Detecting security threats on your network can be difficult, but what about detecting threats in your cloud environment?
Augusto Barros, Vice President of Solutions at Securonix, presented at SecureWorld New England 2021 on the challenge of detecting threats in the cloud.
The challenge of detecting threats in the cloud
Threat detection tools before the cloud focused primarily on networks, endpoints, and logs. But as Barros explained in his session, significant changes are underway.
"The difference now is that we are in fact far more exposed where there are a lot of pieces, when there are many components of our IT infrastructure that are exposed in a way that they never have been before. And I believe that the perfect example of that are the S3 buckets.
But if you make a single mistake in the configuration of that S3 bucket, you may be exposed to the internet, kind of with just one incorrect configuration statement or just one click."
He also discussed how the cloud brings other challenges that IT and security professionals must face:
"The cloud environments also brought a lot of new APIs to set it up. And also the concept of infrastructure as code. So a lot of changes to your infrastructure, they used to be physical. And I've seen that the real physical sense of the word are now done by codes. And I like to use this analogy of you setting up a router, or even kind of a firewall in the physical, kind of with direct physical access, where you're bringing a laptop, you're connected a serial cable.
I bet that many people in the audience here maybe have never seen a serial cable before, but you will connect the cable to the console port on the device, and you will set that up directly beside the device. When you're operating with cloud assets, you may be setting up something like a firewall, entirely using code."
Another challenging aspect of the cloud is that there has been wide adoption of software as a service, with things like Office365, Salesforce, and ServiceNow. This has become especially true this year with the pandemic and everyone working from home and accessing internal servers. So now, no part of the data flow passes through your typical controls.
So, how does this effect threat detection?
There are a few different IT resources to monitor, which may not be visible to some traditional monitoring practices. The telemetry available is different, including data types, collection methods, locations, and volume. You may even need extra telemetry. And as new threats emerge, new threat detection content is required with new skills and better analytics.
Cloud security tools
Barros continued in his session to talk about security tools you need for the cloud. This includes data from endpoints, networks, and logs, and that the cloud can cover all three of these.
However, you will also need some capabilities associated to those data sources, such as data collection, data enrichment, data storage, search, and analytics.
Here is a breakdown of current cloud visibility and security tools:
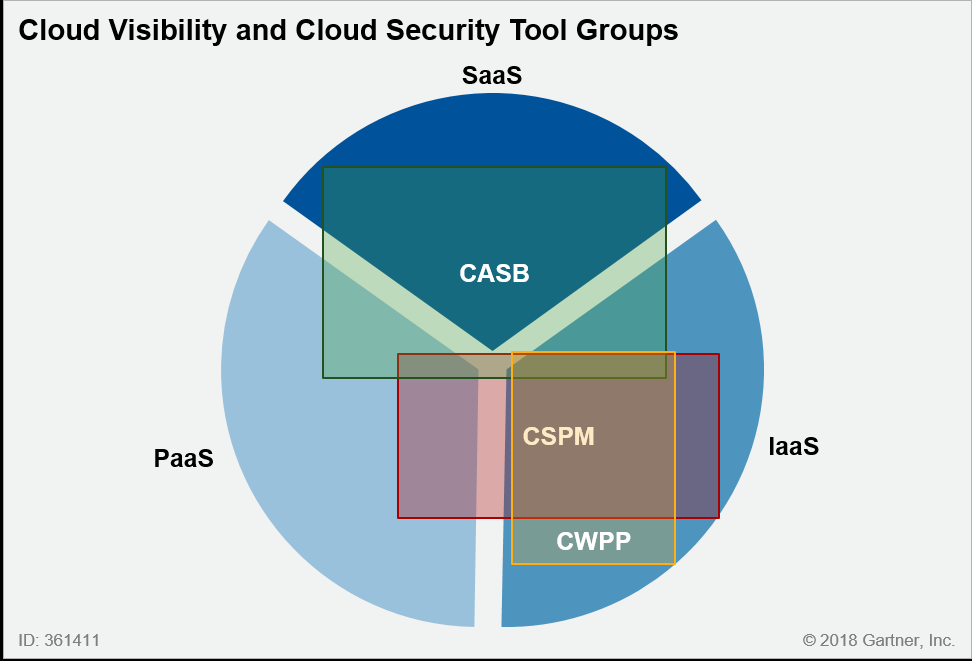
Cloud Access Security Broker (CASB)
Cloud Security Posture Management (CSPM)
Cloud Workload Protection Platform (CWPP)
Barros points out that monitoring the cloud from outside the cloud is not practical, as data transfers can be costly, bandwidth can become a limitation, and many cloud oriented tools simply do not have an "on prem" delivery option.
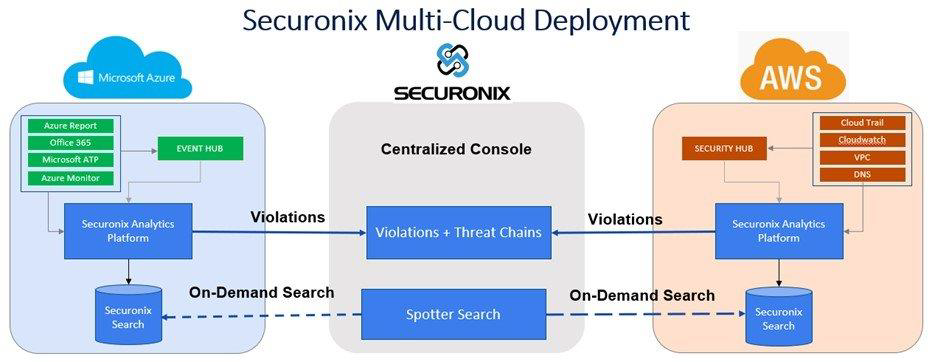
But what about multi-cloud?
Securonix offers a multi-cloud deployment, broken down in in this chart below:
If you want to watch Augusto Barros' session in its entirety, SecureWorld New England is available on-demand and you can go back and listen to him discuss detecting threats in the cloud, as well as many more security topics from our other speakers.





