
Vulnerability Found In Spam Protection, AntiSpam, FireWall Plugin
Overview
A SQL-injection vulnerability was discovered in the WordPress plugin called “Spam protection, AntiSpam, FireWall by CleanTalk” could expose user emails, passwords, credit-card data and other sensitive information to an unauthenticated attacker.
A full disclosure of the vulnerability was completed on March 5th, 2021. The versions of the plugin that had the vulnerability was lower than 5.153.4. The plugin has now been patched. The plugin was installed on more than 100,000 sites, and was mainly used to weed out spam and trash comments on website discussion boards. The vulnerability (CVE-2021-24295) which carried a high-severity CVSS vulnerability rating of 7.5 out of 10, raised due to a fault on how it performed filtering. The plugin maintains a blocklist and tracks the behavior of different IP addresses, including user-agent strings those browsers send to identify themselves.
Functionality
CleanTalk is an all-in-one antispam solution for WordPress that protects login, comment, contact and WooCommerce forms at once. You don’t need to install separate antispam plugins for each form. It allows a blog to work faster and save resources. CleanTalk is a transparent antispam tool, that provides detailed stats of all incoming comments and logins.
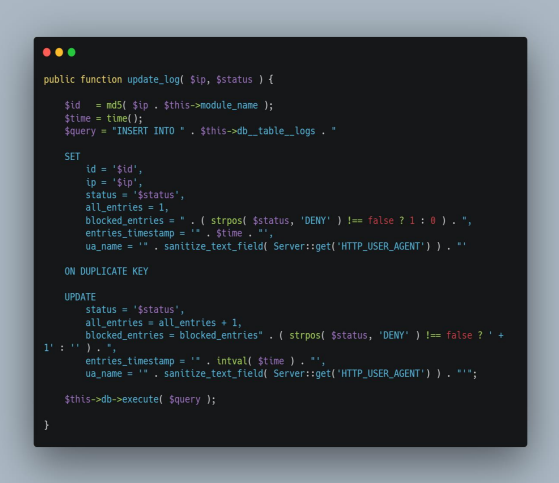
Unfortunately, the update_log function in the file structure lib/Cleantalk/ApbctWP/Firewall/SFW.php file is used to insert records of these requests into the database and failed to use a prepared SQL statement.
Vulnerable Code:
Deployment Methods:
By design, the update_log function should only have been executed a single time for each visitor IP address. However, it was possible to manipulate the cookies set by the plugin on the browser, sending an initial request to obtain a ct_sfw_pass_key cookie and then manually setting a separate ct_sfw_passed cookie and disallowing it from being reset. For example, a request might ask the database if the first letter of the admin user’s email address starts with the letter ‘e,’ and instruct it to delay the response by five seconds if this is true, and then try guessing the next letters in sequence. This would a time-based SQL injection attack and can be used in this case.
The vulnerable SQL query uses INSERT rather than SELECT. Since data was not being inserted into a sensitive table, the INSERT query could not be used by an attacker to exploit the site by changing values in the database, and this also made it difficult to retrieve any sensitive data from the database. Finally, the SQL statement used the sanitize_text_field function in an attempt to prevent SQL injection, and the User-Agent was included in the query within single quotes.
During a normal SQL injection, bad actors can simply read text as it is returned. However, when attackers are unable to retrieve information from a database server, they will often employ time-based SQL injections to achieve their results. This works as the operation can take long periods of time (intervals) for the attack to take place.
Time-based SQL injections are commonly used when determining if vulnerabilities are present on a web application or website, as well as in conjunction with Boolean-based techniques during Blind SQL injections. This exploit could be used by unauthenticated visitors to steal user email addresses, password hashes, and other sensitive information. Cybersecurity researchers were able to successfully exploit the vulnerability in ClearTalk via the time-based blind SQLinjection technique.
Conclusion
According to the Common Vulnerability Scoring System the vulnerability was scored a 7.5 rating. The vulnerability has since been patched in version 5.153.4, however it is highly recommended that users update to the latest version of the plugin, 5.156 immediately. If you are using this WordPress plugin, make sure you have the latest version to avoid this vulnerability, or if you are currently using it and believe you may have been exposed to the vulnerability, contact SiteLock today and let us help get your website back on track.





