need to come to terms with emerging cloud-native applications built using containers, Kubernetes clusters and serverless computing frameworks. The rate of change for these applications will be significantly higher than legacy applications, so the probability a cybersecurity mistake will be made during updates is much greater. More challenging still, many cloud-native applications are much more latency-sensitive, so there’s little tolerance for any overhead created by the platforms and tools used to secure them.
As such, there’s a critical need for an approach to securing all the diverse types of applications deployed in cloud computing environments. In fact, repurposing techniques and technologies used to secure on-premises IT environments in the cloud is likely to have suboptimal results.